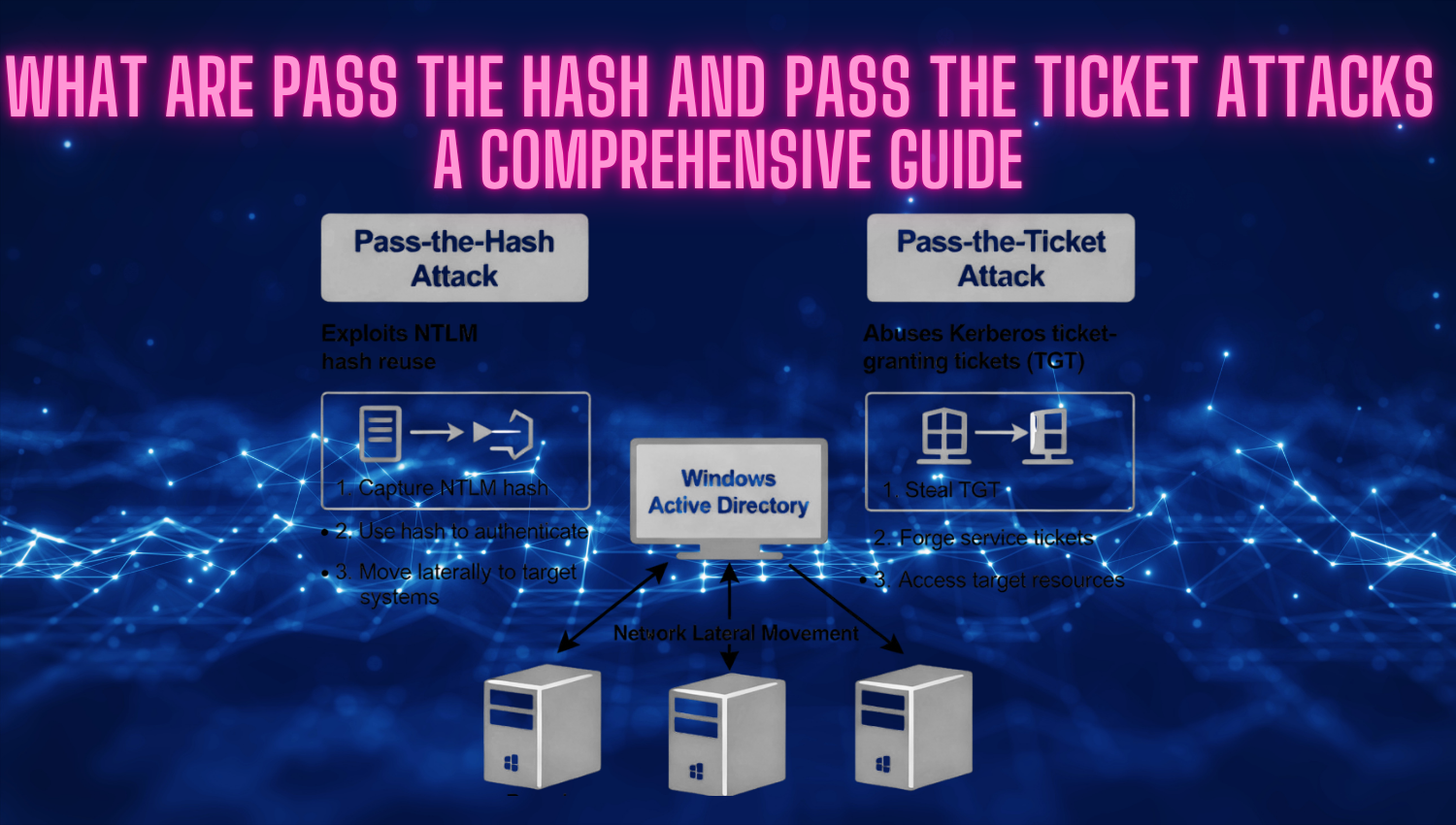
What are Pass-the-Hash and Pass-the-Ticket Attacks: A Comprehensive Guide
Introduction In contemporary cybersecurity, attackers continuously evolve their methods, moving beyond conventional password cracking and brute-force attacks to exploit the deeper weaknesses in authentication systems. Among the most serious threats to enterprise networks are Pass-the-Hash (PtH) and Pass-the-Ticket (PtT) attacks, which allow attackers to leverage stolen authentication material directly—whether in the form of hashed passwords or Kerberos tickets—without ever needing to obtain plaintext