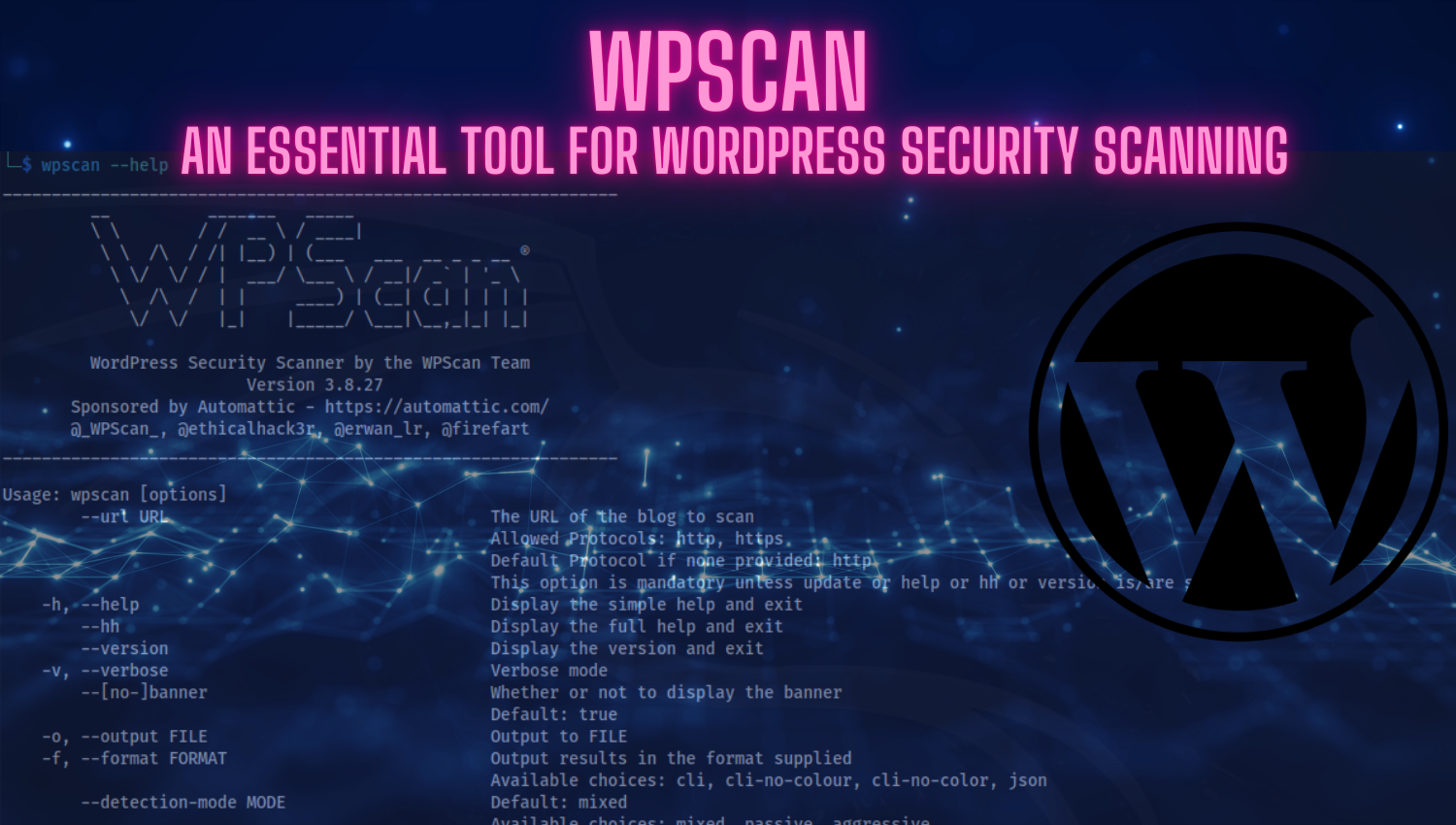
Building a Simple DNS Enumeration Tool in Python
Introduction The Domain Name System (DNS) is an essential component of internet infrastructure, translating human-readable domain names into IP addresses. Understanding how DNS works and being able to enumerate DNS records can provide crucial information for both system administrators and ethical hackers. In this article, we will develop a simple DNS enumeration tool in Python that queries different DNS record types (such