Introduction
The MD2PDF TryHackMe Walkthrough room on TryHackMe offers an engaging and educational experience for individuals interested in the world of cybersecurity, particularly in web application vulnerabilities. This challenge is structured to guide participants through the process of exploiting a web application that converts Markdown files into PDF documents. By navigating through various stages of the challenge, users will gain hands-on experience with common security flaws that can be found in web applications, enhancing their skills in penetration testing and ethical hacking.
Learning Objectives
Participants engaging with the MD2PDF challenge will learn to:
- Understand the concepts of Markdown and its conversion to PDF.
- Identify and exploit vulnerabilities such as Cross-Site Scripting (XSS) and Server-Side Request Forgery (SSRF).
- Utilize tools like Nmap and Gobuster for reconnaissance and directory enumeration.
- Implement HTML injection techniques to access restricted areas of a web application.
Purpose of This CTF
The primary purpose of the MD2PDF CTF is to provide participants with a practical understanding of how vulnerabilities can be exploited in real-world scenarios. By focusing on the conversion of Markdown to PDF, this challenge highlights the importance of secure coding practices and input validation. The exercise aims to reinforce the idea that even seemingly benign features, such as text conversion tools, can introduce significant security risks if not properly secured. Additionally, this CTF serves as a stepping stone for those looking to delve deeper into web application security by offering a safe environment to experiment with different attack vectors without the risk of legal repercussions.
CTF Solution Steps
1. Nmap Scan:
The first step is to conduct a thorough Nmap scan to identify open ports and services running on the machine. This scanning process is critical for understanding potential vulnerabilities based on exposed services. Use the following command to scan all ports:
nmap -p- 10.10.155.26This command scans all ports from 1 to 65535 and will show you which ports are open. You will likely find that ports 80 and 5000 are open; these are typically where web applications operate.
2. Access Web Services:
After completing the scan, open a web browser and navigate to port 80 of your machine’s IP address. Here, you will find an input field designed for converting Markdown text into PDF format, which serves as the main interface for the MD2PDF challenge. You can test the functionality by entering simple text, such as “Hello World!”, and clicking the “Convert to PDF” button. This action will generate a PDF file, MD2PDF TryHackMe Walkthrough.
3. Directory Enumeration:
Utilize tools like Gobuster or Dirb to perform directory enumeration on both port 80 and any other open ports identified during your Nmap scan. Look specifically for hidden directories such as /admin, which may contain sensitive information or administrative functionalities. You can use Gobuster with a command like:
gobuster dir -u http://10.10.155.26/ -w /usr/share/wordlist/directory-list-2.3-medium.txt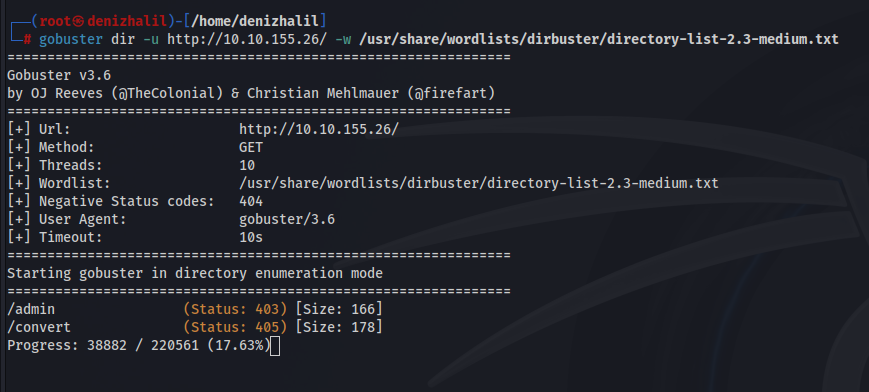
If you encounter a “403 Forbidden” error when trying to access the /admin directory, it indicates that this page may only be accessible from within the internal network.
4. Handle HTTP Errors:
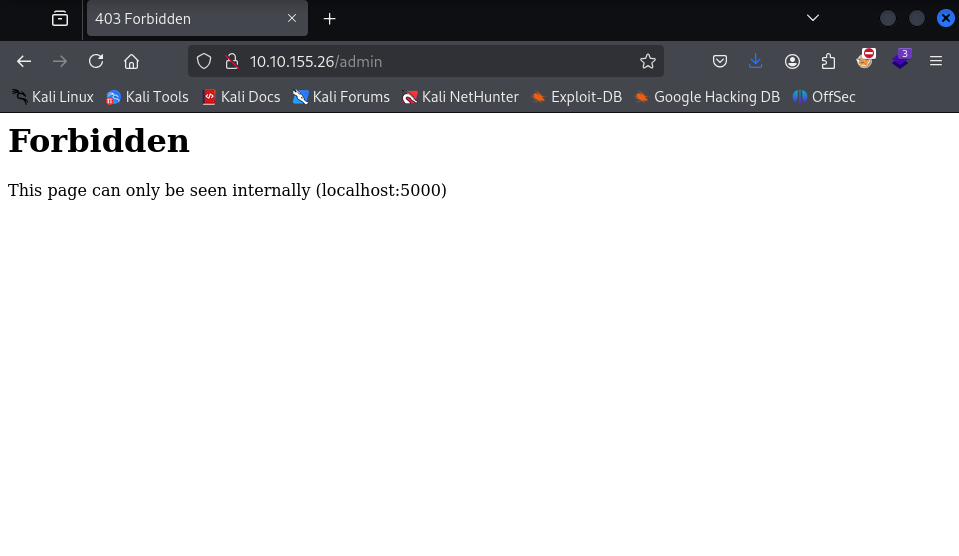
When faced with an HTTP 403 error, it suggests that certain pages may only be viewable internally or require specific conditions to access them. In such cases, consider alternative methods to gain access.
5. HTML Injection Testing:
Return to the input field on port 80 and test various HTML payloads. For example, entering simple HTML tags like Test can help determine whether HTML injection is possible within this application. If your HTML code renders correctly, it indicates that the application may be vulnerable to HTML injection attacks
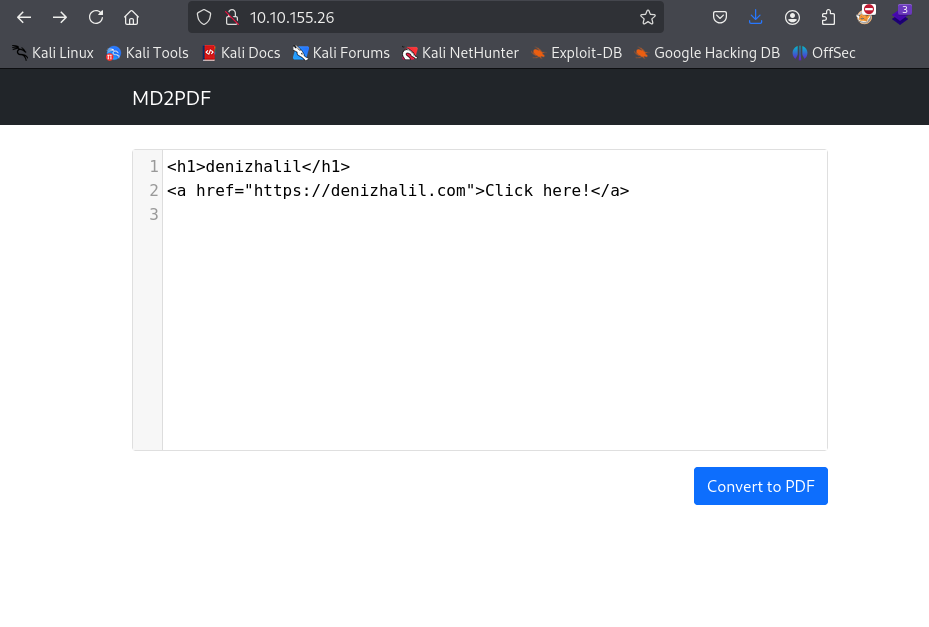
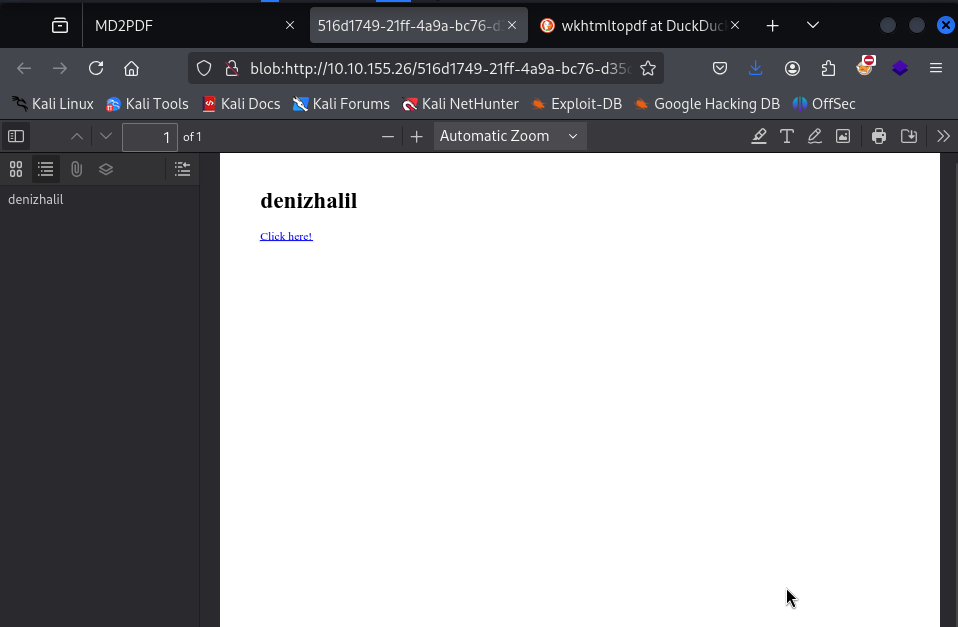
6. Utilize iFrames:
To bypass restrictions imposed by the web application, try injecting an iframe into your input that points to internal resources, such as
<iframe src="http://localhost:5000"></iframe>This technique allows you to view restricted content from within your own session since the request appears to originate from your machine.
7. Access Admin Directory:
Apply similar iframe techniques to access protected directories like /admin. If successful, this will enable you to view content that is otherwise restricted from direct access.
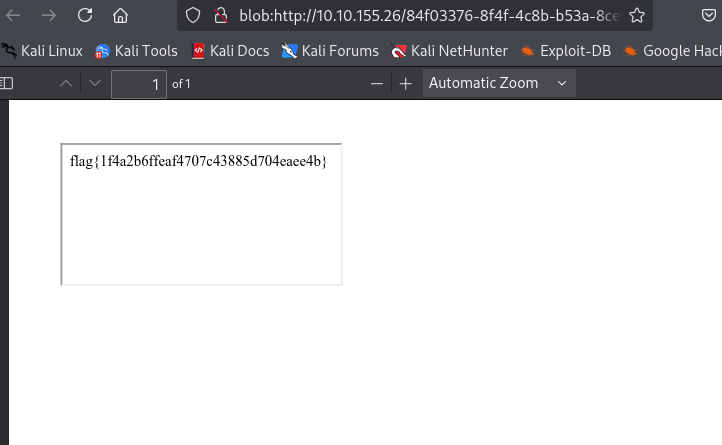
8. Capture the Flag:
Ultimately, your goal is to convert content from these internal pages into a PDF format that reveals a flag indicating completion of the challenge. Downloading this PDF and analyzing its contents will provide you with the necessary flag needed for submission.
Each of these steps is designed to enhance your skills in identifying and exploiting vulnerabilities in web applications. The MD2PDF room offers valuable lessons for both beginners and experienced cybersecurity professionals alike, reinforcing critical concepts in web security and ethical hacking practices.
Conclusion
The MD2PDF TryHackMe Walkthrough challenge not only serves as an excellent introduction to web application vulnerabilities but also emphasizes the importance of secure coding practices in software development. By completing this CTF, participants gain valuable insights into how attackers exploit weaknesses in web applications and learn practical techniques for identifying these vulnerabilities in their own projects. This experience reinforces critical concepts in cybersecurity, including reconnaissance, exploitation techniques, and ethical hacking principles. As participants progress through similar challenges on platforms like TryHackMe, they build a solid foundation that is essential for any aspiring cybersecurity professional or ethical hacker looking to make a meaningful impact in securing digital environments against potential threats.

