introduction
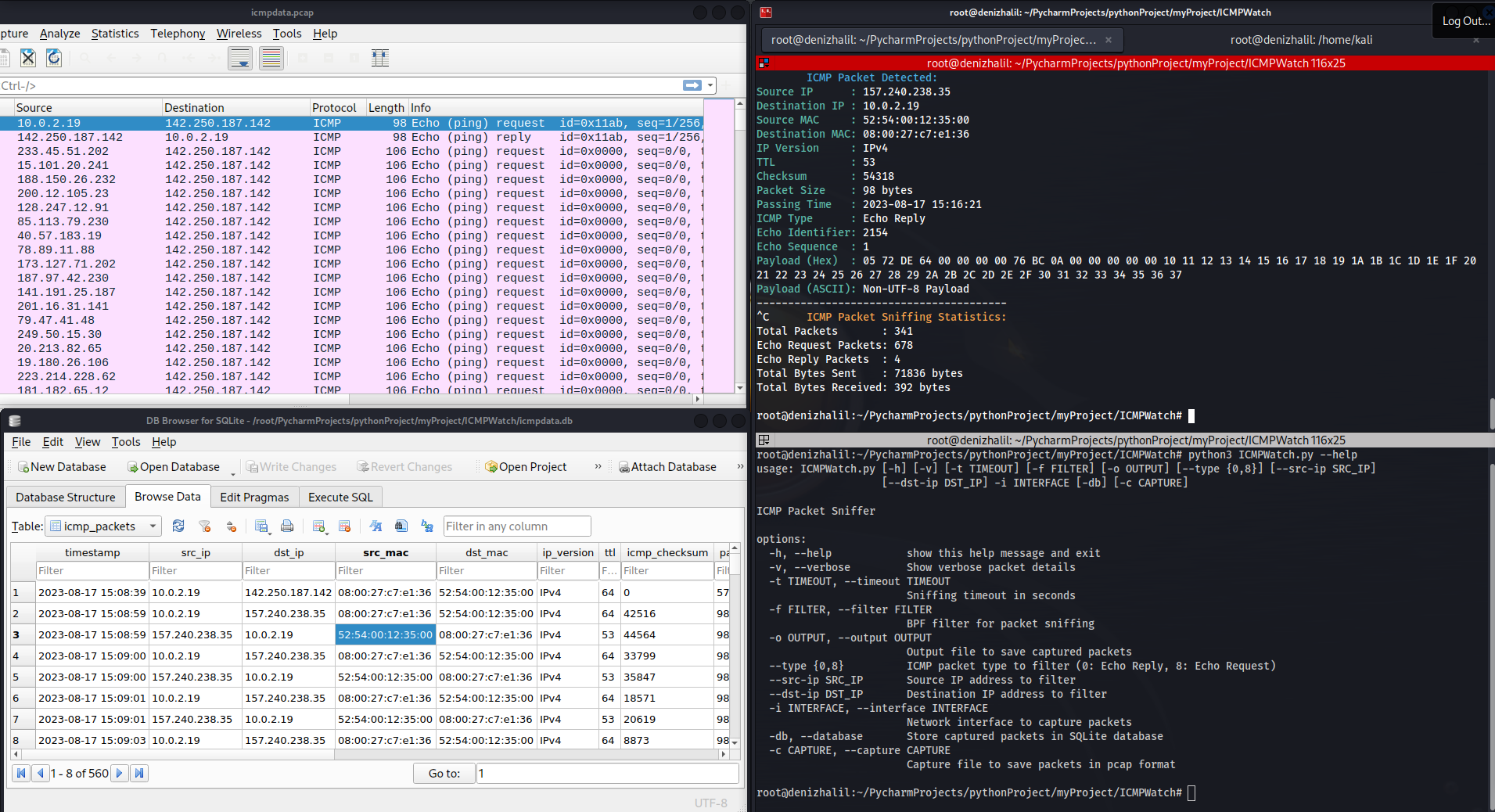
In the realm of network analysis and cybersecurity, the ability to monitor and analyze network traffic is paramount. ICMP Packet Sniffer, a Python program, comes to the forefront as a powerful tool for capturing and dissecting ICMP (Internet Control Message Protocol) packets on network interfaces. The program empowers users with intricate insights into the details of captured packets, including source and destination IP addresses, MAC addresses, ICMP type, payload data, and more. Furthermore, this tool provides the capability to store the captured packets in both a SQLite database and the widely used PCAP format, thereby facilitating comprehensive analysis and subsequent research.
Features
- Capture and analyze ICMP Echo Request and Echo Reply packets.
- Display detailed information about each ICMP packet, including source and destination IP addresses, MAC addresses, packet size, ICMP type, and payload content.
- Save captured packet information to a text file.
- Store captured packet information in an SQLite database.
- Save captured packets to a PCAP file for further analysis.
- Support for custom packet filtering based on source and destination IP addresses.
- Colorful console output using ANSI escape codes.
- User-friendly command-line interface.
Requirements
- Python 3.7+ installed on their system.
- scapy library version 2.4.5 or higher.
- colorama library version 0.4.4 or higher.
Installation
- Clone this repository:
git clone https://github.com/HalilDeniz/ICMPWatch.git- Install the required dependencies:
pip install -r requirements.txtUsage
python ICMPWatch.py [-h] [-v] [-t TIMEOUT] [-f FILTER] [-o OUTPUT] [--type {0,8}] [--src-ip SRC_IP] [--dst-ip DST_IP] -i INTERFACE [-db] [-c CAPTURE]-vor--verbose: Show verbose packet details.-tor--timeout: Sniffing timeout in seconds (default is 300 seconds).-for--filter: BPF filter for packet sniffing (default is “icmp”).-oor--output: Output file to save captured packets.--type: ICMP packet type to filter (0: Echo Reply, 8: Echo Request).--src-ip: Source IP address to filter.--dst-ip: Destination IP address to filter.-ior--interface: Network interface to capture packets (required).-dbor--database: Store captured packets in an SQLite database.-cor--capture: Capture file to save packets in pcap format.
Press Ctrl+C to stop the sniffing process.
Examples
- Capture ICMP packets on the “eth0” interface:
python3 icmpwatch.py -i eth0- Sniff ICMP traffic on interface “eth0” and save the results to a file:
python3 dnssnif.py -i eth0 -o icmp_results.txt- Filtering by Source and Destination IP:
python3 icmpwatch.py -i eth0 --src-ip 192.168.1.10 --dst-ip 192.168.1.20- Filtering ICMP Echo Requests:
python3 icmpwatch.py -i eth0 --type 8- Saving Captured Packets
python3 icmpwatch.py -i eth0 -c captured_packets.pcapLicense and Disclaimer
ICMPWatch is released under the MIT License, as detailed in the LICENSE file within the repository. However, it is imperative to note that this tool is intended strictly for educational and testing purposes. The tool should not be utilized for malicious activities, as this contradicts its ethical and constructive intent.
Conclusion
ICMPWatch emerges as a potent ICMP packet sniffer, enabling network enthusiasts to delve into the intricacies of network traffic. Its robust feature set, ease of use, and commitment to responsible usage make it an asset to both educational settings and network analysis endeavors. By fostering a deeper understanding of network communication, ICMPWatch empowers users to navigate the digital landscape with knowledge and integrity.


selam
merhaba
looking very cool