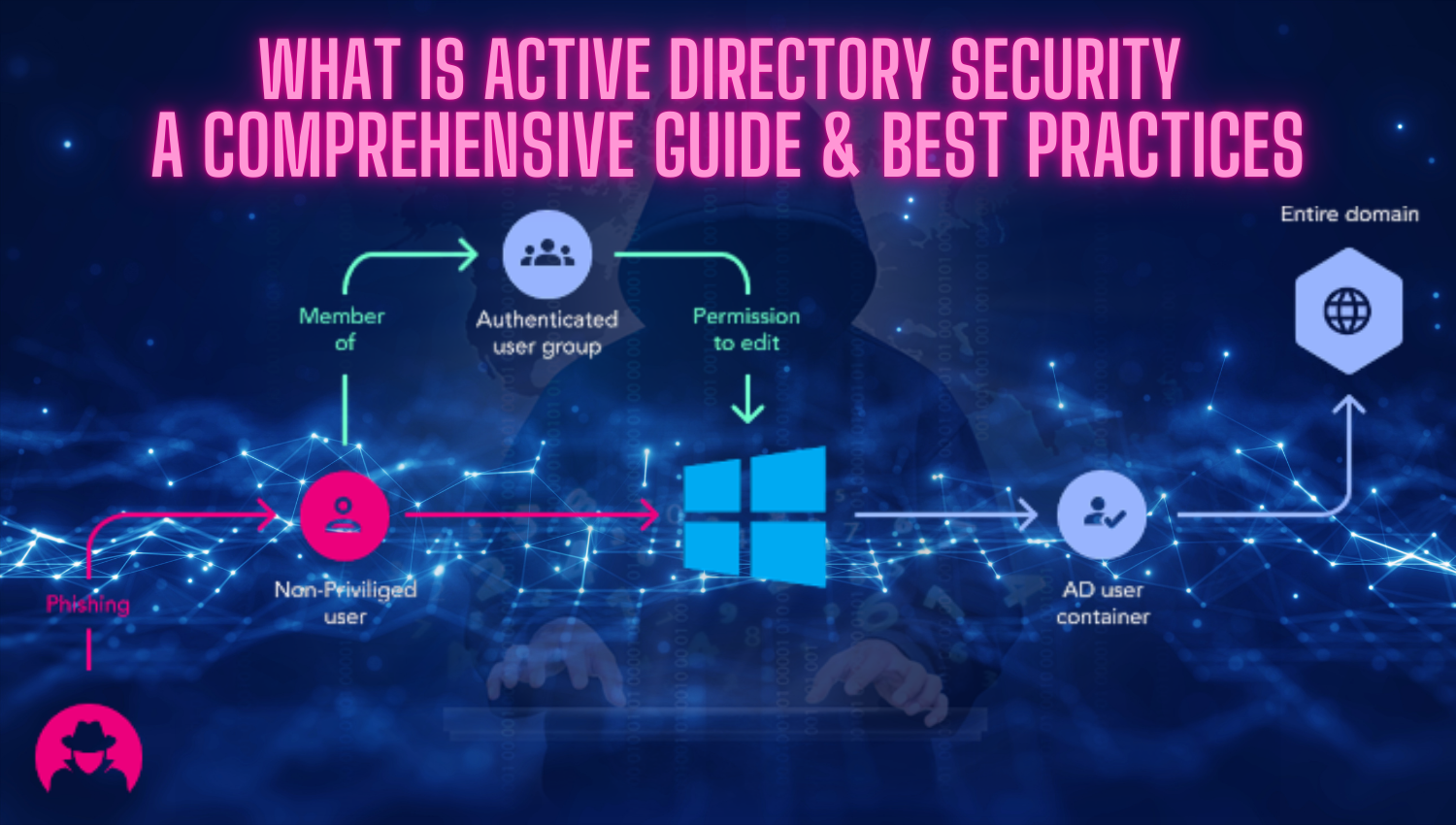
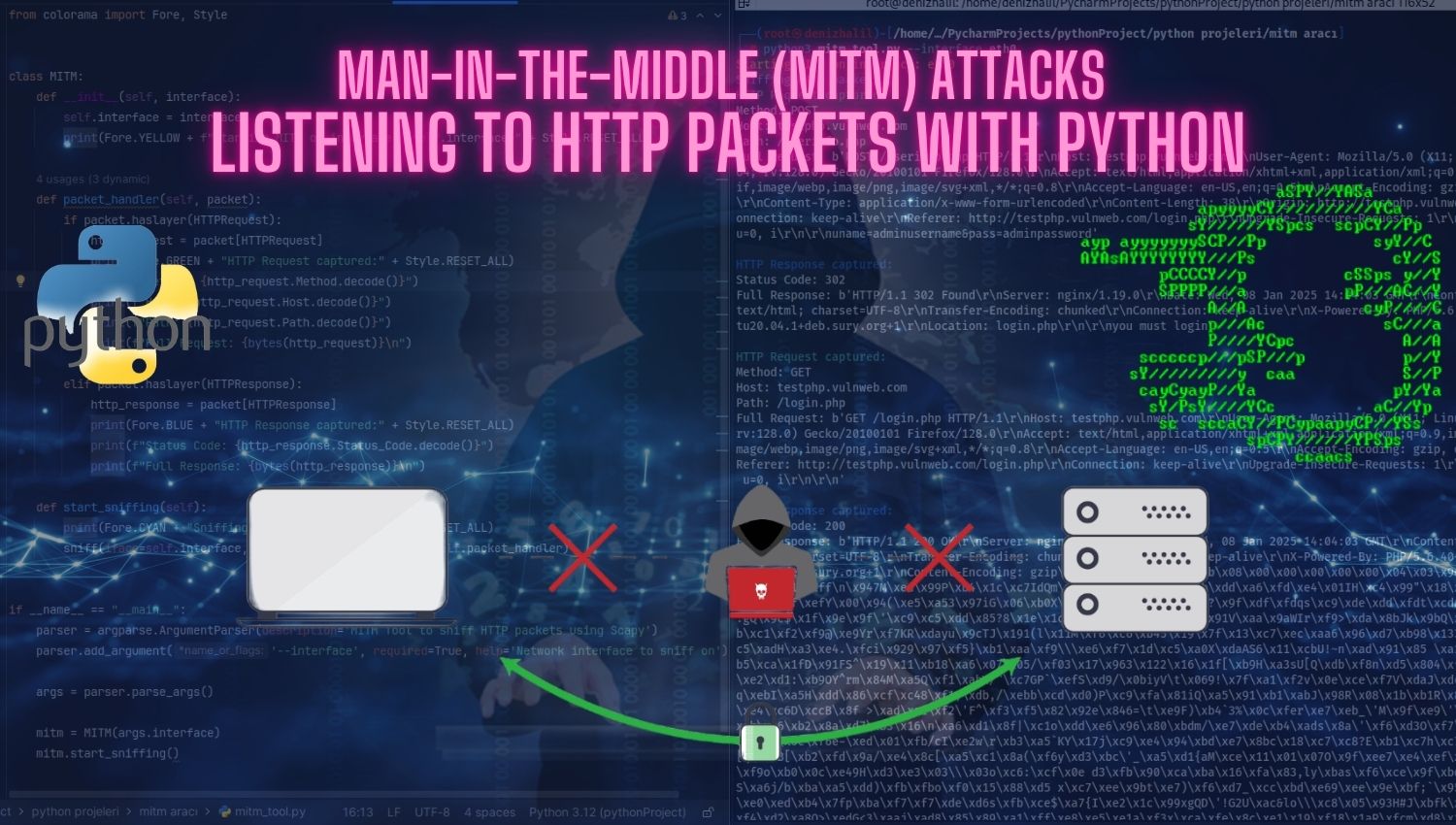
Password Sniffing with Msfconsole: An In-Depth Guide
Introduction In today’s digital landscape, information security is paramount. Networks are complex highways transporting sensitive data, making their protection a critical concern. This article provides an in-depth look at password sniffing, a potent capability within the Metasploit Framework (msfconsole). Password sniffing involves intercepting usernames, passwords, and other sensitive information by monitoring network traffic. However, it’s crucial to remember the ethical and legal implications. Unauthorized password sniffing can