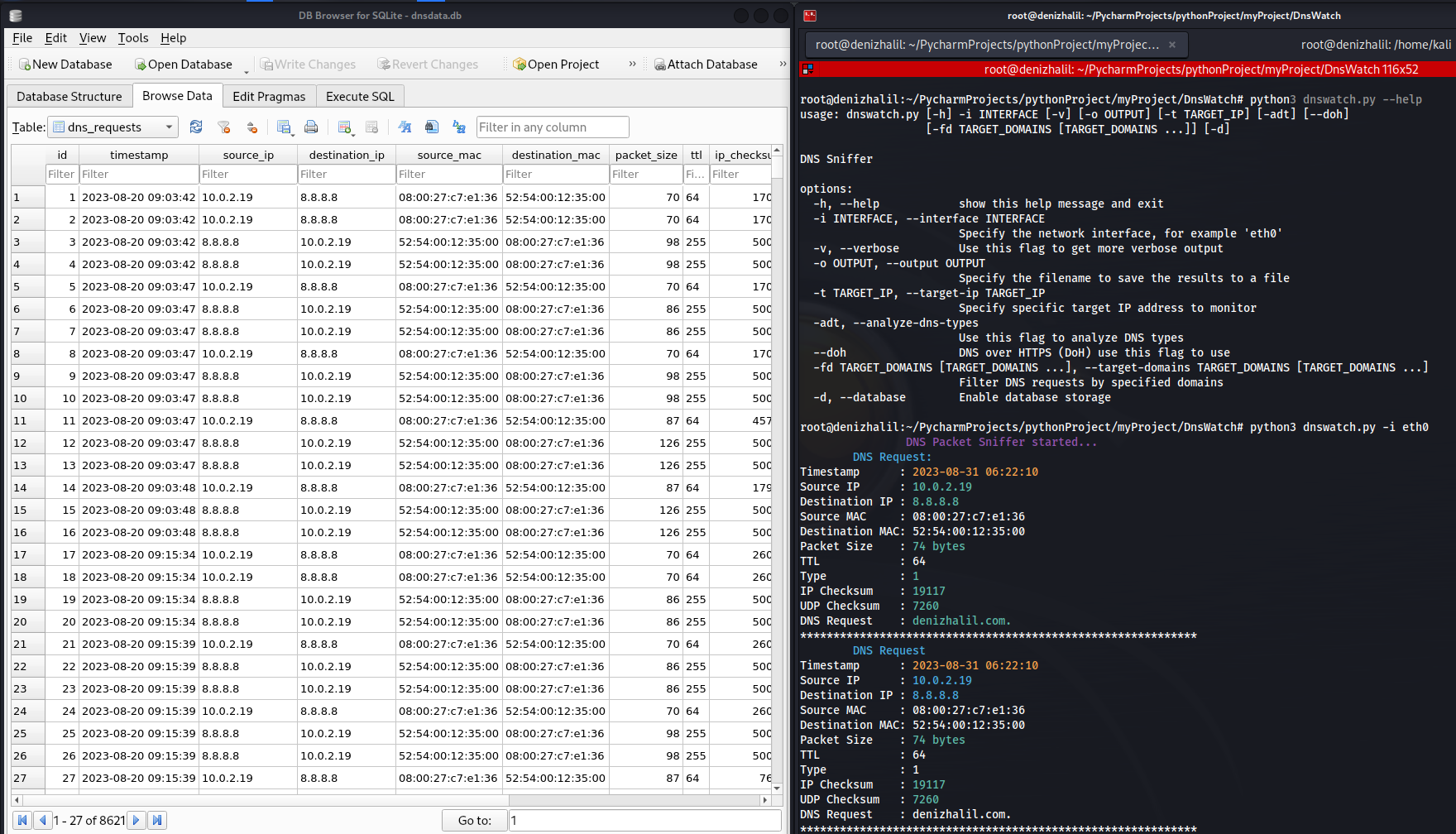
DNSWatch is a Python-based tool that allows you to sniff and analyze DNS (Domain Name System) traffic on your network. It listens to DNS requests and responses and provides insights into the DNS activity.
And before we start the article, we recommend you to read our article called what is dns and how does it work.
Note: The Dnswatch tool was recently released on kitploit 🥳
Features
- Sniff and analyze DNS requests and responses.
- Display DNS requests with their corresponding source and destination IP addresses.
- Optional verbose mode for detailed packet inspection.
- Save the results to a specified output file.
- Filter DNS traffic by specifying a target IP address.
- Save DNS requests in a database for further analysis(optional)
- Analyze DNS types (optional).
- Support for DNS over HTTPS (DoH) (optional).
Requirements
- Python 3.7+
- scapy 2.4.5 or higher
- colorama 0.4.4 or higher
Installation
- Clone this repository:
git clone https://github.com/HalilDeniz/DNSWatch.git- Install the required dependencies:
pip install -r requirements.txtUsage
python dnswatch.py -i <interface> [-v] [-o <output_file>] [-k <target_ip>] [--analyze-dns-types] [--doh]-i,--interface: Specify the network interface (e.g., eth0).-v,--verbose: Use this flag for more verbose output.-o,--output: Specify the filename to save results.-t,--target-ip: Specify a specific target IP address to monitor.-adt,--analyze-dns-types: Analyze DNS types.--doh: Use DNS over HTTPS (DoH) for resolving DNS requests.-fd,--target-domains: Filter DNS requests by specified domains.-d,--database: Enable database storage for DNS requests.
Press Ctrl+C to stop the sniffing process.
Examples
- Sniff DNS traffic on interface “eth0”:
python dnswatch.py -i eth0- Sniff DNS traffic on interface “eth0” and save the results to a file:
python dnswatch.py -i eth0 -o dns_results.txt- Sniff DNS traffic on interface “eth0” and filter requests/responses involving a specific target IP:
python dnswatch.py -i eth0 -t 192.168.1.100- Sniff DNS traffic on interface “eth0” and enable DNS type analysis:
python dnswatch.py -i eth0 --analyze-dns-types- Sniff DNS traffic on interface “eth0” using DNS over HTTPS (DoH):
python dnswatch.py -i eth0 --doh- Sniff DNS traffic on interface “wlan0” and Enable database storage
python3 dnswatch.py -i wlan0 --databaseLicense and Disclaimer
DNSWatch is released under the MIT License, as detailed in the LICENSE file within the repository. However, it is imperative to note that this tool is intended strictly for educational and testing purposes. The tool should not be utilized for malicious activities, as this contradicts its ethical and constructive intent.
Conclusion
DNSWatch emerges as a potent DNS packet sniffer, enabling network enthusiasts to delve into the intricacies of network traffic. Its robust feature set, ease of use, and commitment to responsible usage make it an asset to both educational settings and network analysis endeavors. By fostering a deeper understanding of network communication, DNSWatch empowers users to navigate the digital landscape with knowledge and integrity.