Subdomain Takeover Vulnerabilities and Prevention
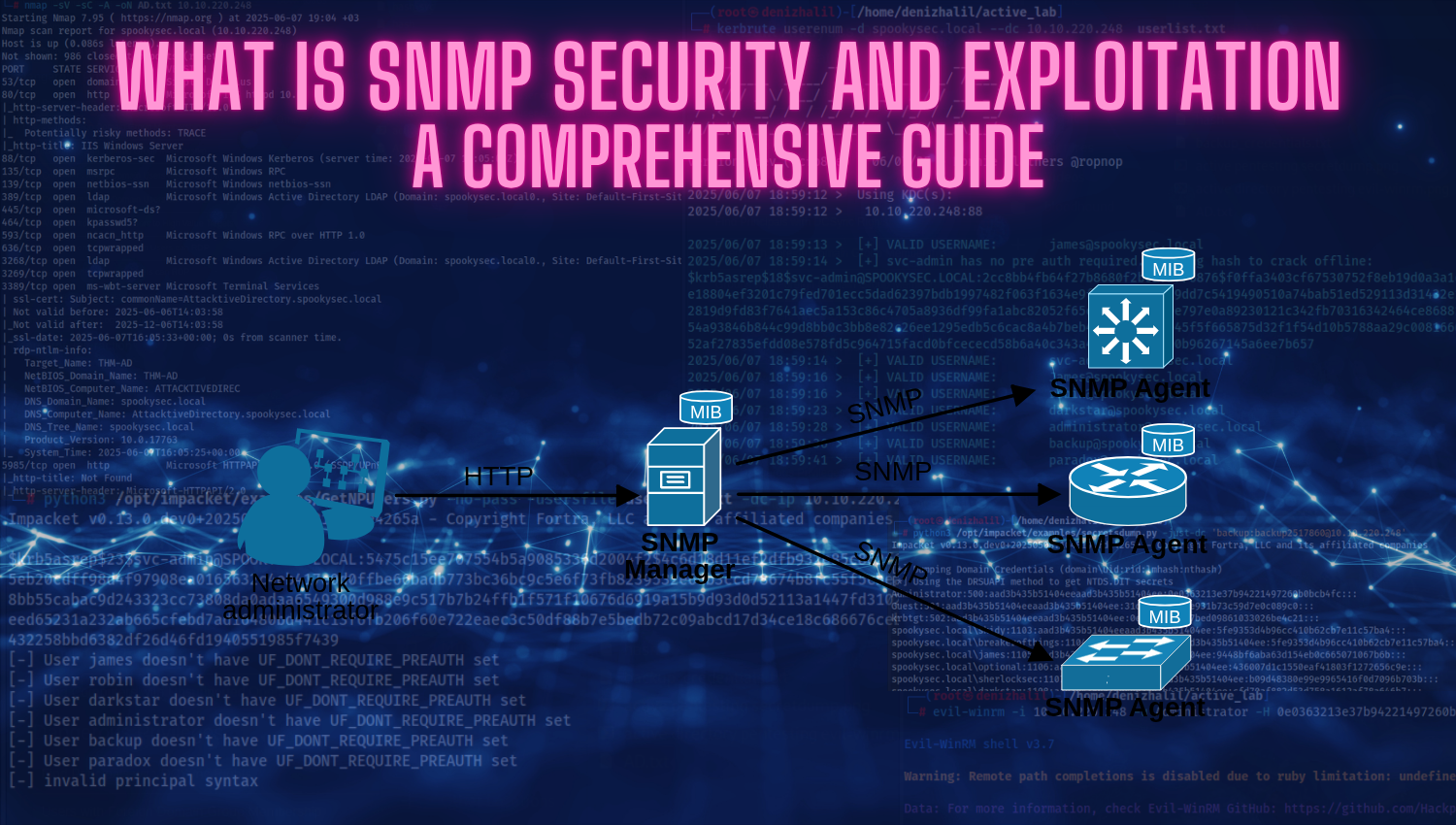
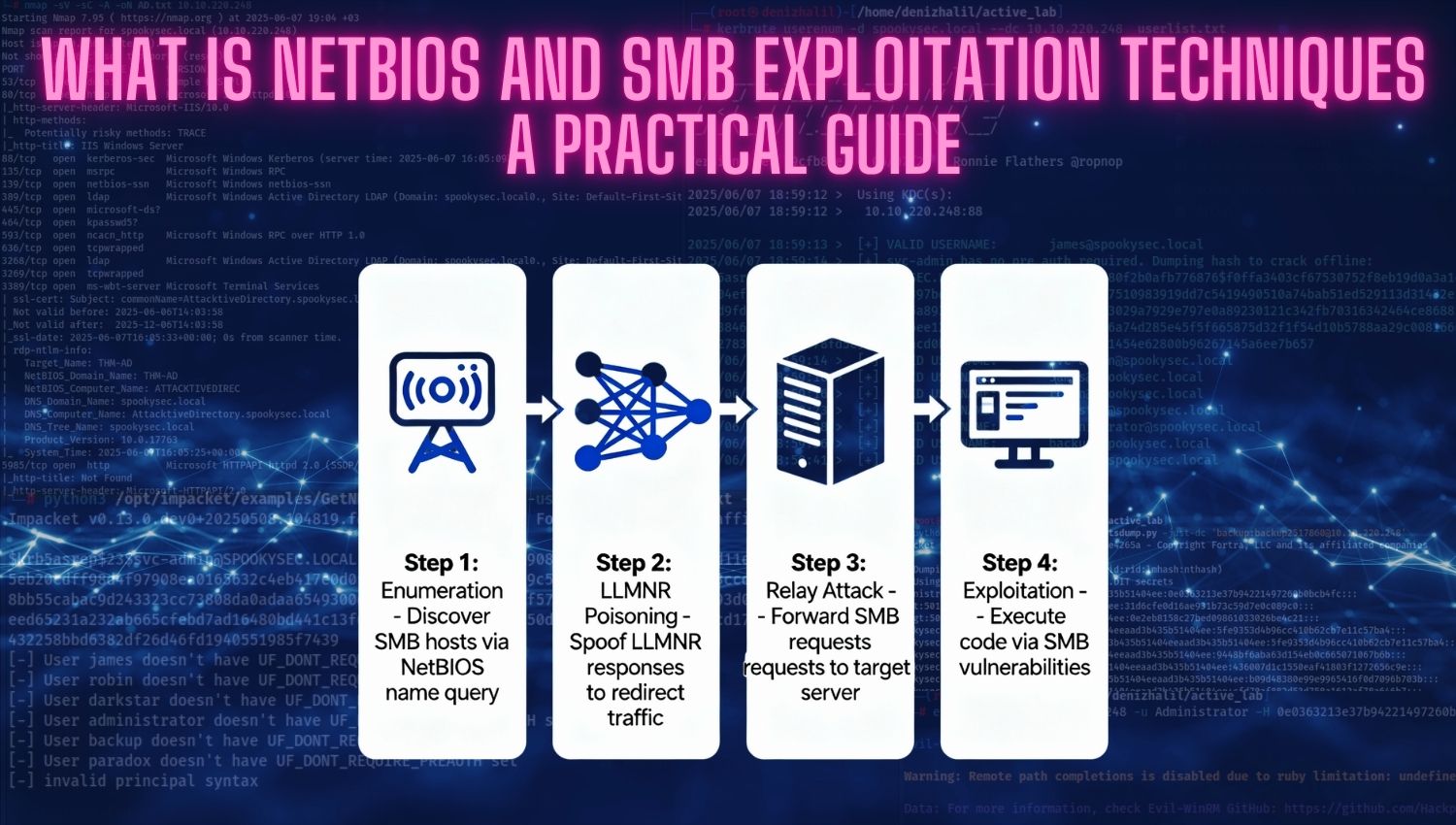
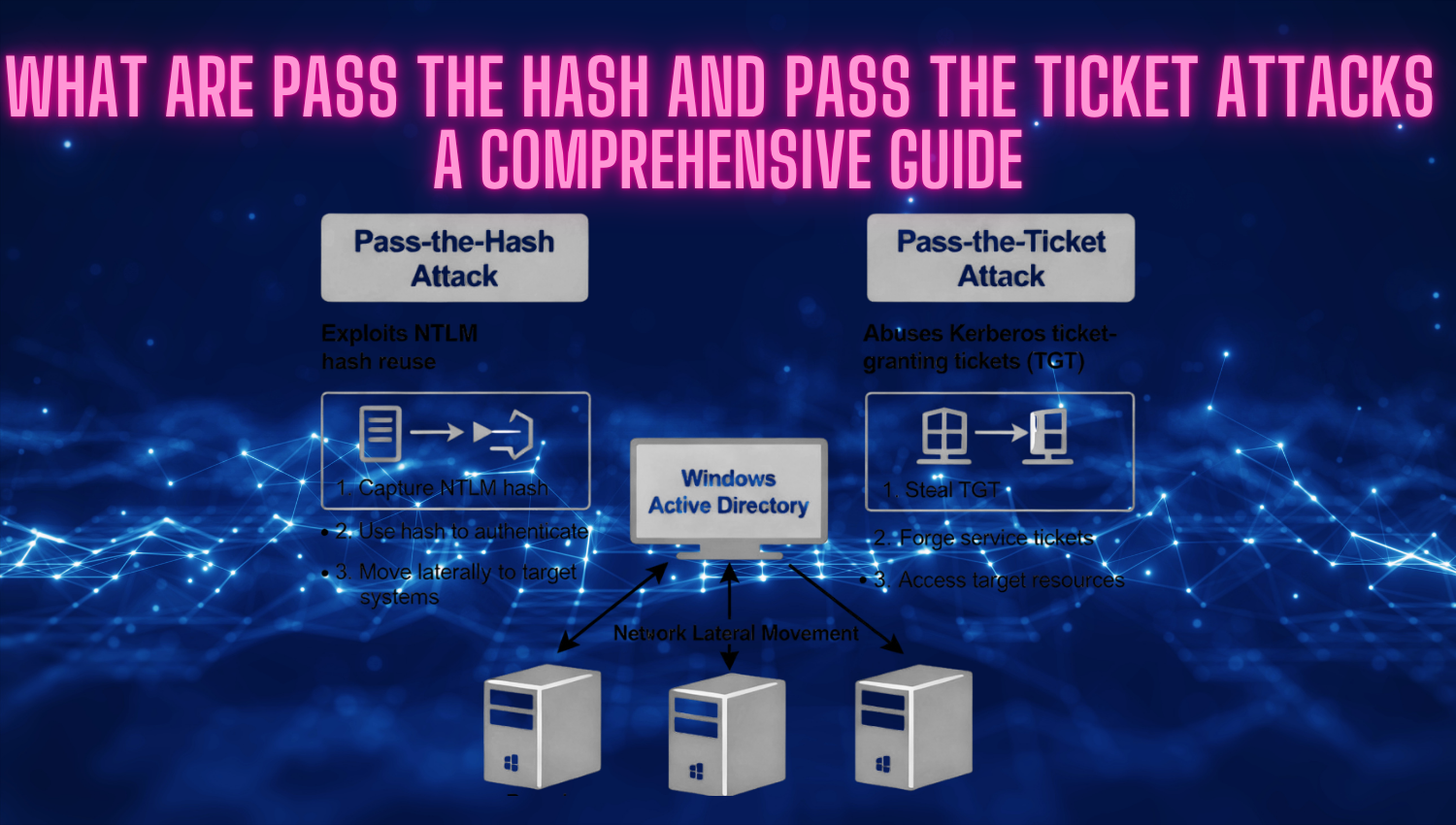
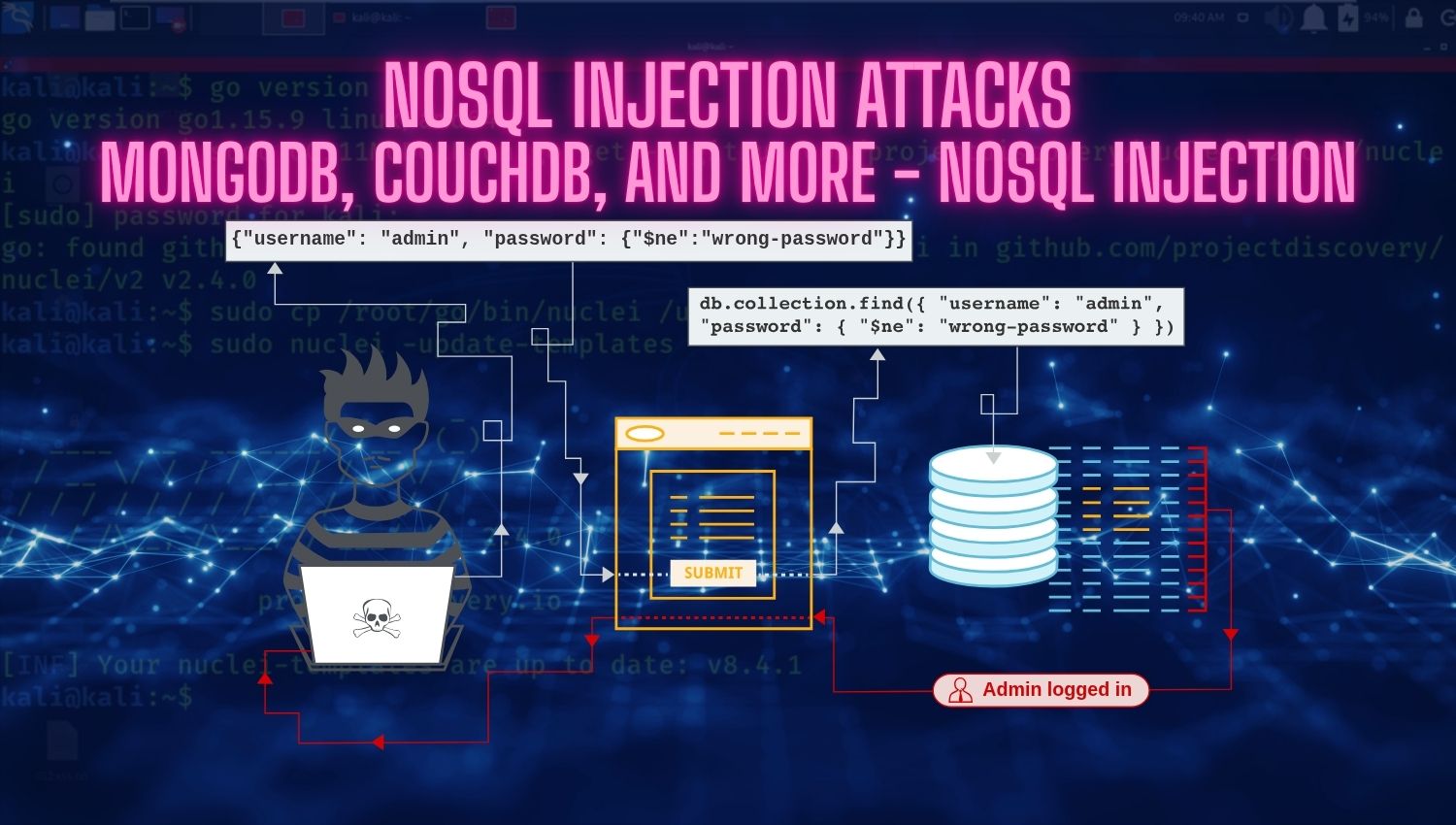
Introduction Subdomain takeover is a critical security vulnerability that allows attackers to gain unauthorized control over a subdomain of a legitimate domain through misconfigured or abandoned DNS records. This vulnerability exploits the gap between DNS configuration and actual resource ownership, creating an entry point for sophisticated attacks that leverage the trust associated with legitimate domain names. Unlike traditional