Introduction
File and Hash Threat Intel is a beginner-friendly blue team challenge hosted on TryHackMe, designed to help SOC analysts and cybersecurity learners build practical skills in malware detection, hash analysis, and threat intelligence workflows. This room simulates real-world scenarios where attackers disguise malicious files using misleading names and extensions, requiring defenders to investigate using hash lookups, sandboxing, and behavioral analysis.
This walkthrough provides a step-by-step guide through the challenge, covering everything from identifying suspicious filenames to extracting SHA256 hashes and interpreting threat labels across platforms like VirusTotal, Hybrid Analysis, and MalwareBazaar. By following this guide, learners will gain hands-on experience with tools and techniques used in professional SOC environments to detect, classify, and respond to file-based threats.
Learning Objectives
By completing this TryHackMe walkthrough, participants will:
- Detect suspicious file naming conventions and double extensions used for masquerading malware
- Extract and analyze file hashes using PowerShell and CMD on Windows systems
- Use VirusTotal and MalwareBazaar to classify threats and identify MITRE ATT&CK techniques
- Perform sandbox analysis with Hybrid Analysis to uncover stealthy behaviors and command executions
- Interpret threat labels, process trees, and dropped files to build a complete attack narrative
- Apply these techniques to real-world SOC workflows for faster detection and incident response
Purpose of This CTF
This room serves as a foundational exercise for blue teamers, emphasizing the importance of hash-based threat detection. Every file, regardless of its name, carries a unique hash — a digital fingerprint that remains unchanged even if the file is renamed. Attackers often exploit this by disguising malware with misleading filenames, hoping to evade basic signature-based defenses.
However, when a file appears suspicious, submitting its hash to a threat intelligence platform like VirusTotal or MalwareBazaar can reveal its true nature. If the malware is newly crafted, it may not be flagged immediately, requiring deeper sandbox analysis and behavioral inspection. This challenge teaches learners how to navigate that process, equipping them with the skills to identify, classify, and respond to file-based threats using open-source tools and forensic workflows.
Let’s solve the Room:
Task 2: Filenames and Paths
- One file displays one of the indicators mentioned. Can you identify the file and the indicator? (Answer: file, property)
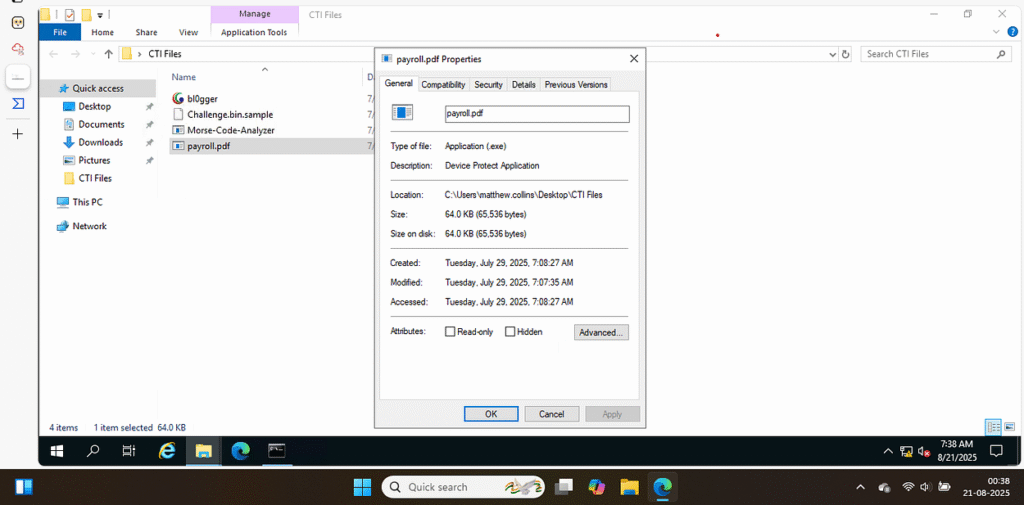
As we can see, the file is named with a double extension, and it is an executable.
Answer: payroll.pdf, Double extensions
Task 3: File Hash Lookup
Q 1. What is the SHA256 hash of the file bl0gger?
We are working with a Windows machine. We have two options to get the hash: using CMD or PowerShell.
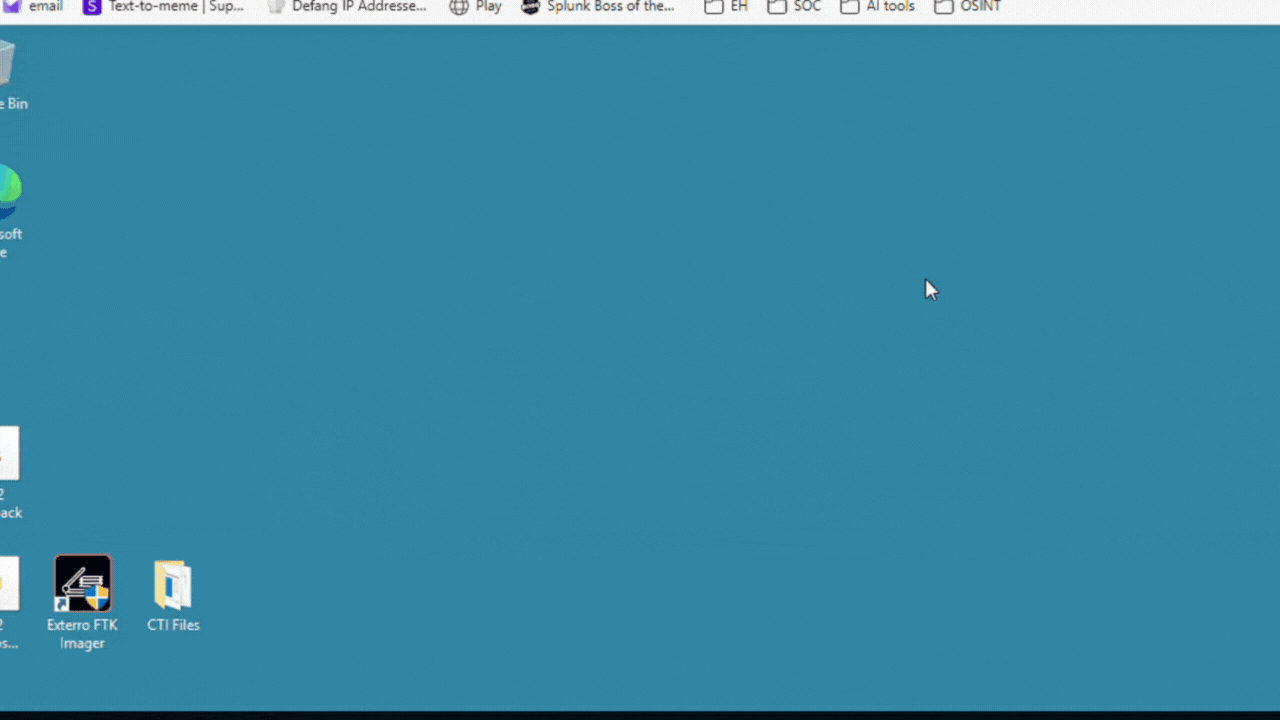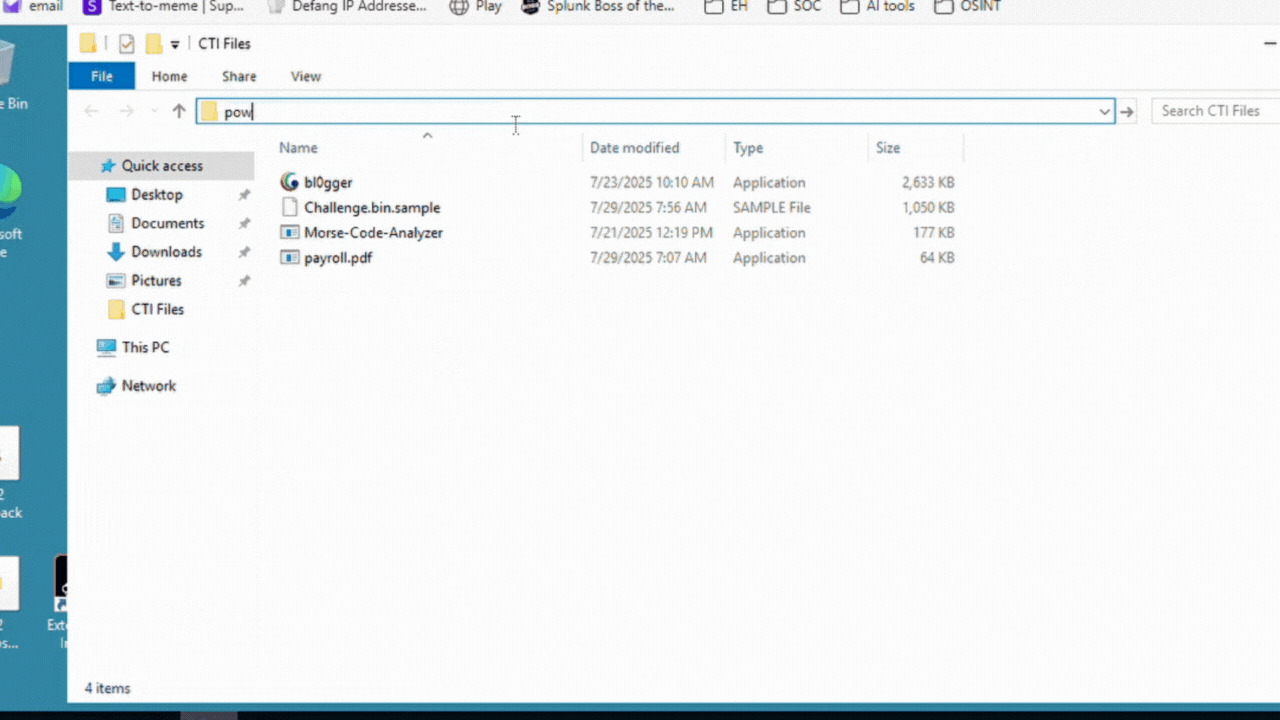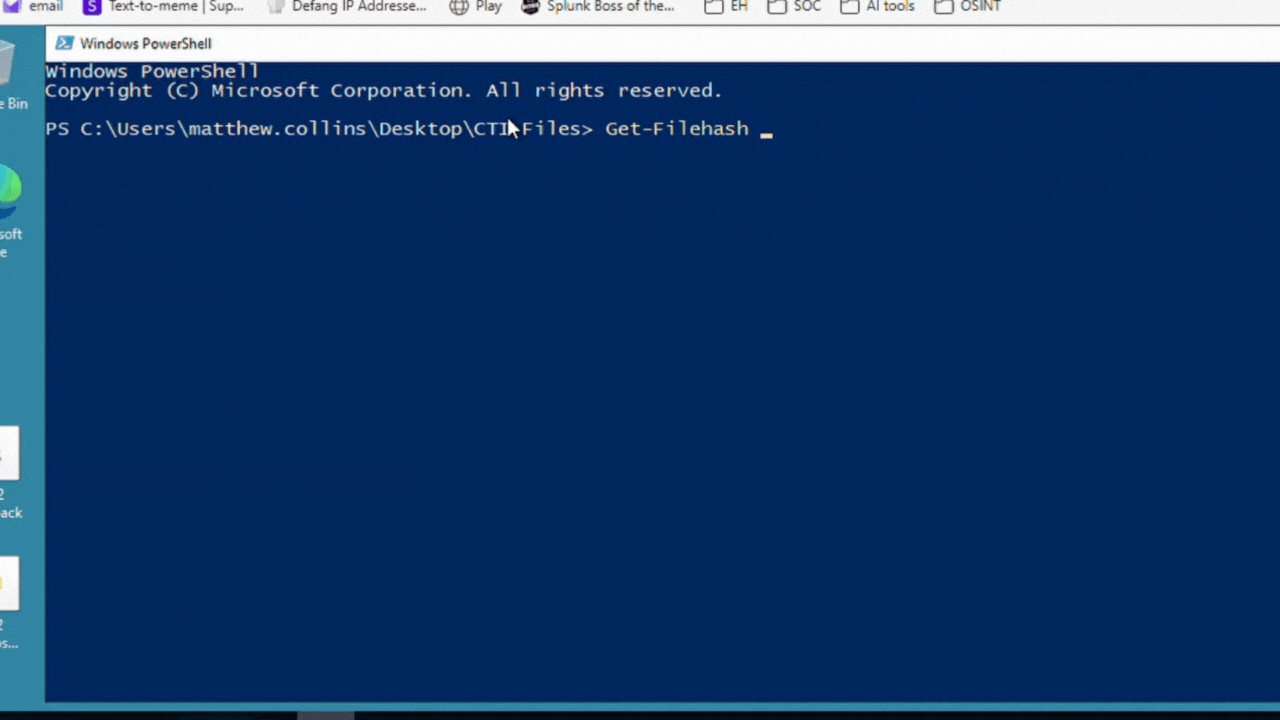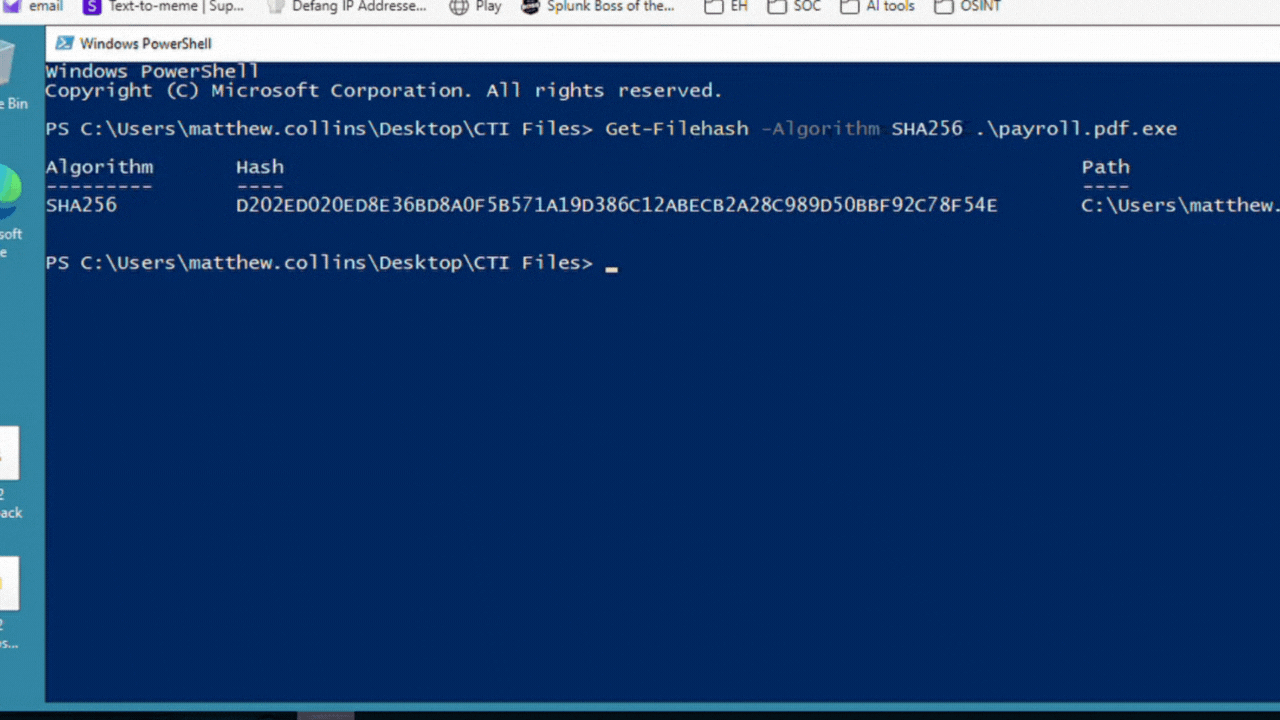
Answer: 2672b6688d7b32a90f9153d2ff607d6801e6cbde61f509ed36d0450745998d58
Q 2. On VirusTotal, what is the threat label used to identify the malicious file?
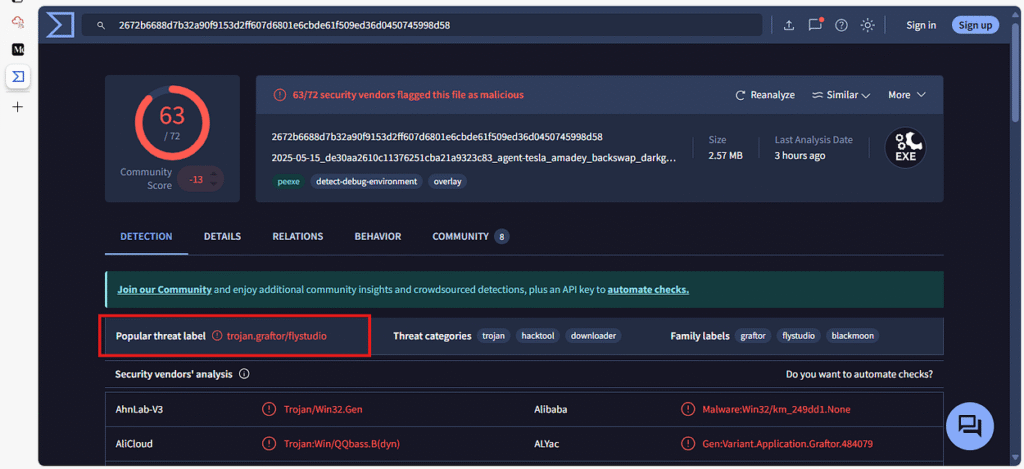
Answer: trojan.graftor/flystudio
Q 3. When was the file first submitted for analysis? (Answer format: YYYY-MM-DD HH:MM:SS)
The first submission will appear under the “Details” tab. Currently, we are on the “Detection” tab.
Answer: 2025–05–15 12:03:49 UTC
Q 4. According to MalwareBazaar, which vendor classified the Morse-Code-Analyzer file as non-malicious?
Now get the hash of Morse Code Analyzer file in the same way as demonstrated in the GIF above.
Put this way: sha256:1f8806869616c18cbae9ffcf581c0428915d32fb70119df16d08078d92d1a5e3
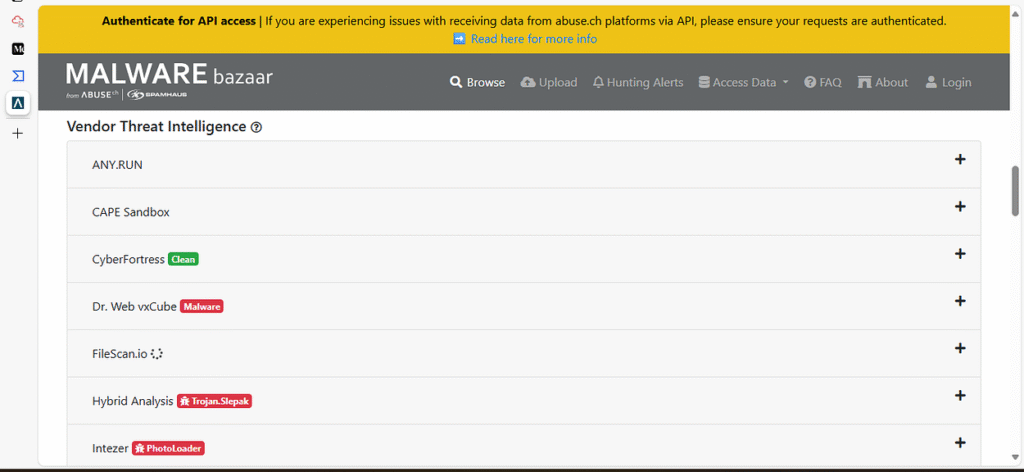
Answer: CyberFortress
Q 4. On VirusTotal, what MITRE technique has been flagged for persistence and privilege escalation for the Morse-Code-Analyzer file?
Technique is visible under the behavior tab:
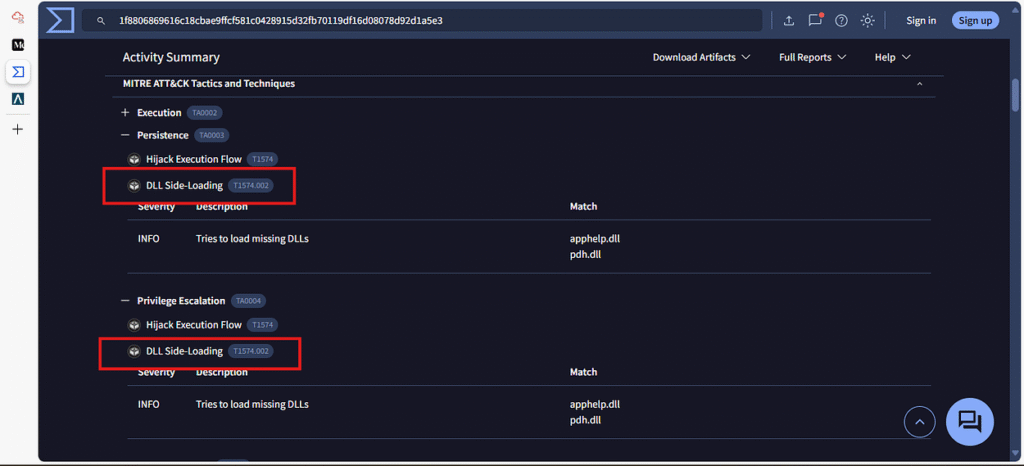
Answer: DLL Side-Loading
Task 4: Sandbox Analysis
Q 1. What tags are used to identify the bl0gger.exe malicious file on Hybrid Analysis? (Answer: Tag1, Tag2, Tag3)
OH, we need one more hash from file bl0gger.exe, use a similar method to get it. This time, the platform will be Hybrid-Analysis:
Hash: 2672B6688D7B32A90F9153D2FF607D6801E6CBDE61F509ED36D0450745998D58
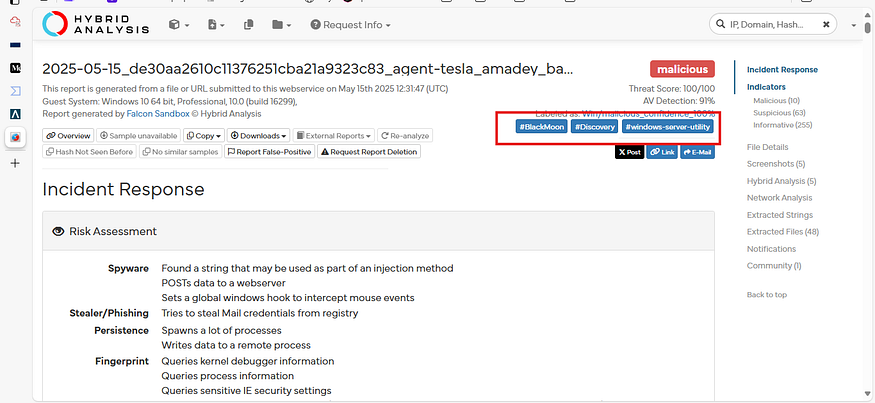
Answer: BlackMoon, Discovery, windows-server-utility
Q 2. What was the stealth command line executed from the file?
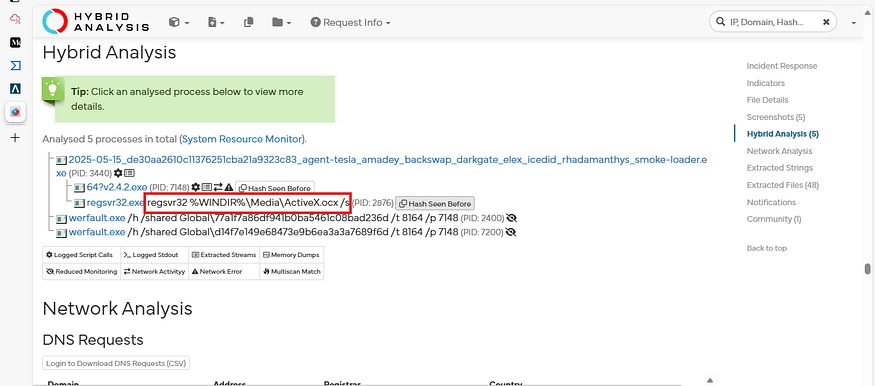
This command quietly installs a small helper tool on your computer so that other apps can use it without popups or noise.
Answer: regsvr32 %WINDIR%\Media\ActiveX.ocx /s
Q 3. Which other process was spawned according to the process tree?
Answer: werfault.exe
Q 4. The payroll.pdf application seems to be masquerading as which known Windows file?
Answer: svchost.exe
Q 5. What associated URL is linked to the file?
Hash file: D202ED020ED8E36BD8A0F5B571A19D386C12ABECB2A28C989D50BBF92C78F54E
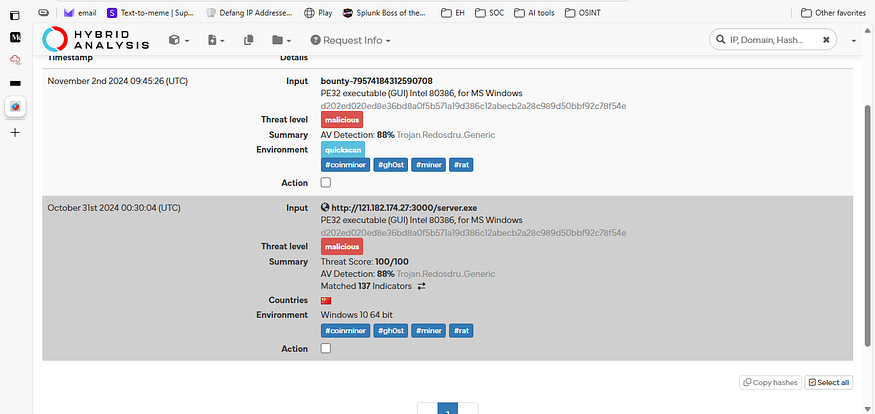
Answer: hxxp://121.182.174.27:3000/server.exe
Q 6. How many extracted strings were identified from the sandbox analysis of the file?
Answer: 454
Task 5: Threat Intelligence Challenge
Q 1. What is the SHA256 hash of the file?
Answer: 43b0ac119ff957bb209d86ec206ea1ec3c51dd87bebf7b4a649c7e6c7f3756e7
Q 2. What family labels are assigned to the file on VirusTotal?
Answer: akira, filecryptor
Q 3. How many security vendors have flagged the file as malicious?
Answer: 61
Q 4. Name the text file dropped during the execution of the malicious file.
Answer: akira_readme.txt
Q 5. What PowerShell script is observed to be executed?
Answer: Get-WmiObject Win32_Shadowcopy | Remove-WmiObject
Q 6. What is the MITRE ATT&CK ID associated with this execution?
Answer: T1490
This marks the end of the challenge, but additional tools for threat intelligence are available, which will be useful for advanced analysis.
if you want to check your system for any hidden files or executables, you can try the simple tool Autoruns, which has VirusTotal integration. The hash of each file is visible in the application, allowing you to conduct further investigation.
Author: Atik Shekh | Security Operations Specialist
- Medium: Howler’s Articles
- LinkedIn: My Profile

