What is Malware: Threats and Protection Methods
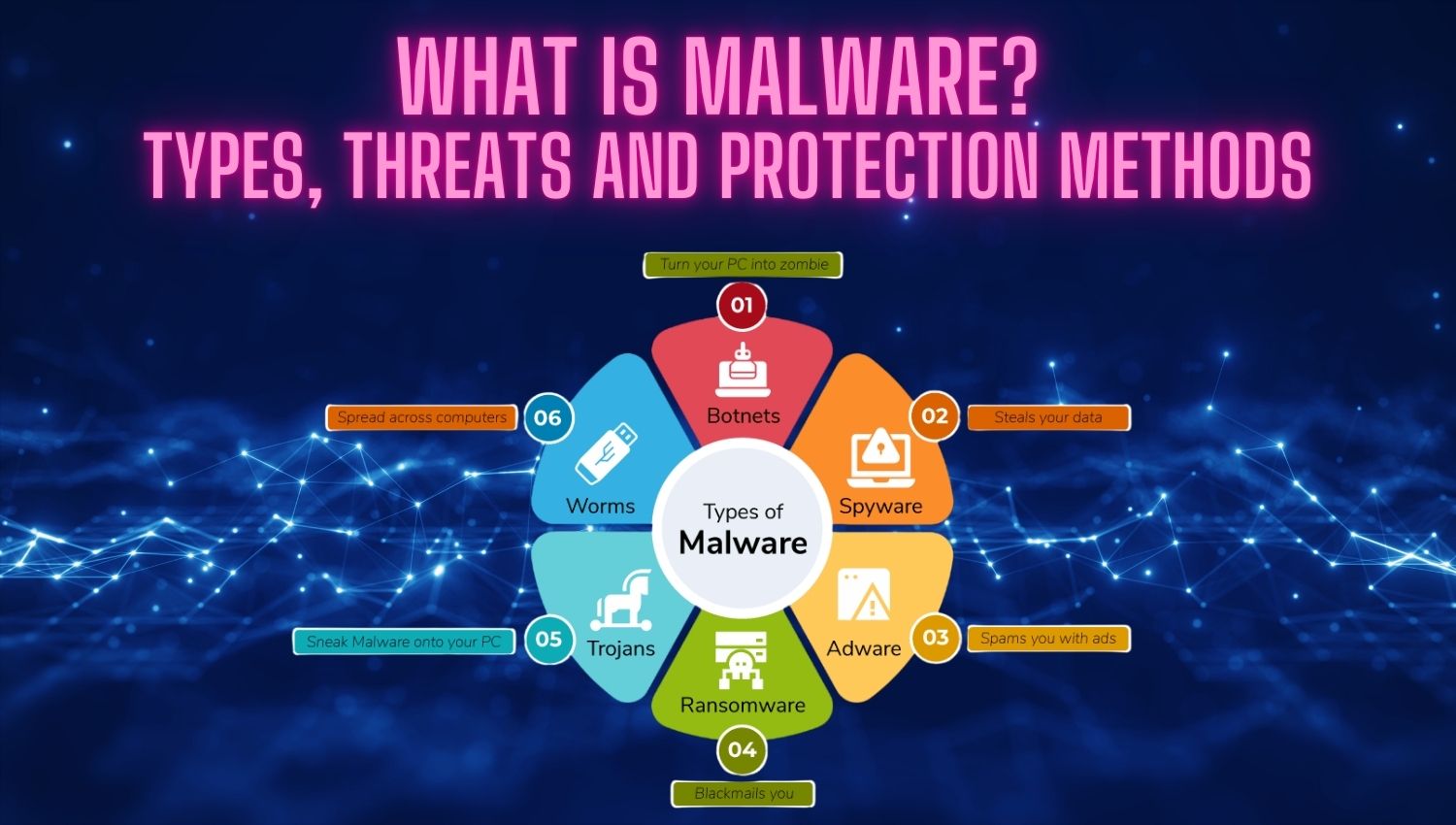
Introduction The rapid advancements of the digital age have undeniably transformed our lives, making everyday tasks more convenient and efficient. However, this technological progress has also introduced significant risks, particularly in the realm of cybersecurity. One of the most prevalent and dangerous threats in this landscape is malware, short for malicious software. Malware encompasses a wide array of software types specifically designed