What You Need to Know About Ransomware Protection in 2025
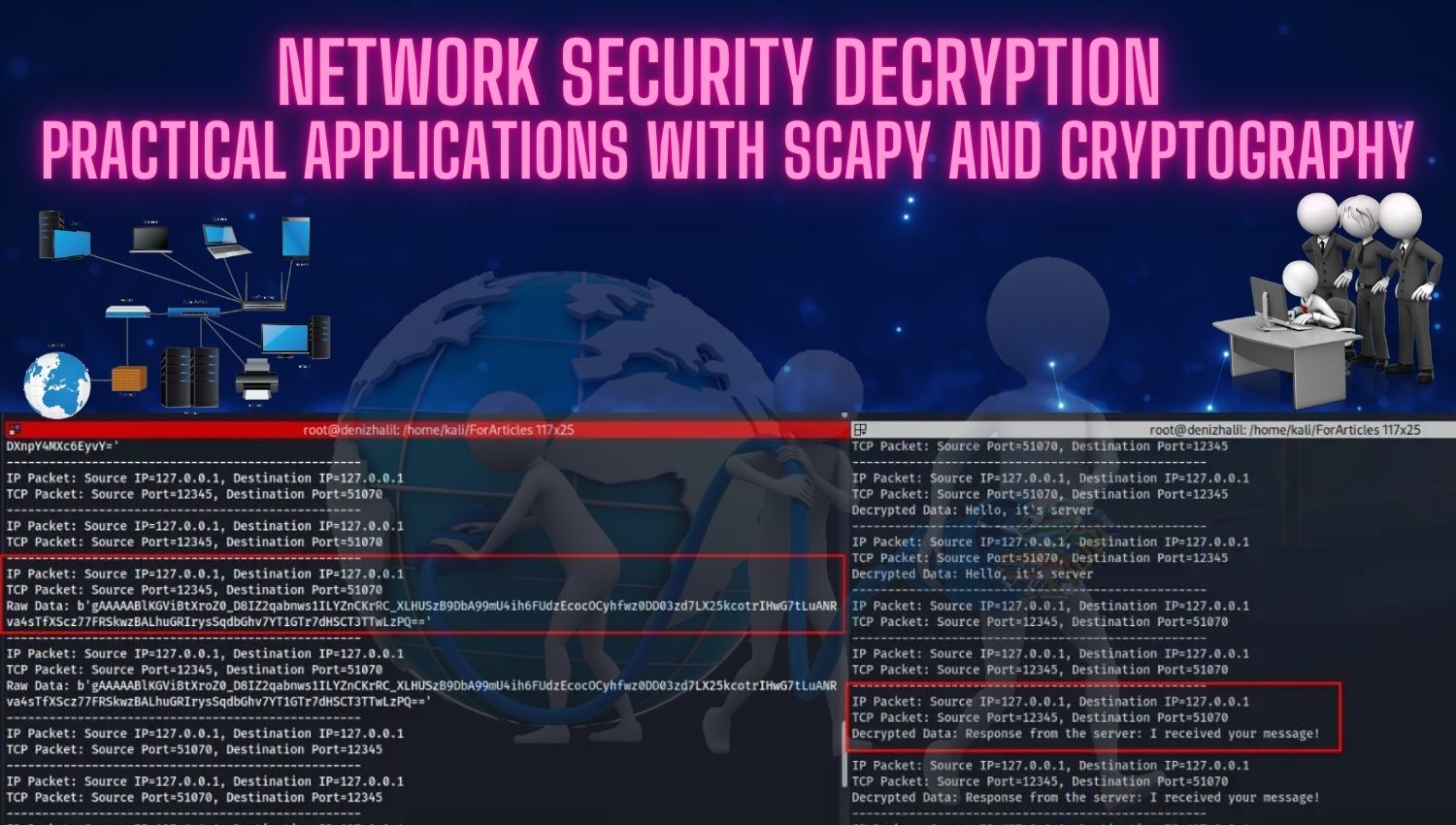
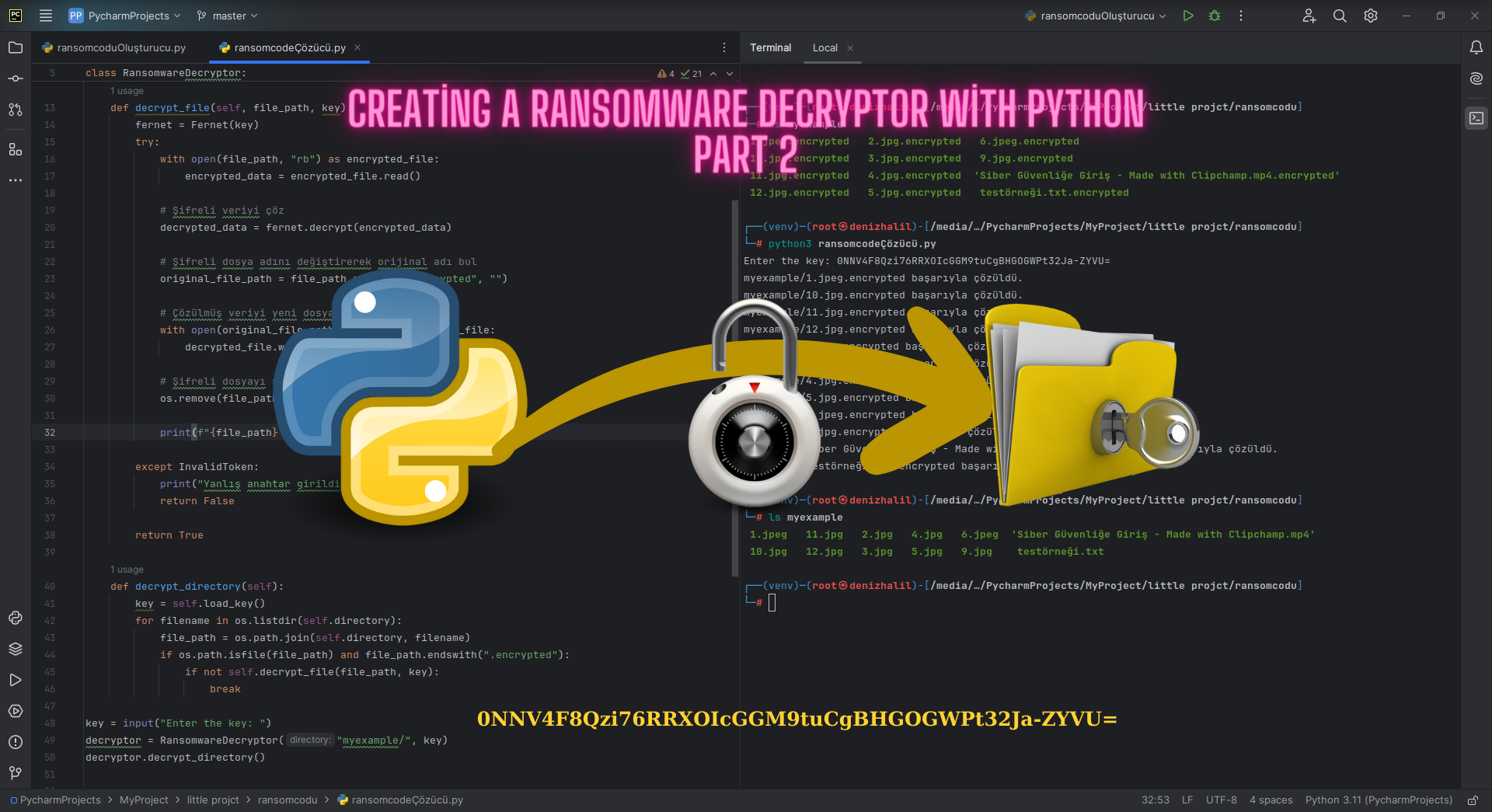
Introduction As digital transformation accelerates and more aspects of our personal and professional lives move online, the threat landscape continues to evolve at an unprecedented pace. Ransomware attacks, in particular, have emerged as one of the most pervasive and damaging forms of cybercrime, targeting everyone from individuals and small businesses to large enterprises and critical infrastructure. In 2025, attackers are leveraging increasingly