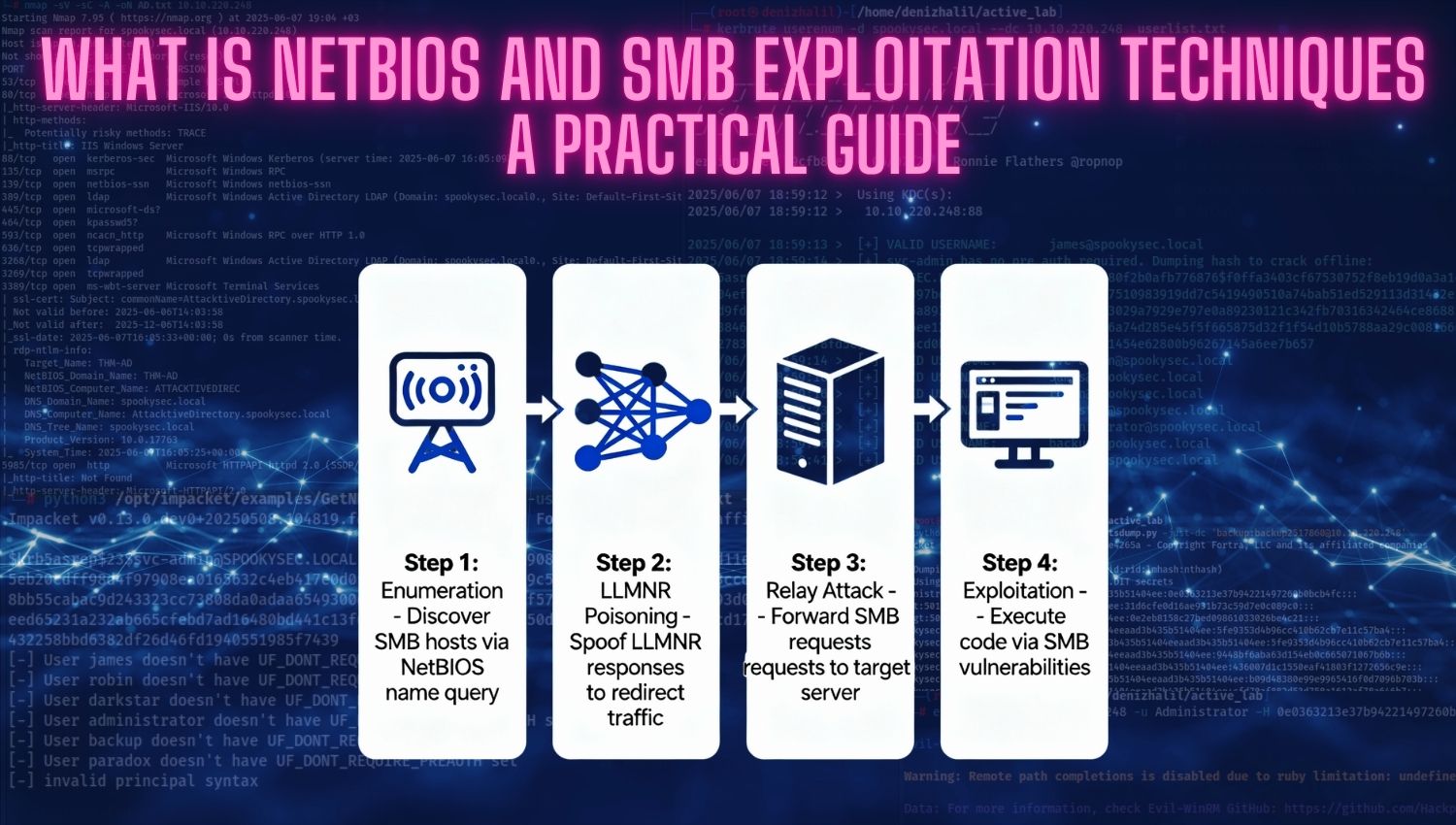
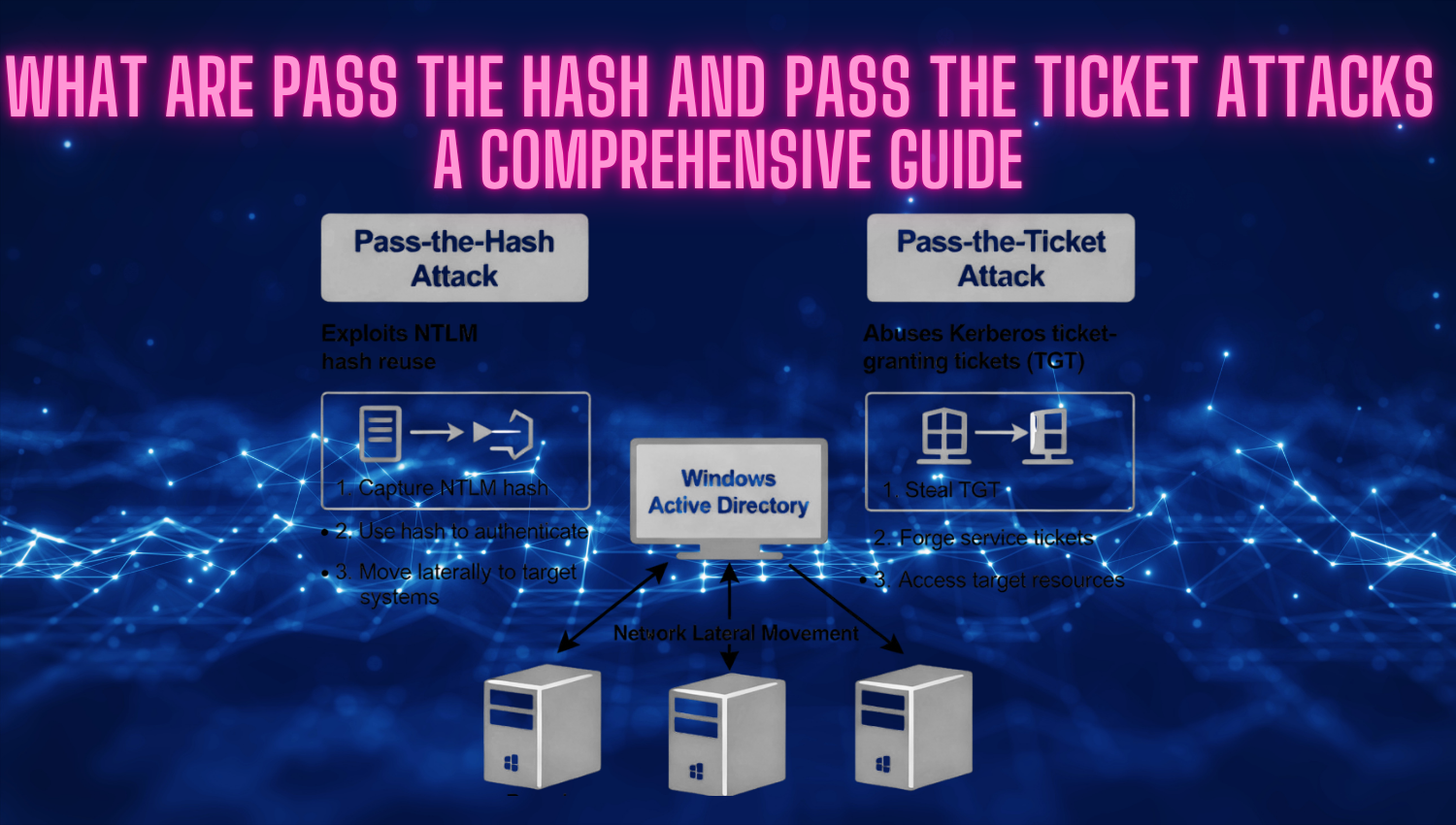
What is NetBIOS and SMB Exploitation Techniques: A Practical Guide
Introduction NetBIOS (Network Basic Input/Output System) and SMB (Server Message Block) are fundamental protocols that form the backbone of modern Windows networking environments. These protocols enable critical network functions including file sharing, printer access, and inter-process communication across enterprise systems. However, their widespread deployment and legacy compatibility features have made them frequent targets for attackers seeking unauthorized network access. Understanding how these protocols work, their inherent