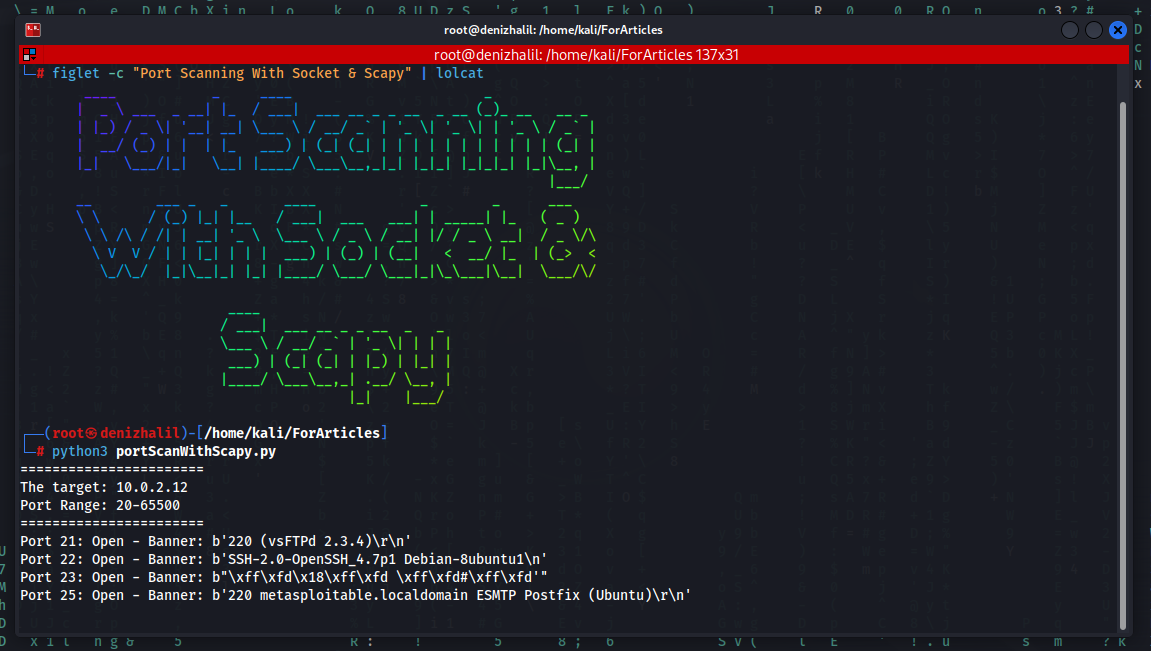
Port Scanning and Banner Retrieval with Scapy and Socket
When it comes to conducting security assessments and network reconnaissance, identifying open ports on target systems and retrieving banner information from those ports is crucial. In this article, we will explore how to perform port scanning and banner retrieval using the Python programming language with the Scapy and Socket libraries. Importing the Necessary Libraries First