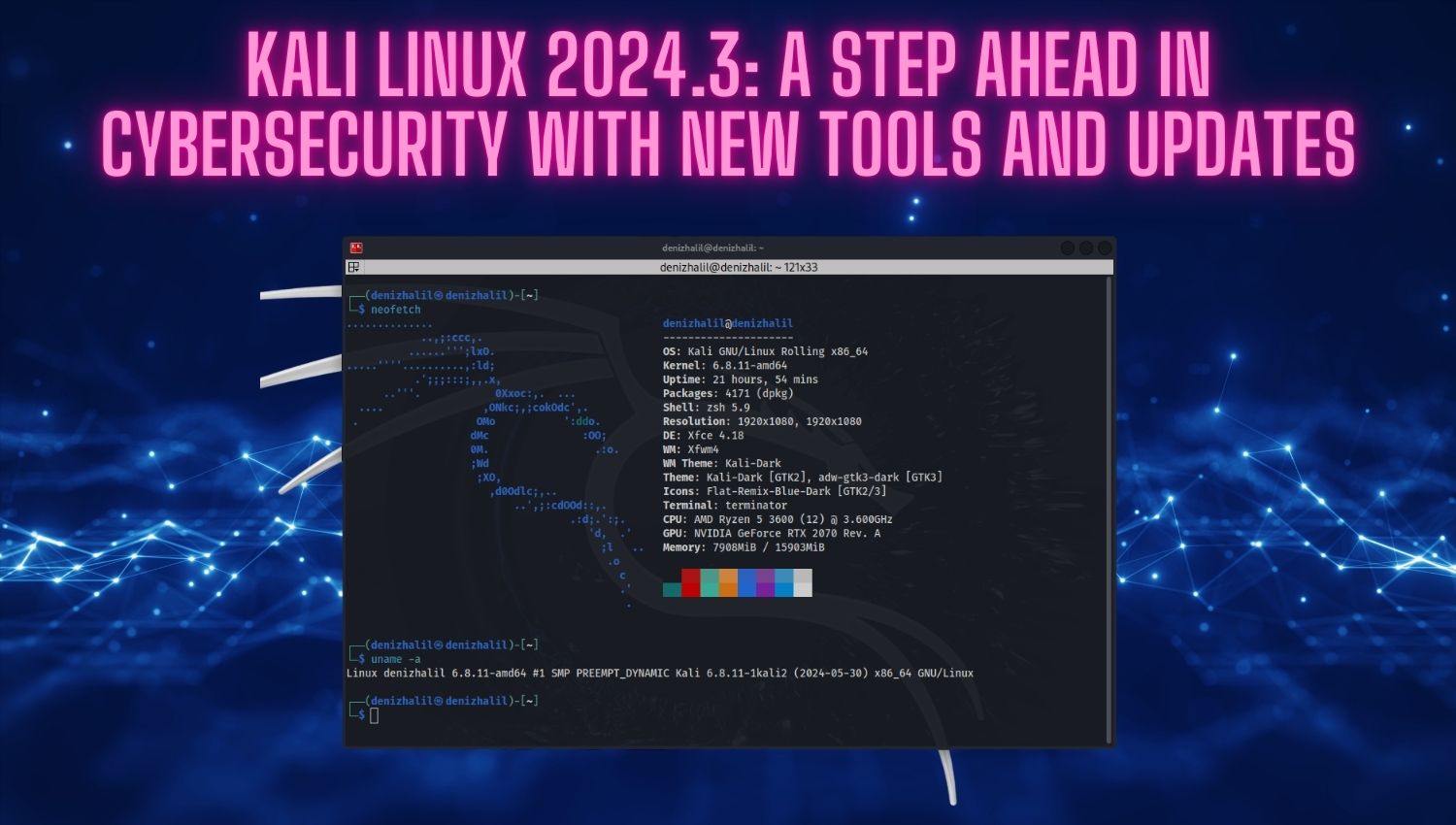
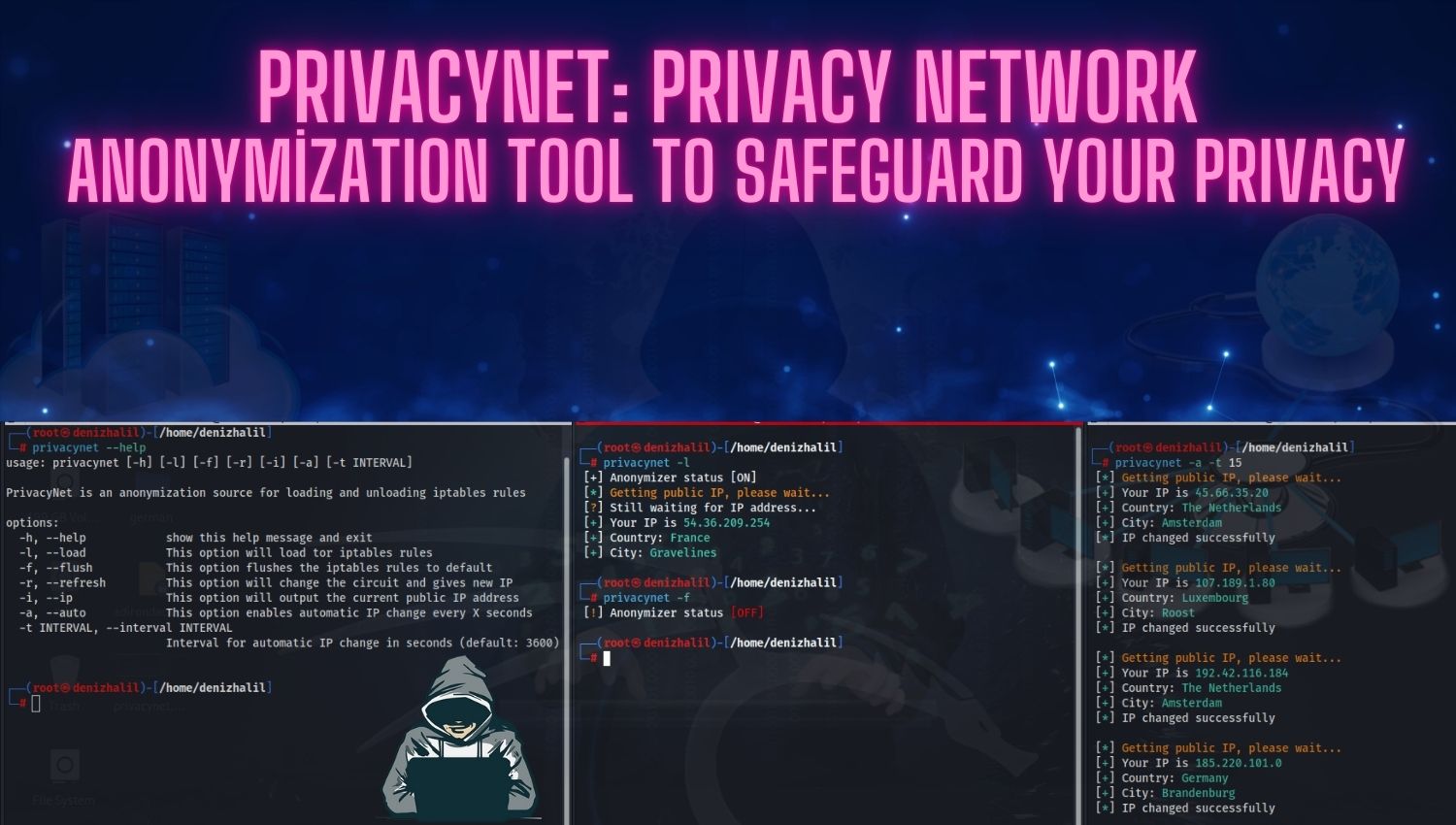
What is Penetration Testing: An effective Security Vulnerabilities approach
Introduction In today’s rapidly digitizing world, the importance of data security has never been greater. As cyber threats become increasingly sophisticated, organizations must adopt more effective strategies to safeguard their information. Cyberattacks can lead not only to significant financial losses but also to severe damage to an organization’s reputation. In this context, penetration testing (pentesting) plays a crucial role. It is an authorized simulated