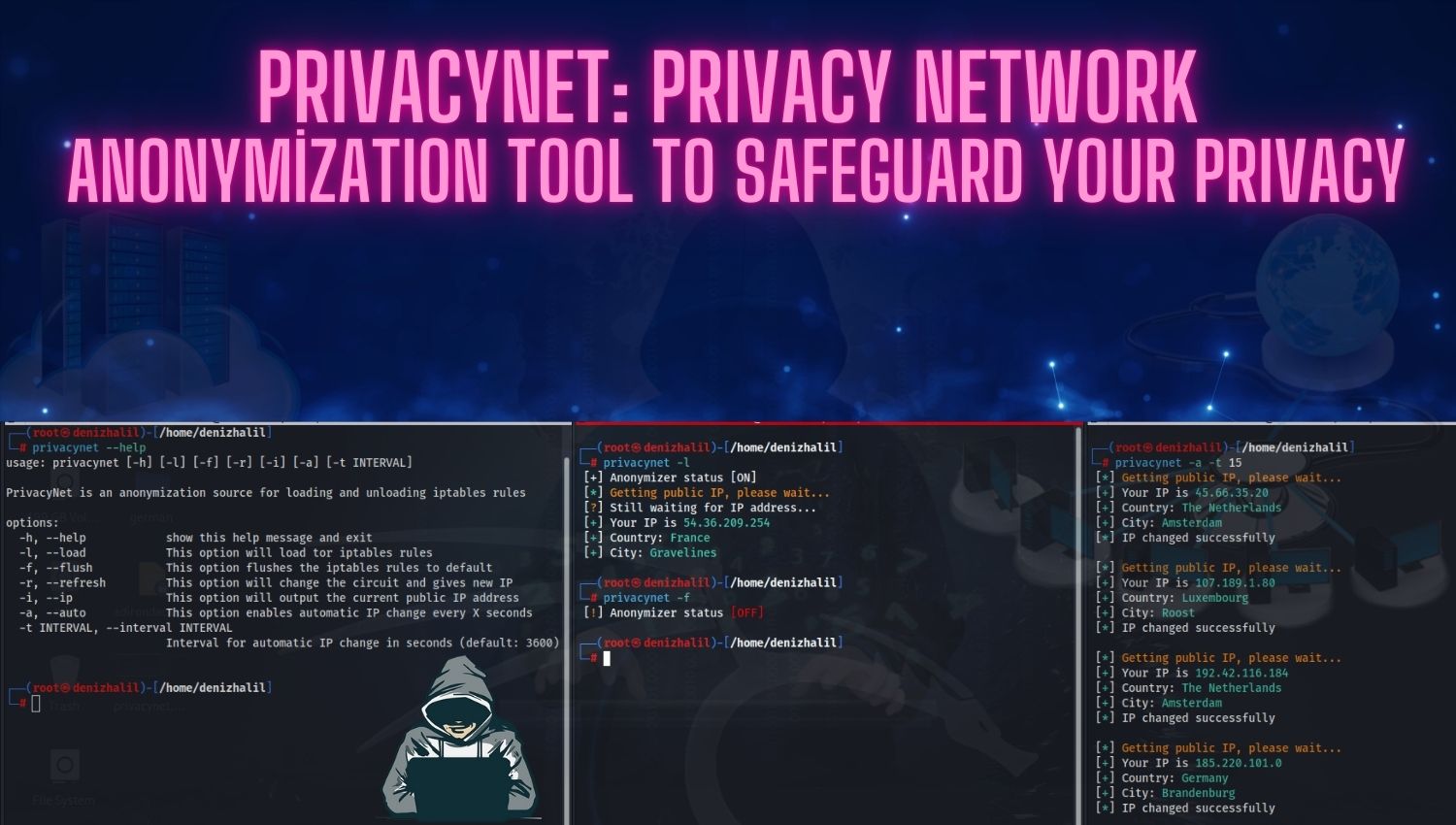
Advanced-Level Cybersecurity Certifications: Elevate Your Expertise
Introduction: As the field of cybersecurity continues to evolve rapidly, advanced-level certifications have become crucial for professionals looking to deepen their expertise and progress in their careers. These certifications are designed for those with existing industry experience and are valuable steps toward achieving higher-level roles. Before diving into advanced certifications, it’s beneficial to familiarize yourself with foundational certifications that