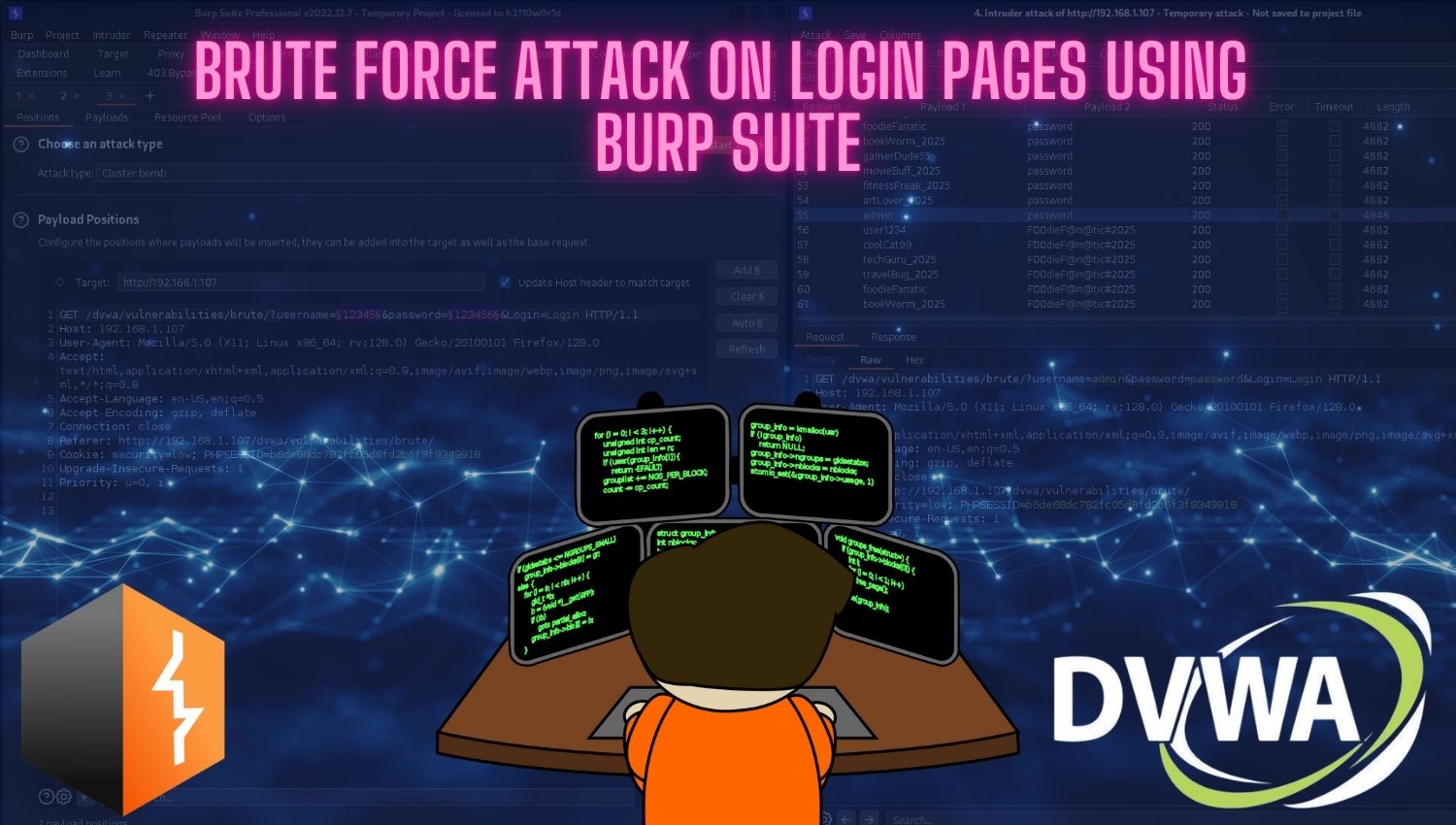
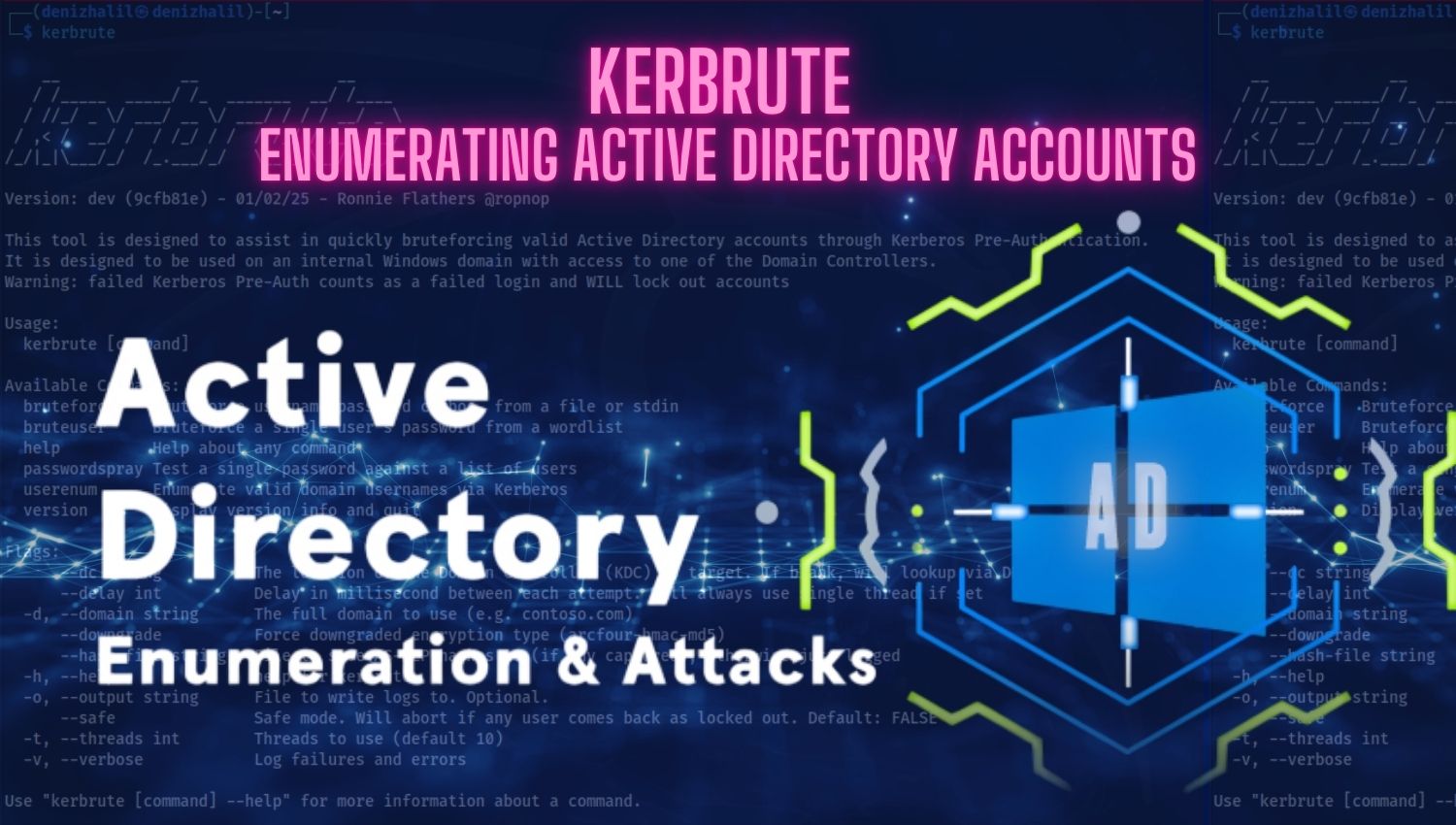
Linux Security Auditing with Lynis
Introduction In today’s digital world, system security has become more critical than ever with the rise of cyber attacks. The Linux operating system is widely used in many different environments, including servers, desktops, and embedded systems. Therefore, ensuring the security of Linux systems is of critical importance. This is where Lynis comes in. Lynis is an open-source security auditing tool developed for Linux, macOS, and Unix-based