Session Hijacking and Ethical Hacking: Detecting and Preventing
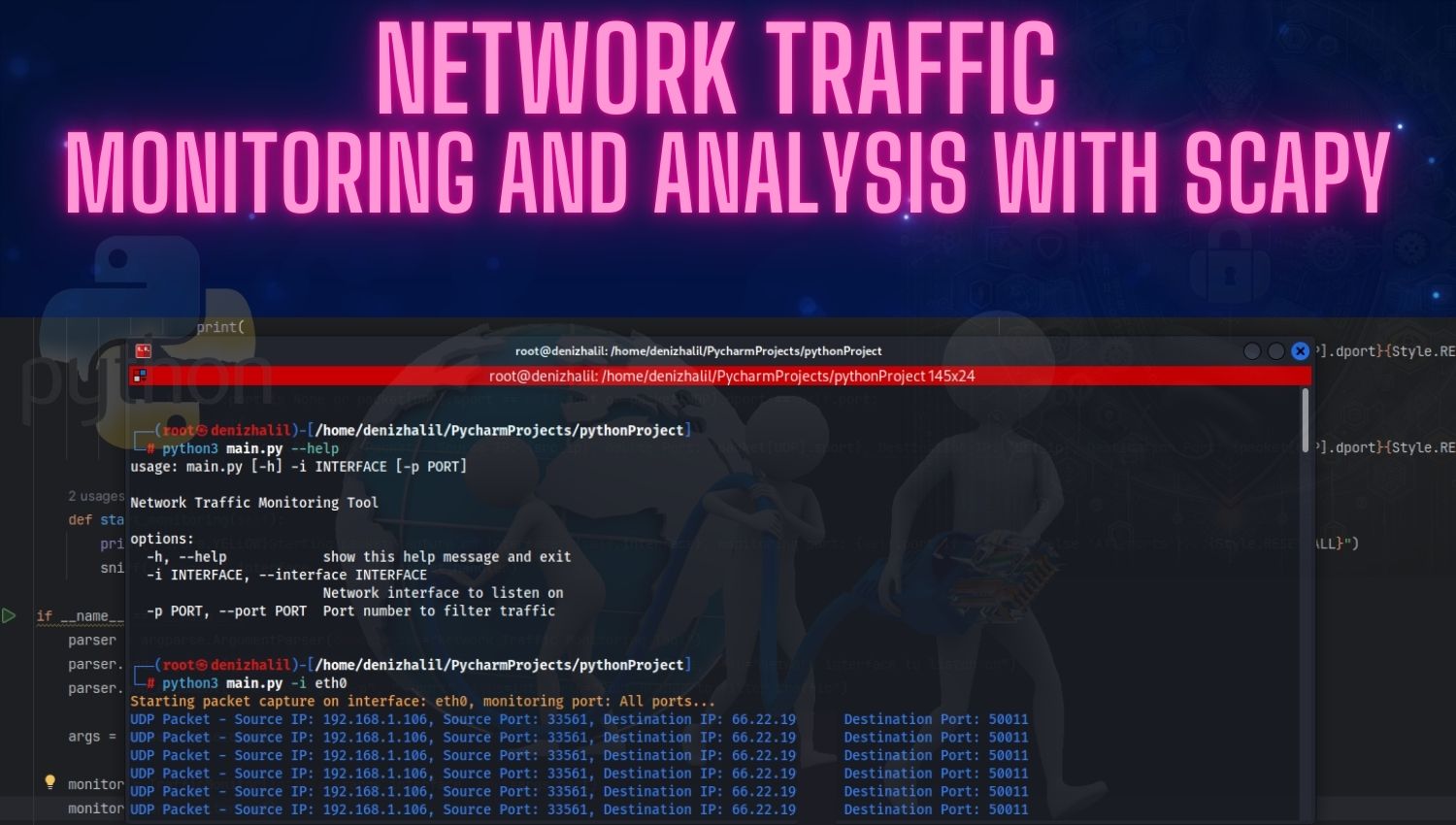
Introduction Session hijacking is a significant threat in the cybersecurity world, capable of causing substantial damage. Attackers gain unauthorized access to a user’s session by capturing session tokens. This type of attack can lead to identity theft, data breaches, and even financial losses in web applications that handle sensitive information, such as banking and e-commerce platforms. Ethical hackers use various techniques to