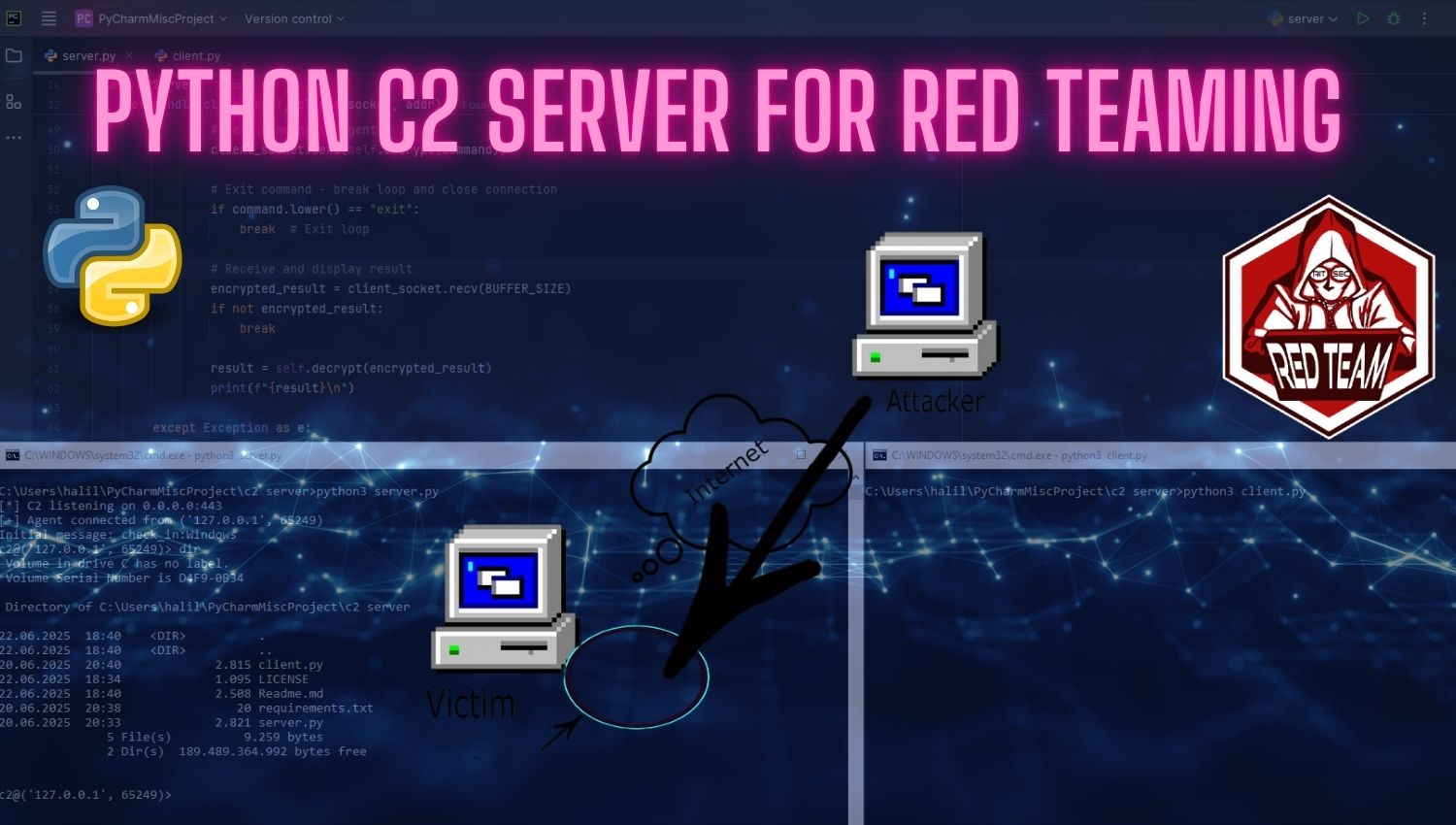
Python C2 Server for Red Teaming: A Comprehensive Hands-On Guide
Introduction In the evolving landscape of cybersecurity, Red Team operations have become essential for organizations seeking to assess their defensive capabilities against sophisticated threats. At the heart of these operations lies the Command & Control (C2) infrastructure, a critical component that enables security professionals to simulate adversarial tactics, techniques, and procedures in controlled environments. The Python-C2-Server-for-Red-Teaming project represents an accessible, open-source solution designed specifically for authorized