Brute Force Attack on Login Pages Using Burp Suite
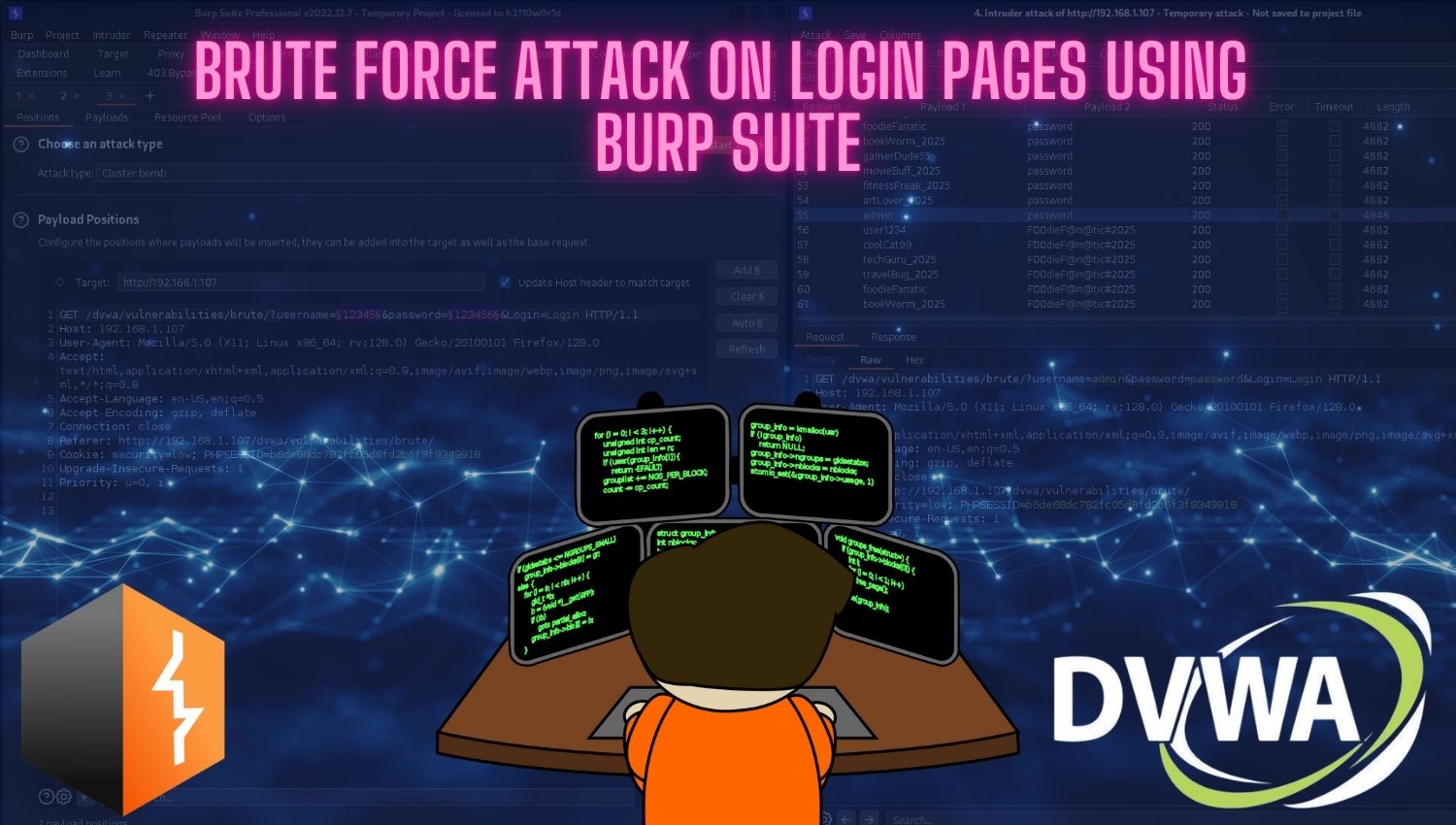
Introduction In today’s digital landscape, cybersecurity has become a critical concern for individuals and organizations alike. With the increasing use of web applications, cyberattacks targeting these platforms have also proliferated. Among the various types of attacks, brute force attacks are one of the simplest and most effective methods. In this article, we will explore how to conduct a brute force attack on