Introduction
The rapid advancements of the digital age have undeniably transformed our lives, making everyday tasks more convenient and efficient. However, this technological progress has also introduced significant risks, particularly in the realm of cybersecurity. One of the most prevalent and dangerous threats in this landscape is malware, short for malicious software. Malware encompasses a wide array of software types specifically designed to compromise the security of individuals and organizations alike. These malicious programs can infiltrate systems, steal sensitive information, disrupt operations, and cause extensive damage. In this article, we will delve into the intricacies of malware—defining what it is, exploring its various types, understanding how it spreads, and discussing effective methods of protection. Our goal is to enhance readers’ understanding of this critical topic and raise awareness about the importance of cybersecurity in an increasingly interconnected world. As we navigate through the complexities of digital threats, it becomes evident that knowledge and proactive measures are essential for safeguarding our personal and professional information.
Learning Objectives
- Understand the definition and purpose of malware.
- Learn about different types of malware and how each operates.
- Discover the methods through which malware spreads.
- Explore protection methods to enhance your cybersecurity.
What is Malware?
Malware refers to any software intentionally designed to cause harm to a computer system, network, or device. This malicious software can take various forms and is typically used to steal data, disrupt operations, or compromise user information. The threats posed by malware are significant, affecting both individuals and organizations across the globe. The impact of malware can vary widely; some types may only display annoying advertisements, while others can encrypt user data and demand ransom payments, leading to severe consequences. The term “malware” encompasses various categories of harmful software, including viruses, worms, remote access trojan, ransomware, spyware, and adware. Each type operates differently and poses unique risks. For instance, viruses attach themselves to legitimate programs and spread when those programs are executed. In contrast, worms can self-replicate and spread across networks without requiring user action. Ransomware encrypts files and demands payment for decryption, while spyware covertly gathers sensitive information from users.
Definition and Purpose of Malware
The primary purpose of malware is to obtain sensitive information from users or disrupt their systems for financial gain. These programs often operate in the background without the user’s knowledge, infiltrating systems through various means. For example, malware may be delivered via phishing emails that trick users into providing information or downloading harmful software from a fake website. The consequences of malware can be devastating—leading to personal data loss, financial damage, and reputational harm. Malware authors frequently employ sophisticated techniques to ensure their software remains undetected and effective. They may use social engineering tactics to manipulate users into executing malicious files or clicking on harmful links. Once installed on a system, malware can execute its payload—performing actions such as stealing credentials, corrupting files, or creating backdoors for future access.
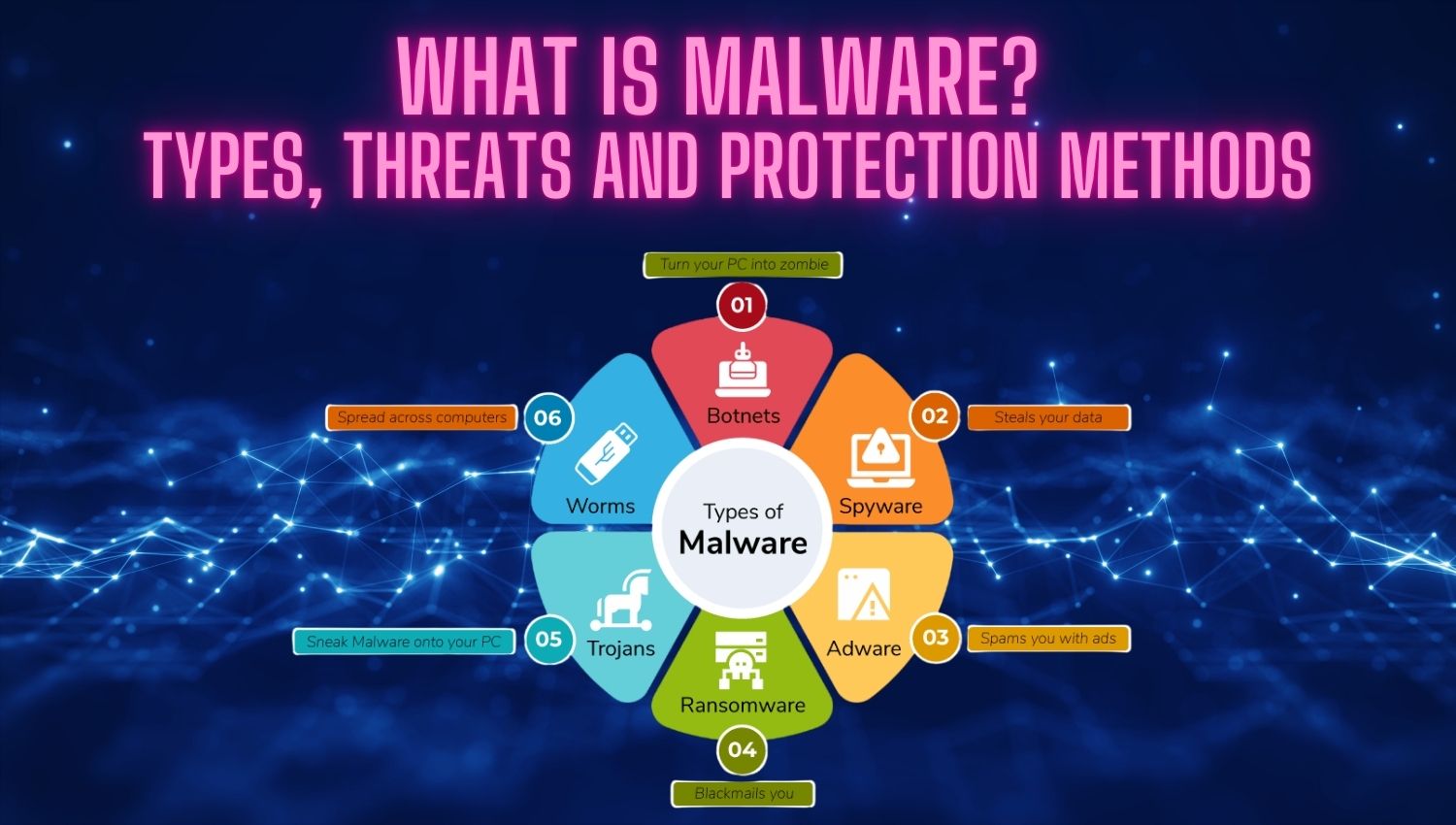
Types of Malware
Malware can be categorized into several distinct types, each with unique characteristics and methods of infection. Understanding these categories is essential for recognizing the potential threats they pose. Here are eight common types of malware:
- Viruses: Viruses are one of the most well-known types of malware. They consist of malicious code that attaches itself to legitimate programs or files. When these infected programs are executed, the virus activates and can spread to other files or systems. Viruses often aim to delete or corrupt data, and they can proliferate rapidly if users do not exercise caution when downloading or executing files. They may also disrupt system performance and lead to data loss.
- Worms: Worms are a particularly dangerous type of malware because they can self-replicate and spread across networks without any user intervention. Unlike viruses, worms do not need to attach themselves to a host program; they exploit vulnerabilities in network protocols to infect other devices. This autonomous nature allows worms to quickly infect entire networks, causing significant damage, including data loss and system malfunctions.
- Trojan Horses: Trojans are deceptive programs that disguise themselves as legitimate software to trick users into installing them. Once activated, they can perform a variety of malicious actions, such as stealing sensitive information, creating backdoors for further attacks, or downloading additional malware onto the infected system. Trojans rely heavily on social engineering tactics to convince users to execute them, making them particularly insidious.
- Ransomware: Ransomware is a type of malware that encrypts a user’s files and demands a ransom payment for the decryption key. This form of malware bytes has surged in popularity among cybercriminals due to its profitability. Ransomware attacks can have devastating effects on both individuals and organizations, leading to data loss and significant financial damage. Well-known ransomware variants include WannaCry and Petya, which have caused widespread disruptions in various sectors.
- Spyware: Spyware is designed to secretly gather information about users without their consent. It operates covertly, tracking user activity and collecting sensitive data such as passwords, credit card numbers, and browsing habits. This information is then transmitted to malicious actors who may use it for identity theft or financial fraud. Spyware often comes bundled with free software or is installed through deceptive ads.
- Adware: Adware displays unwanted advertisements on a user’s device and may track user behavior to deliver targeted ads. While adware is generally considered less harmful than other types of malware, it can still negatively impact user experience by slowing down devices and cluttering screens with intrusive ads. Additionally, adware can pave the way for more dangerous infections by exploiting the same vulnerabilities it uses for advertisement delivery.
- Rootkits: Rootkits are a more advanced form of malware that provides cybercriminals with unauthorized access to a computer system while hiding their presence from users and security software. Once installed, rootkits can manipulate system processes, allowing attackers to execute commands remotely, steal data, or install additional malicious software without detection.
- Keyloggers: Keyloggers are designed to record every keystroke made by a user on their device. This information can include sensitive data like passwords, credit card numbers, and personal messages. Keyloggers can be particularly damaging as they provide attackers with direct access to confidential information without the user’s knowledge. They often operate silently in the background and can be difficult to detect.
Read: Creating Ransomware with Python | Part 1
How Malware Spreads
Malware can spread through various methods, each exploiting different vulnerabilities in human behavior or technology. Understanding these methods is crucial for individuals and organizations to protect themselves effectively. Here are six common ways malware spreads:
- Phishing Emails: Phishing remains one of the most prevalent methods for spreading malware. Cybercriminals send deceptive emails that appear to come from trusted sources, such as banks or colleagues. These emails often contain malicious attachments or links that, when clicked, either download malware directly onto the user’s device or redirect them to a compromised website. The effectiveness of phishing lies in its ability to manipulate users into acting without suspicion, making it a favored tactic among cybercriminals.
- Malicious Websites: Cybercriminals create fake websites that mimic legitimate ones to deceive users into downloading harmful software. These sites may host malicious code that automatically installs malware on a user’s device upon visiting, a tactic known as “drive-by downloading.” Users do not need to click anything; simply visiting the site can result in an infection. This method is particularly dangerous because it can affect even cautious users who might inadvertently visit such sites.
- Exploiting Vulnerabilities: Malware can exploit security flaws in software or operating systems to gain unauthorized access to devices. Cybercriminals often use exploit kits—collections of tools designed to take advantage of known vulnerabilities—to deliver malware silently. When users visit compromised websites or click on malicious ads, these kits scan for weaknesses in their systems and deploy malware if a vulnerability is found. This method highlights the importance of keeping software up-to-date and applying security patches promptly.
- Social Engineering: Social engineering encompasses various tactics that manipulate individuals into divulging confidential information or installing malware. Attackers may pose as IT support, customer service representatives, or even friends to gain trust and encourage users to take actions that compromise their security. For instance, they might ask users to download a “necessary update” that is actually malware disguised as legitimate software. This method leverages human psychology rather than technical vulnerabilities.
- Infected Removable Media: USB drives and other removable media can serve as vectors for malware transmission. Cybercriminals may deliberately leave infected USB drives in public places, hoping someone will find and plug them into their computer out of curiosity. Once connected, the malware can execute automatically, leading to an infection of the device and potentially spreading to connected networks. This method exploits human curiosity and trust in seemingly innocuous devices.
- Malvertising: Malvertising involves injecting malicious code into legitimate online advertisements displayed on high-traffic websites. Users may encounter these ads while browsing, which can lead them to malicious sites or prompt them to download harmful software disguised as legitimate applications. Even reputable sites can unknowingly host malvertising, making it difficult for users to discern safe from unsafe content online.
Check: Phishing Attacks categories
Recommendations for Protection
- Regular Software Updates: Keeping all operating systems, applications, and security software up to date is one of the most effective ways to protect against malware. Software developers frequently release updates that include security patches to address vulnerabilities that cybercriminals may exploit. By enabling automatic updates, you ensure that your devices are always protected with the latest security enhancements, reducing the risk of malware infections.
- Use Strong Security Software: Invest in reputable antivirus and anti-malware solutions that offer comprehensive protection against various types of threats. Look for software that provides real-time scanning, automatic updates, and advanced features such as behavior-based detection and web protection. Regularly review and adjust the settings of your security software to maximize its effectiveness in identifying and neutralizing potential threats.
- Educate Yourself and Others: Knowledge is a powerful tool in combating cybersecurity threats. Participate in cybersecurity training programs or workshops to stay informed about the latest malware trends, phishing tactics, and safe online practices. Sharing this knowledge with friends, family, and colleagues can create a more informed community that is better equipped to recognize and respond to potential threats. Consider organizing group discussions or sharing informative resources to foster a culture of cybersecurity awareness.
- Practice Safe Browsing: Be vigilant when navigating the internet. Avoid clicking on links or downloading attachments from unknown or suspicious sources, as these can often lead to malware infections. Use ad blockers and browser extensions designed to enhance security by blocking potentially harmful ads and scripts. Additionally, verify website URLs before entering sensitive information; look for HTTPS in the address bar as an indicator of a secure connection.
- Enable Two-Factor Authentication (2FA): Whenever possible, enable two-factor authentication for your online accounts. This adds an extra layer of security by requiring not only your password but also a second form of verification—such as a text message code or an authentication app—before granting access. 2FA significantly reduces the risk of unauthorized access, even if your password is compromised.
- Backup Important Data: Regularly backing up important files is crucial for data recovery in case of a malware attack or other data loss incidents. Use a combination of external hard drives and cloud storage solutions to create multiple copies of your critical information. Schedule automatic backups to ensure that your data is consistently protected without requiring manual intervention. In the event of a ransomware attack or data corruption, having backups allows you to restore your files without succumbing to ransom demands.
Read: What is Social Engineering: A Comprehensive Overview
Conclusion
Malware represents a significant threat in today’s digital landscape, affecting individuals, businesses, and governments alike. As cybercriminals continuously evolve their tactics, it becomes increasingly important for everyone to remain vigilant and proactive in their cybersecurity efforts. The consequences of malware infections can be severe, including data breaches, financial losses, and reputational damage. To combat these threats effectively, individuals and organizations should adopt a multi-faceted approach to cybersecurity. Regular software updates are essential, as they help close vulnerabilities that malware can exploit. Keeping operating systems and security software current reduces the risk of infection significantly.
Using robust security software is another critical component of defense. Antivirus programs and firewalls can detect and neutralize threats before they cause harm. Additionally, users should practice cautious online behavior by being wary of unsolicited emails and suspicious websites. Education plays a vital role in enhancing overall security. Organizations should invest in training programs to inform employees about the latest threats and best practices for avoiding them. By fostering a culture of cybersecurity awareness, individuals can empower themselves and those around them to recognize potential risks and respond effectively. Ultimately, every individual has a responsibility to protect not only themselves but also their community in the realm of cybersecurity. By staying informed and sharing knowledge about safe practices, we can collectively work towards a more secure digital environment.