Automatically Generated Malware with AI: Misuse of Artificial Intelligence
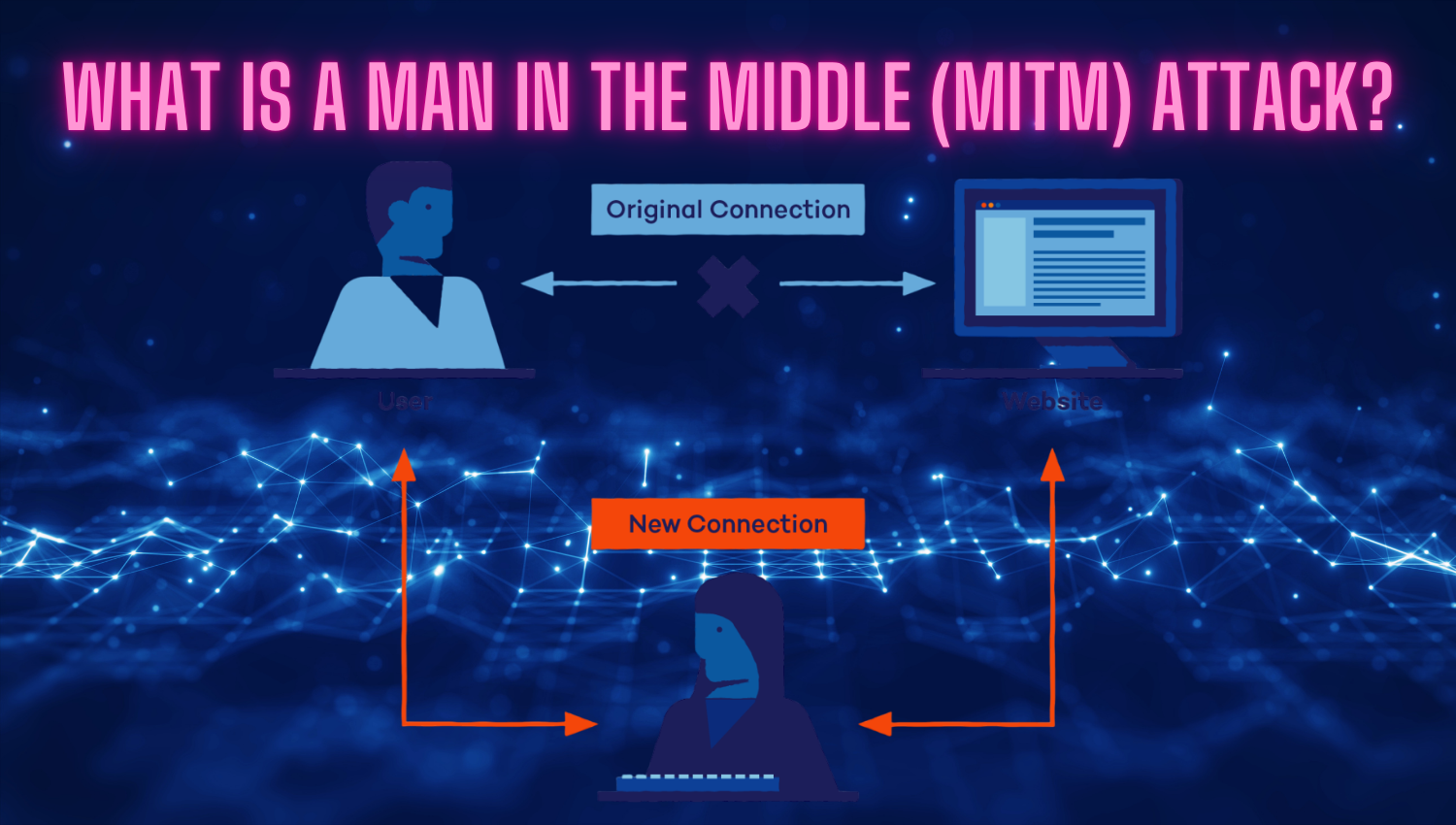
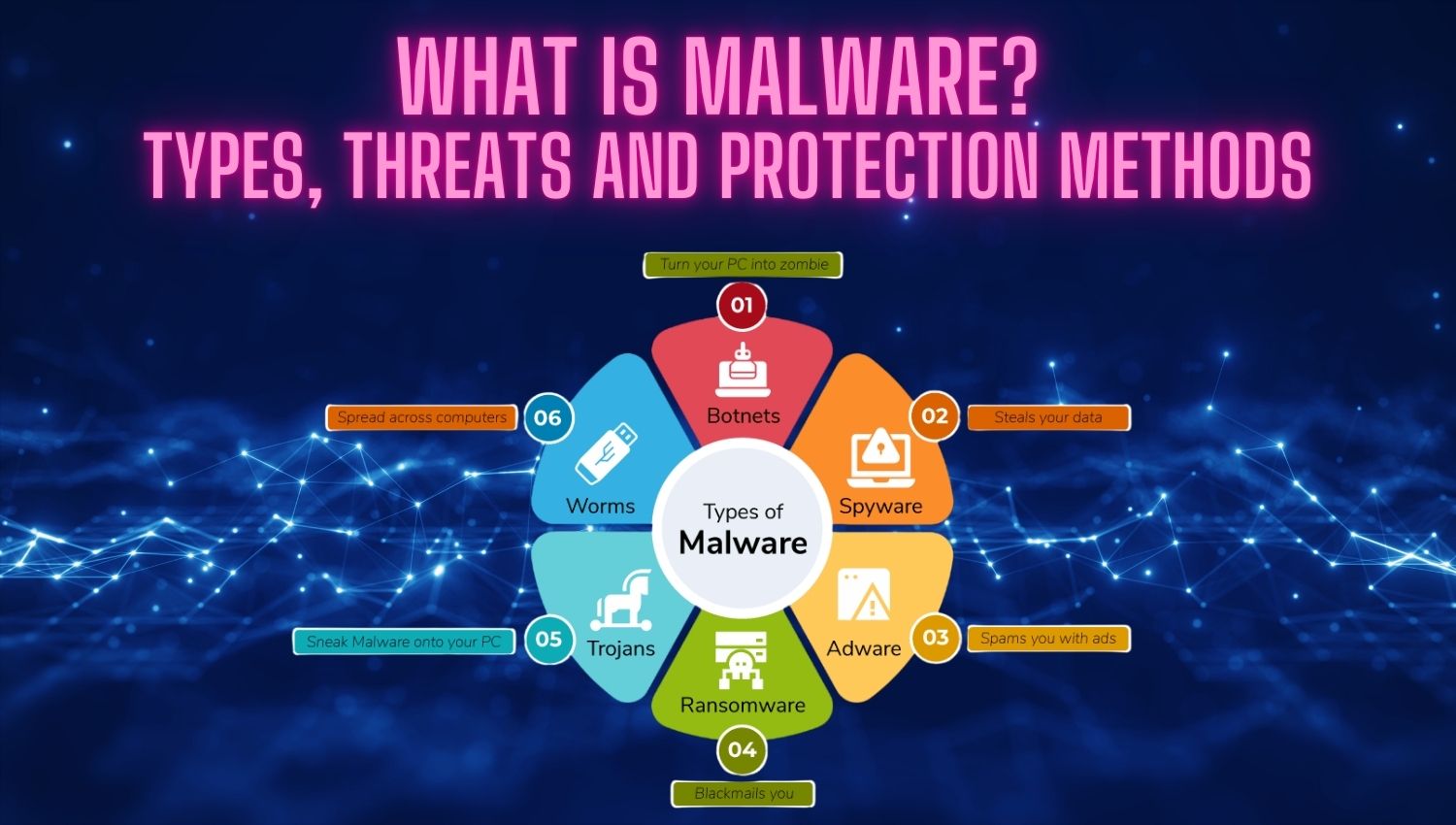
Introduction In recent years, artificial intelligence (AI) has introduced innovations that could fundamentally shake the cybersecurity world, while simultaneously giving rise to new and highly adaptive threats. Moving beyond classical malware development methods, automated and far more sophisticated malicious software systems powered by AI have provided threat actors with powerful tools to automate attacks, evolve malware code, and bypass traditional security barriers. The capabilities