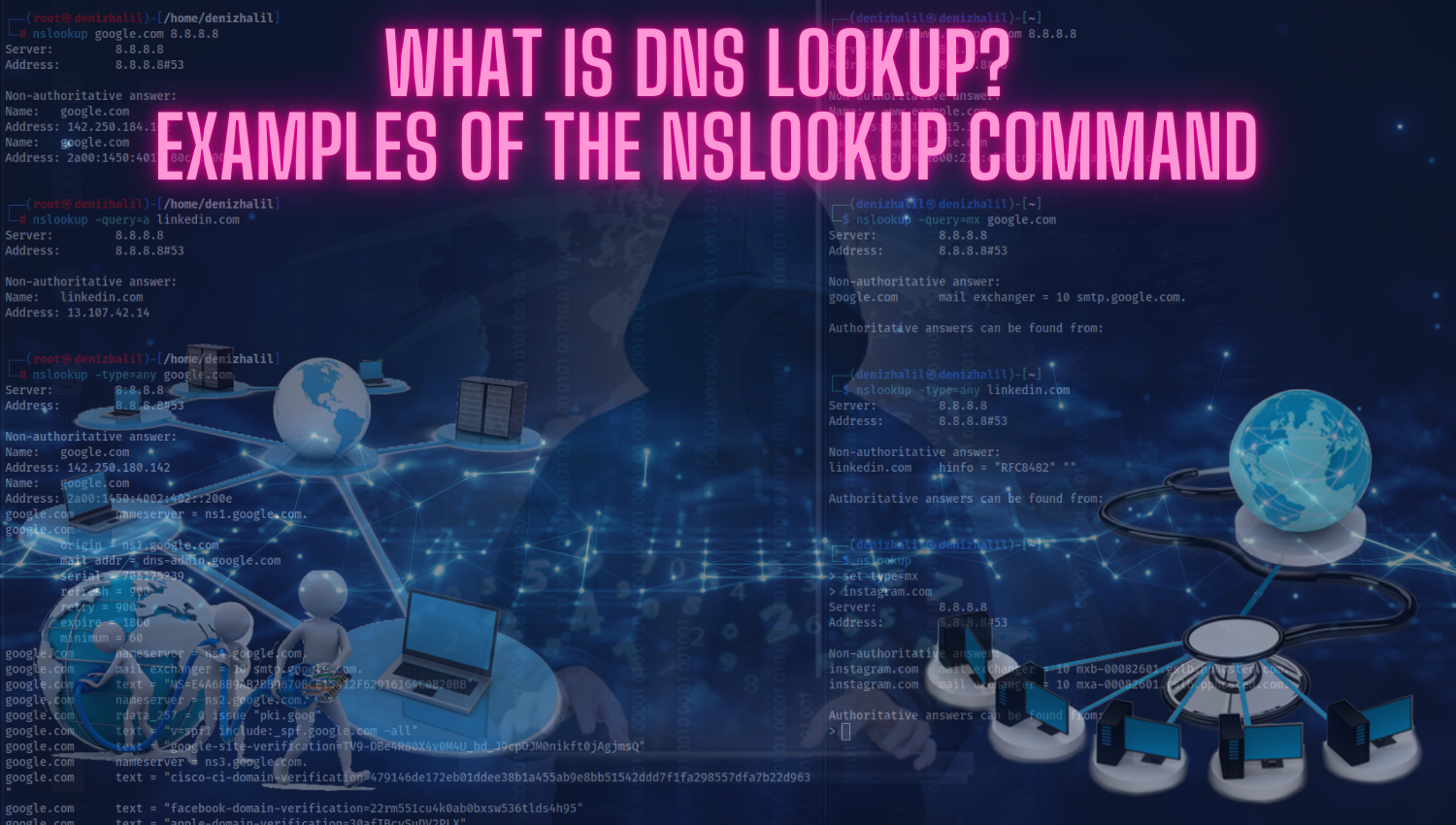
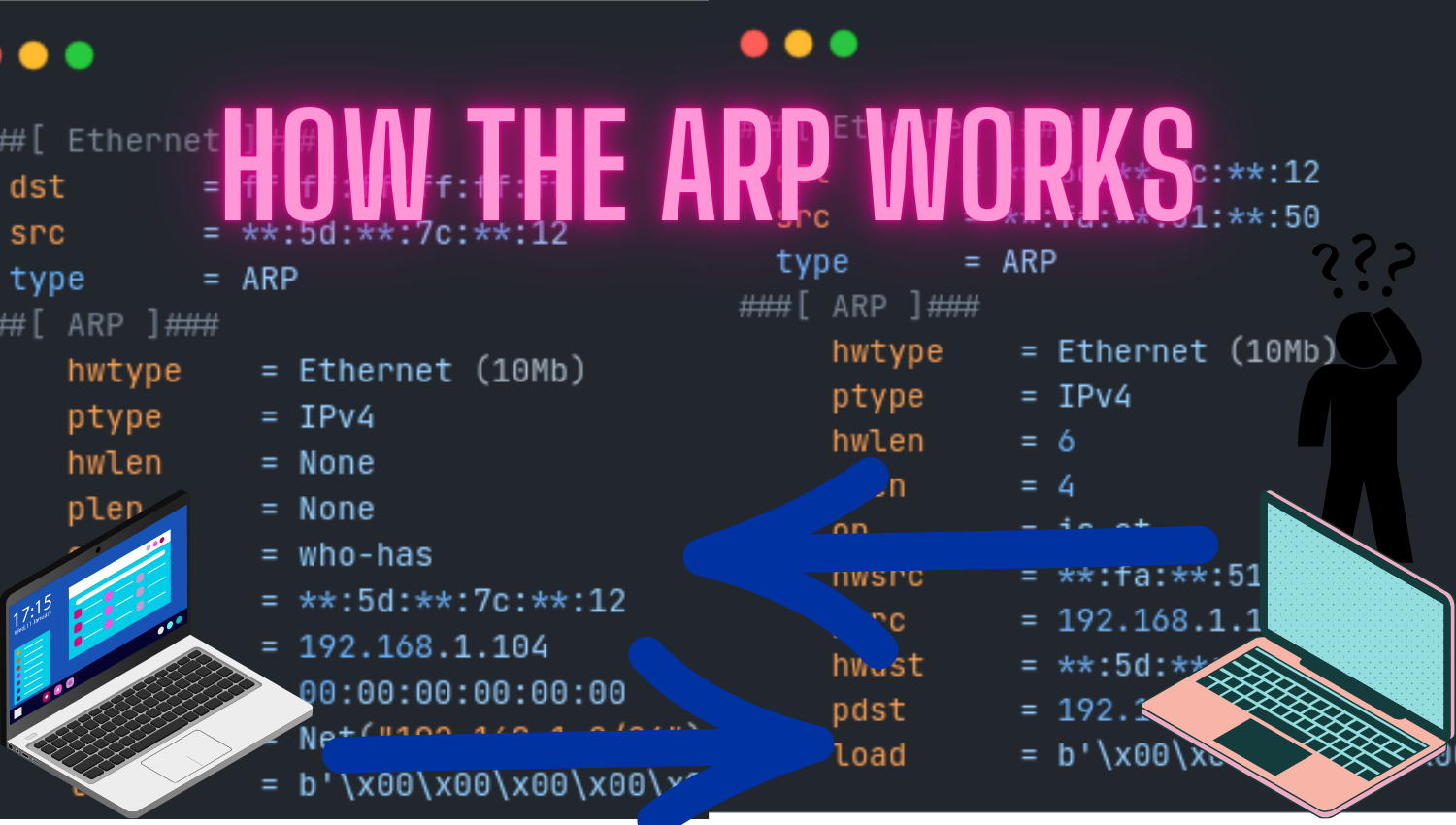
What is DNS Lookup? and Examples of the nslookup Command
Introduction One of the fundamental building blocks of the internet is the Domain Name System (DNS), which plays a critical role in simplifying our access to websites. DNS translates domain names into IP addresses, facilitating communication between humans and computers. This technology, which we use daily, ensures seamless browsing on the internet. In this article, we will explore what DNS lookup is, how it works, and