Network Keyword Detection Tool Using Scapy
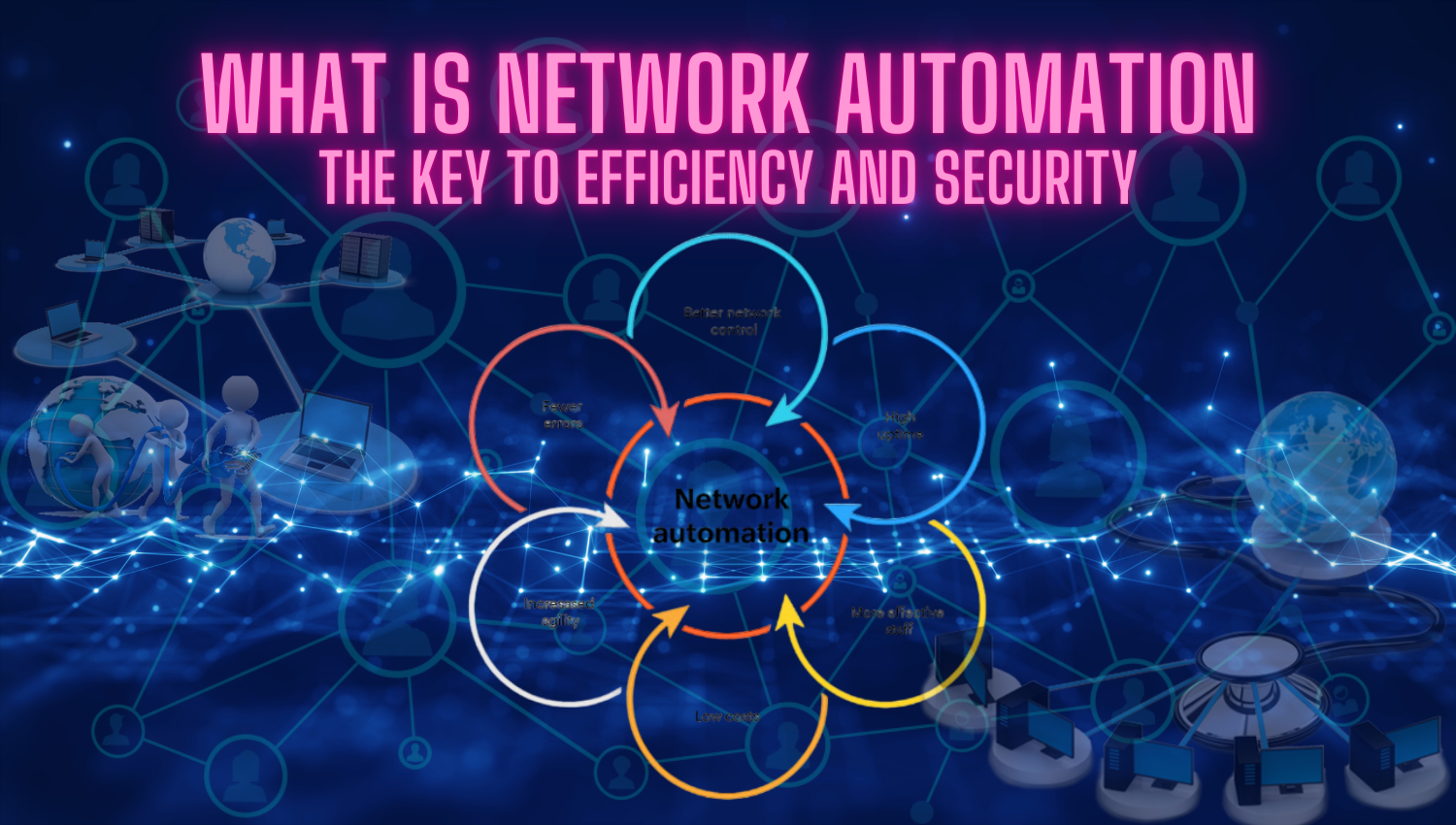
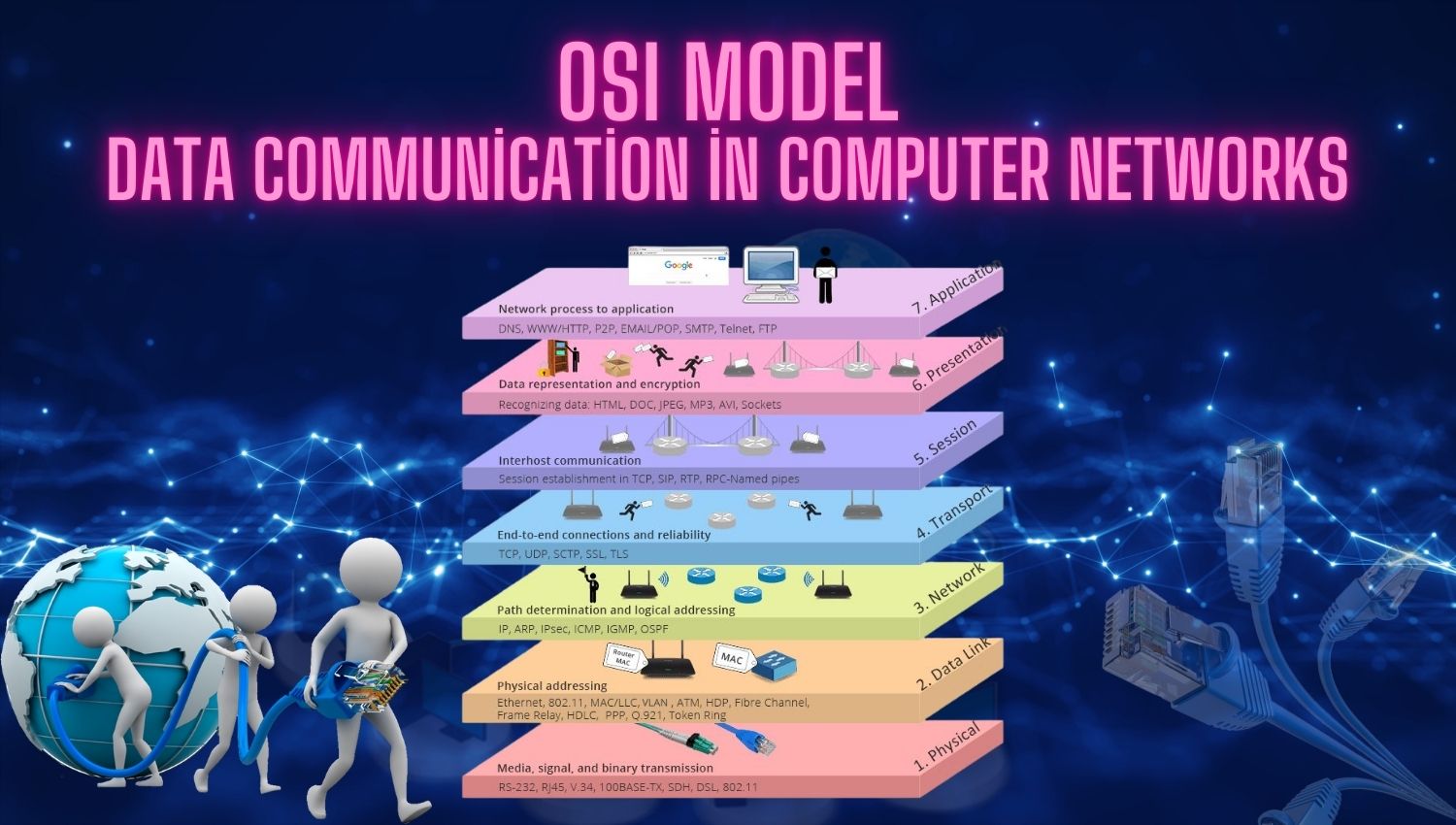
Introduction In today’s digital landscape, the importance of network security and monitoring cannot be overstated. As organizations increasingly rely on digital communication and data exchange, the volume of sensitive information transmitted over networks has surged. This trend has created a pressing need for effective tools that can analyze network traffic for specific patterns or keywords that may indicate security