Introduction
In today’s mobile-driven world, the ability to monitor and analyze network traffic directly from your Android device offers a significant advantage for both professionals and enthusiasts. Termux, a powerful terminal emulator for Android, transforms your smartphone into a portable network diagnostics and security toolkit. With Termux, you can access a wide range of advanced Linux-based networking tools on the go—allowing you to troubleshoot issues, detect threats, and optimize network performance from virtually anywhere. This flexibility streamlines network management, supports real-time problem solving, and provides a practical, hands-on learning platform for anyone interested in cybersecurity, ethical hacking, or understanding how modern networks operate. Whether you’re at home, in the office, or traveling, Termux empowers you to take control of your network environment with ease.
Learning Objectives
- Understand the advantages of using Termux for network monitoring on Android devices.
- Learn practical methods and tools for capturing and filtering network traffic.
- Gain hands-on experience with essential commands and filters for real-world scenarios.
- Recognize the security and ethical considerations of network monitoring.
Benefits of Fast Network Monitoring with Termux
- Portability and Accessibility: With Termux, you can perform advanced network diagnostics and monitoring directly from your Android phone, eliminating the need for bulky laptops or dedicated hardware. This portability means you can analyze and secure networks wherever you are—at home, in the office, or while traveling—making it especially valuable for professionals who need to respond quickly to incidents or troubleshoot problems on the go.
- Real-Time Troubleshooting: Termux enables you to instantly diagnose connectivity issues, detect unauthorized devices, and analyze suspicious traffic as soon as problems arise. The ability to monitor network traffic in real time from your mobile device ensures that you can quickly identify and resolve issues, minimizing downtime and preventing potential threats from escalating.
- Security Assessment: Using Termux, you can identify vulnerabilities, scan for open ports, and monitor for potential attacks without needing a full desktop setup. This makes it easier to conduct security assessments and penetration tests in a variety of environments, including those where traditional tools may not be practical. Termux supports essential tools like tcpdump, tshark, and nmap, allowing you to carry out comprehensive security checks directly from your phone.
- Educational Value: Termux is also an excellent platform for learning. It allows beginners and students to experiment with network analysis tools in a safe, controlled environment, fostering a deeper understanding of network protocols, cybersecurity concepts, and ethical hacking techniques. This hands-on approach is ideal for building practical skills and confidence in network security.
- Automation and Scripting: Termux supports powerful scripting and automation capabilities, enabling you to automate repetitive monitoring tasks, schedule regular scans, and parse results for further analysis. This not only saves time but also ensures consistent and thorough network monitoring, making it easier to maintain high security standards and quickly respond to emerging threats.
My Pentest Story: The Real-Life Inspiration Behind This Article
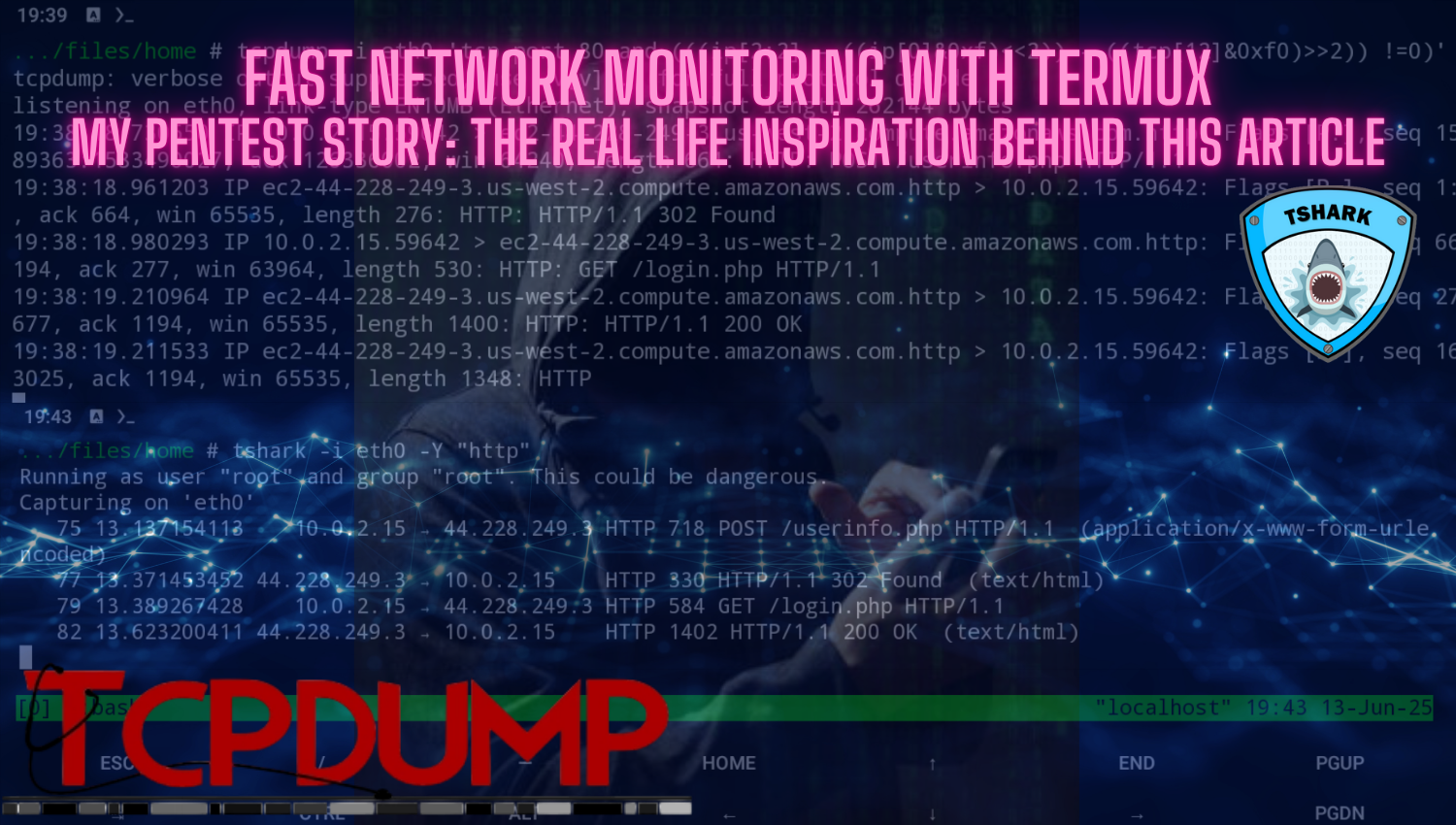
The main inspiration for writing this article was a real-life experience I had while visiting a company. I connected to the company’s Wi-Fi network. Out of professional curiosity, I decided to passively monitor the network traffic using Termux on my Android phone.
Using tools like tcpdump and tshark, I quickly discovered that a surprising amount of sensitive data, including usernames and passwords, was being transmitted in plain text over unencrypted protocols like HTTP and FTP. For example, I intercepted login credentials sent via HTTP Basic Authentication, which could be easily decrypted from network packets. Additionally, I observed that users were uploading files and sending FTP credentials without any encryption. When I shared these findings with the company, it prompted them to take more cautious measures. They realized how easily attackers, even those merely connected to the Wi-Fi network, could access and exploit sensitive information. As a result, the company took immediate action to secure internal communications, segment the guest network, and implement stronger authentication methods.
This eye-opening pentest experience highlighted both the risks of insecure network configurations and the powerful capabilities of mobile tools like Termux. This experience directly inspired me to write this article to share practical methods for network monitoring, raise awareness about common security vulnerabilities, and encourage others to take proactive steps to secure their own networks.
Termux Mastery: A Comprehensive Guide
In our Termux Cheat Sheet book, which has been prepared for you in PDF format, you can learn Linux commands, cyber security, coding, network connections and many more topics.
-35% $10 on buymeacoffeeMethods and Filters for Monitoring Your Network with Termux
1 Practical Examples with tcpdump
1. Capture only HTTP GET and POST requests:
$ tcpdump -i wlan0 'tcp port 80 and (((ip[2:2] - ((ip[0]&0xf)>2)) != 0)'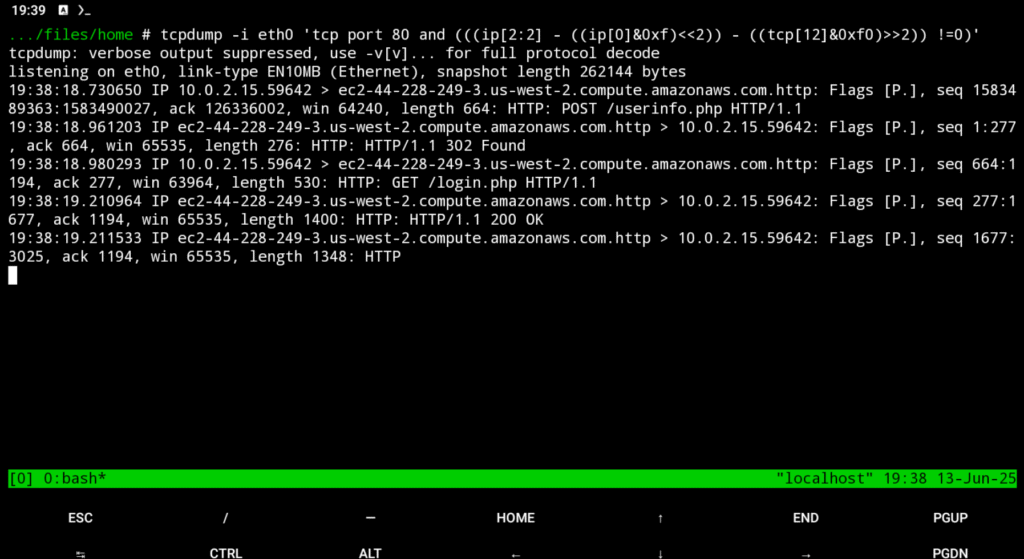
This command filters and captures only HTTP requests (such as GET and POST) on port 80.
2. Capture traffic destined for a specific IP address:
tcpdump -i wlan0 dst host 192.168.1.10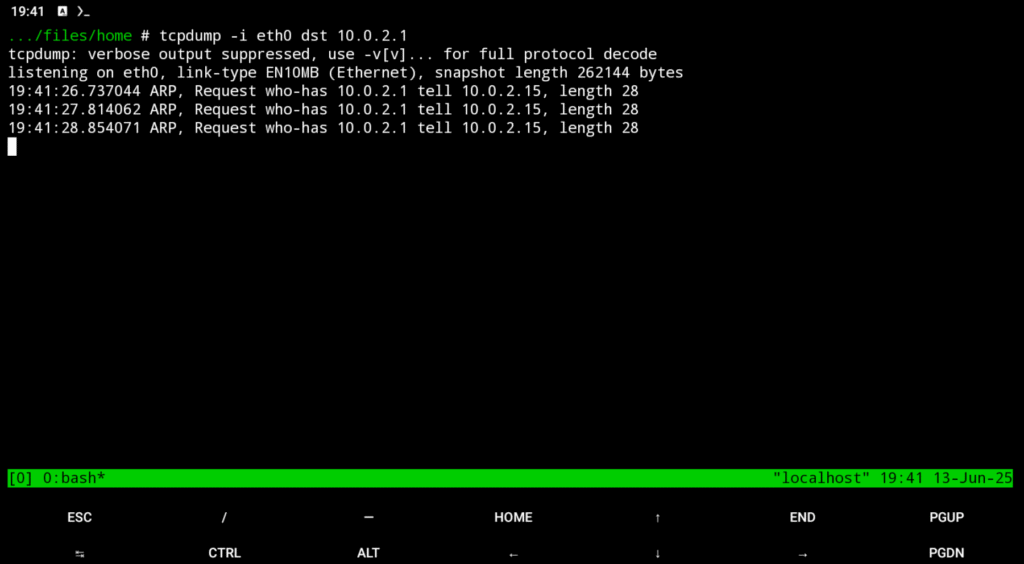
This captures packets where the destination IP is 192.168.1.10.
3. Capture DNS queries:
tcpdump -i wlan0 port 53This captures all DNS traffic (UDP port 53).
3 Practical Examples with tshark
1. Live monitoring of HTTP traffic:
tshark -i wlan0 -Y 'http'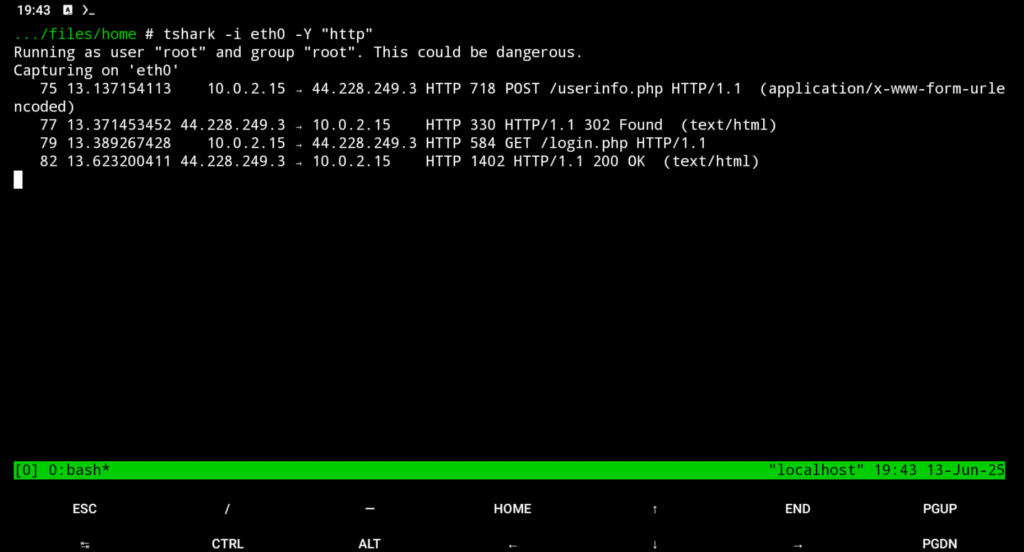
Displays all HTTP traffic in real time on the specified interface.
2. Filter packets from a specific source IP:
tshark -i wlan0 -Y 'ip.src == 192.168.1.5'Shows only packets where the source IP is 192.168.1.5.
3. Save packets to a file and analyze only TCP packets:
tshark -i wlan0 -w /sdcard/capture.pcap
tshark -r /sdcard/capture.pcap -Y 'tcp'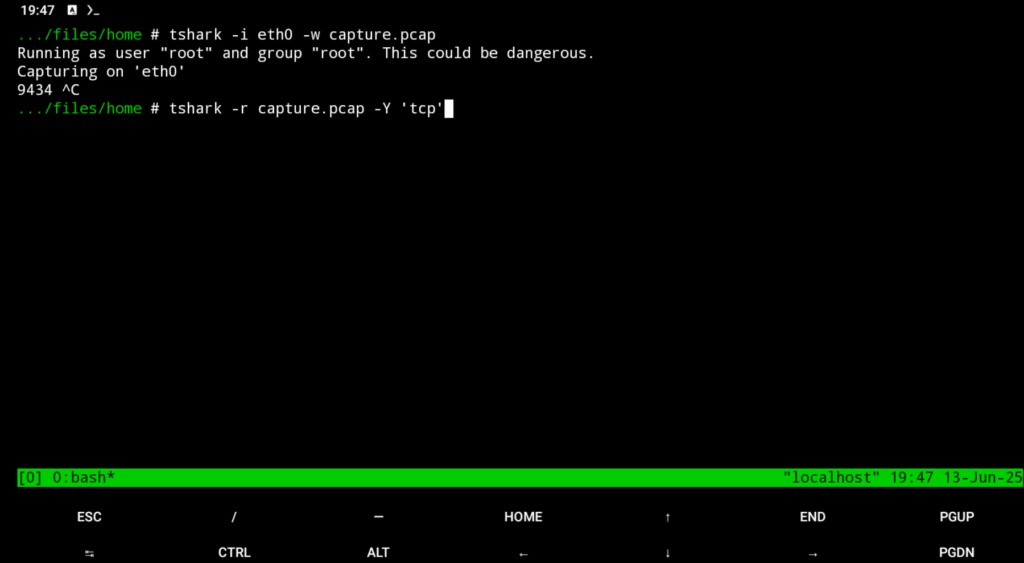
The first command saves traffic to a file, and the second analyzes only TCP packets from that file.
Mastering Linux Networking and Security
As you progress through this book, you’ll gain the skills necessary to not only manage networks but also protect them from the ever-evolving threats that exist in today’s digital landscape.
-5% 18 on buymeacoffeeConclusion
Termux empowers Android users to perform sophisticated network monitoring and comprehensive security assessments from virtually anywhere, making advanced diagnostics accessible beyond the confines of traditional desktop environments. By leveraging powerful tools such as tcpdump, tshark, nmap, and a wide range of built-in Termux utilities, users can efficiently capture, filter, and analyze network traffic with remarkable precision. This mobile-first approach is especially valuable for troubleshooting slow connections, detecting unauthorized devices, and proactively identifying vulnerabilities, whether you’re at home, in the office, or on the move. The versatility of Termux extends beyond just network diagnostics; it also serves as a robust learning platform for those eager to master network protocols, cyber defense techniques, and ethical hacking practices. With the ability to automate monitoring tasks, schedule regular scans, and parse results for deeper analysis, Termux streamlines the process of maintaining strong network security and fosters a hands-on understanding of cybersecurity concepts.
Moreover, the portability and flexibility of Termux mean that anyone—from IT professionals to students—can take control of their network environment, respond rapidly to incidents, and continuously improve their digital defenses. However, it is essential to always obtain proper authorization before monitoring or scanning any network, as responsible and ethical use of these tools is crucial for maintaining privacy and legal compliance. In summary, Termux stands out as an indispensable tool for modern network monitoring and security, combining convenience, power, and educational value in a single, mobile-friendly package. By integrating these capabilities into your workflow, you not only enhance your ability to secure and troubleshoot networks but also contribute to a safer and more resilient digital world.



this is really great blog, please post more content like this, but i think this requires rooting the phone
Yes, our phone needs to be rooted for this type of work.