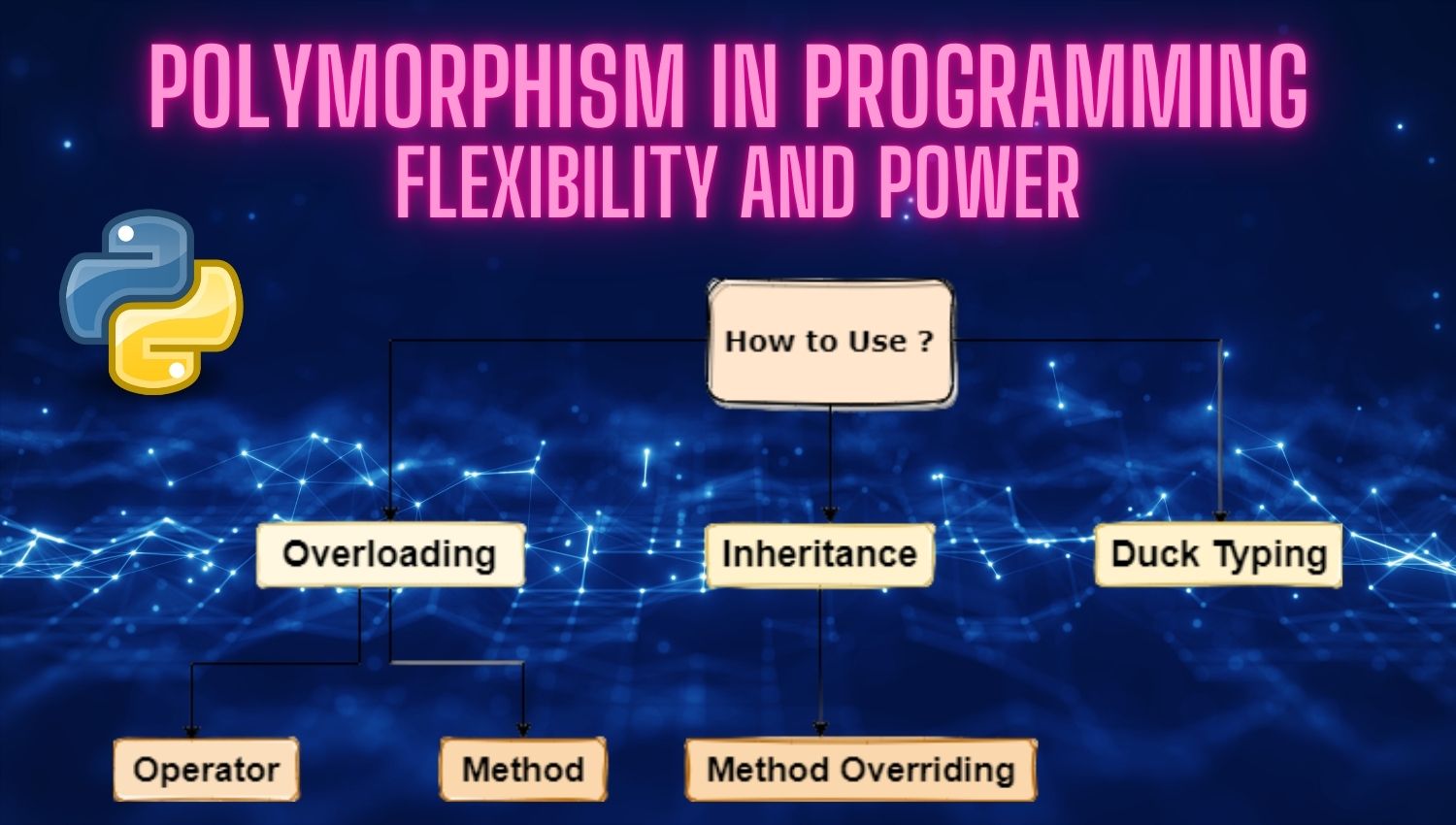
Database Management with Python and a Project Example
Introduction In today’s world, data lies at the heart of technology, and the management of this data plays a critical role in almost every sector. Database management is vital for organizing, storing, and making data accessible. In this article, we demonstrate how to effectively manage databases using Python, one of the world’s most popular programming languages. Python Database Management is an excellent choice for