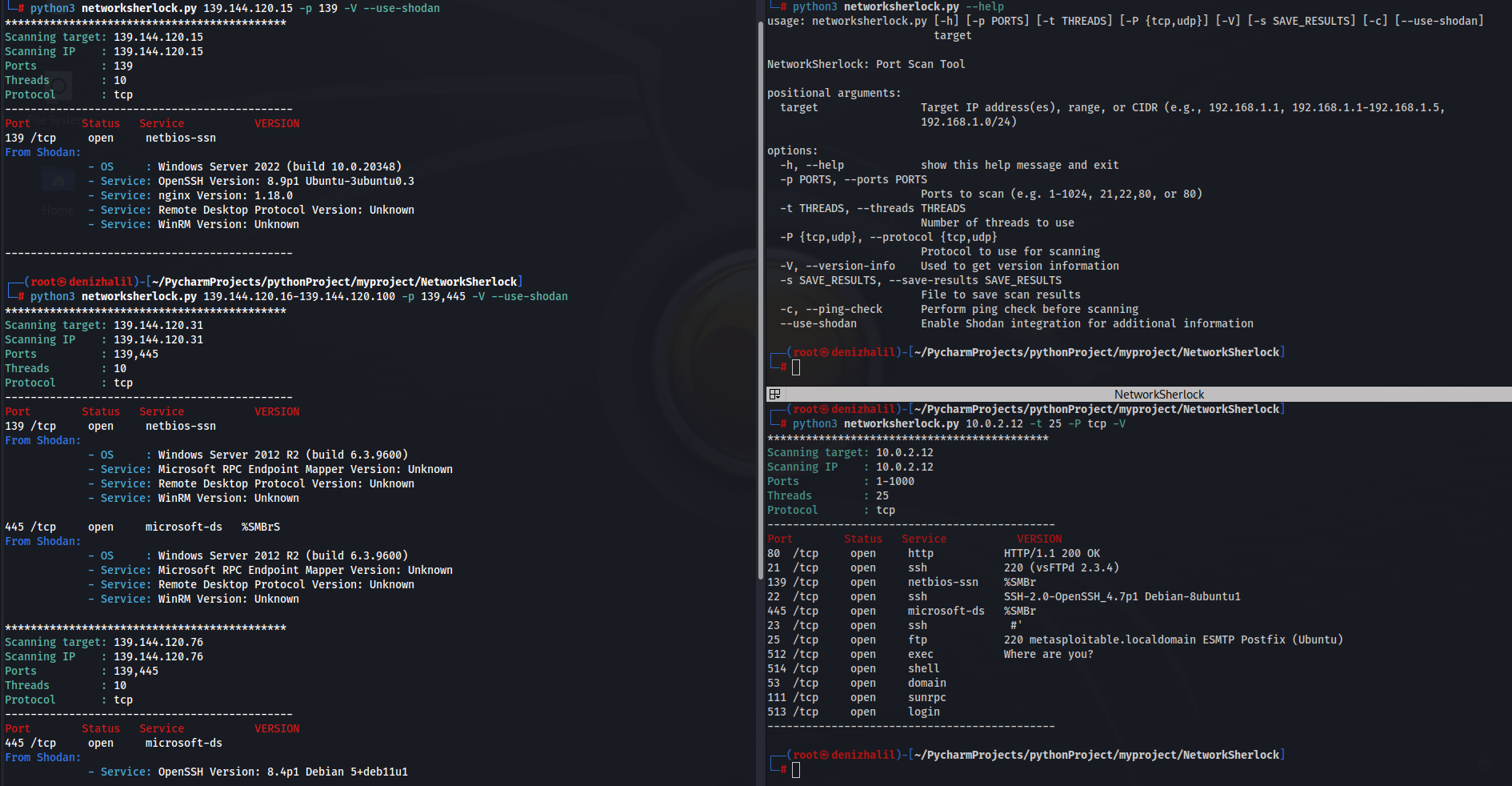
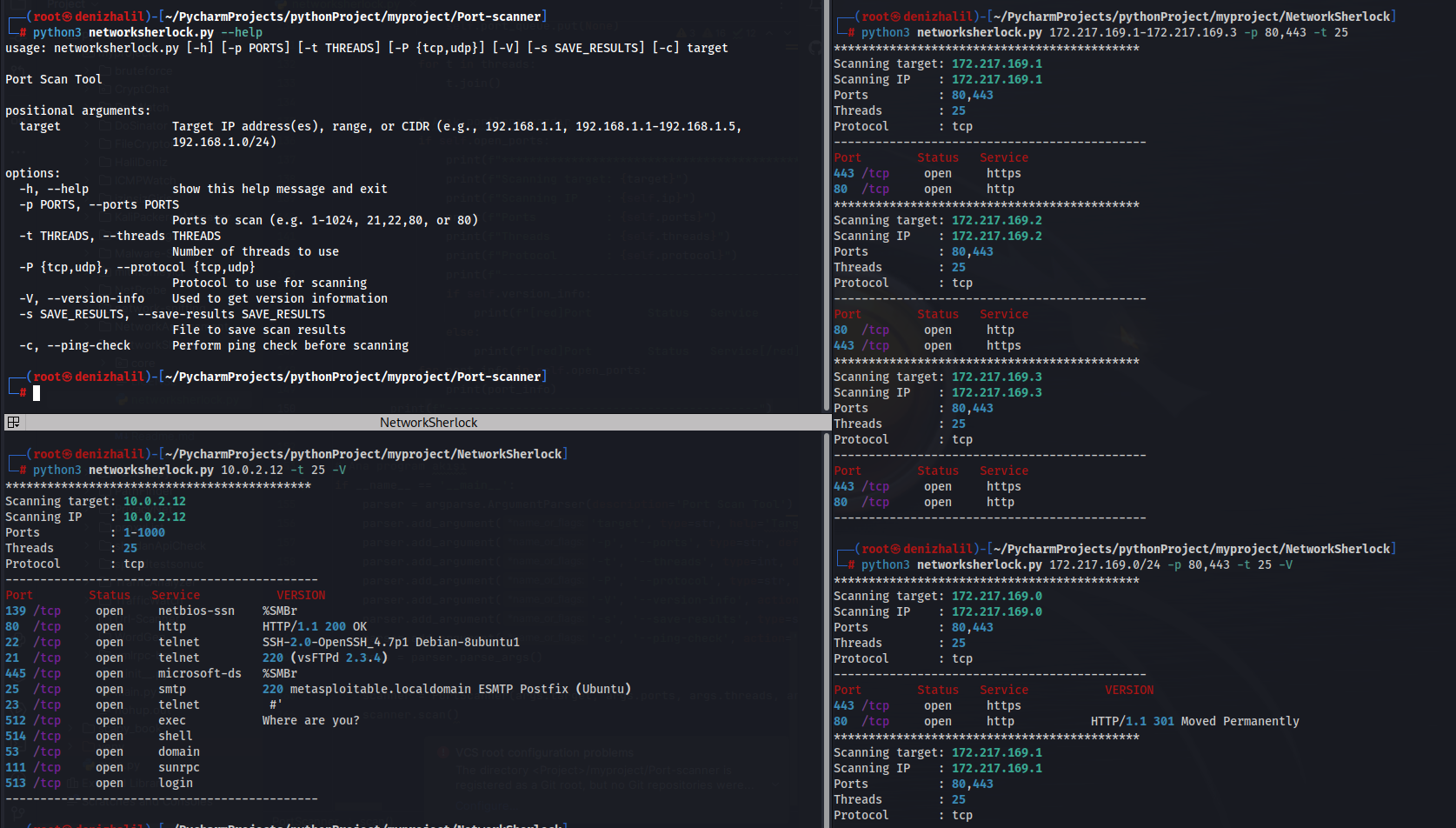
Popular Tools Used in Penetration Testing
Introduction In today’s rapidly evolving digital landscape, cybersecurity has emerged as a paramount concern for individuals and organizations alike. With the increasing frequency and sophistication of cyberattacks, including data breaches, ransomware, and other malicious activities, it is essential to adopt proactive measures to safeguard sensitive information. One of the most effective strategies for identifying and mitigating potential security vulnerabilities, using popular penetration