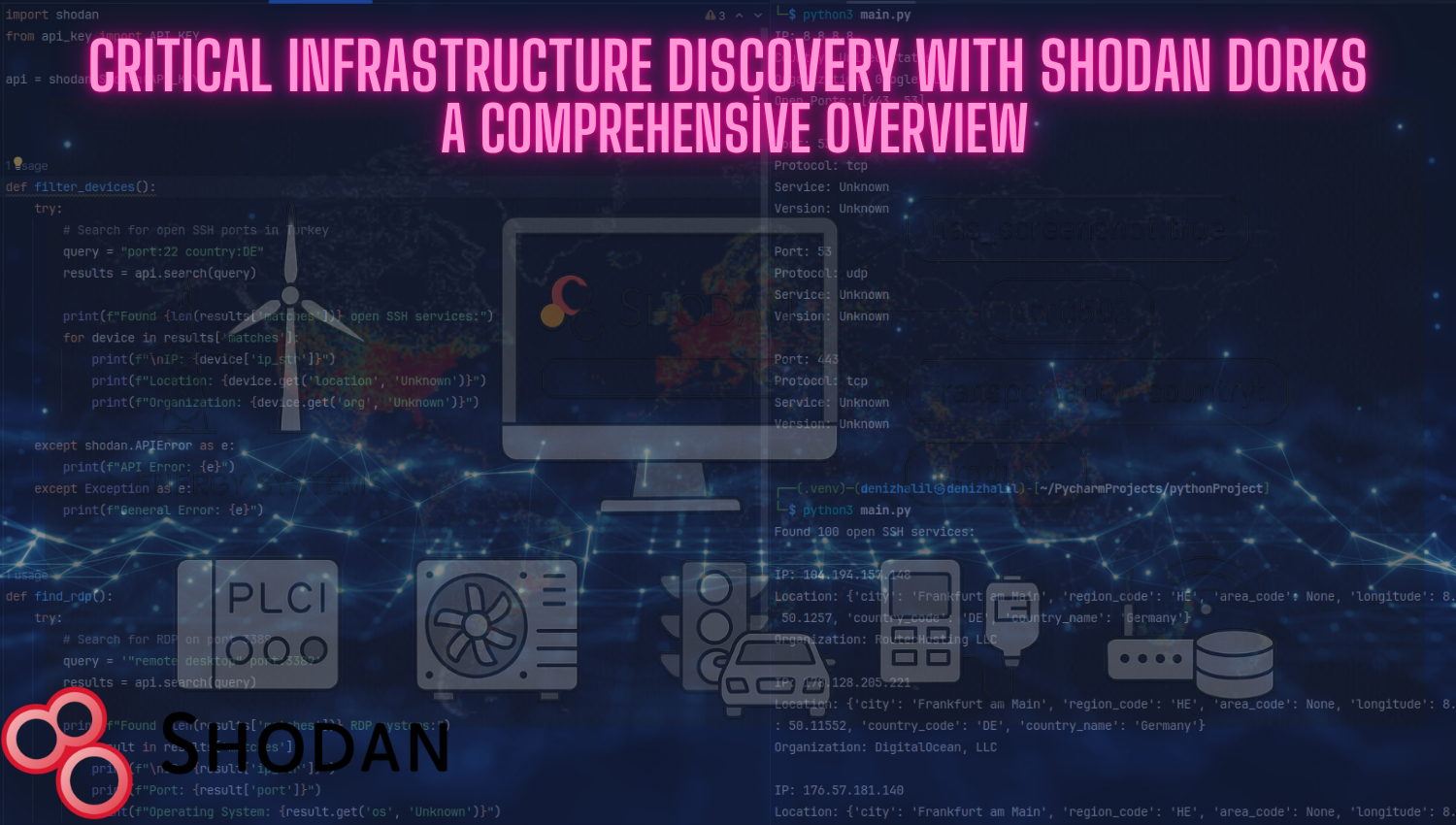
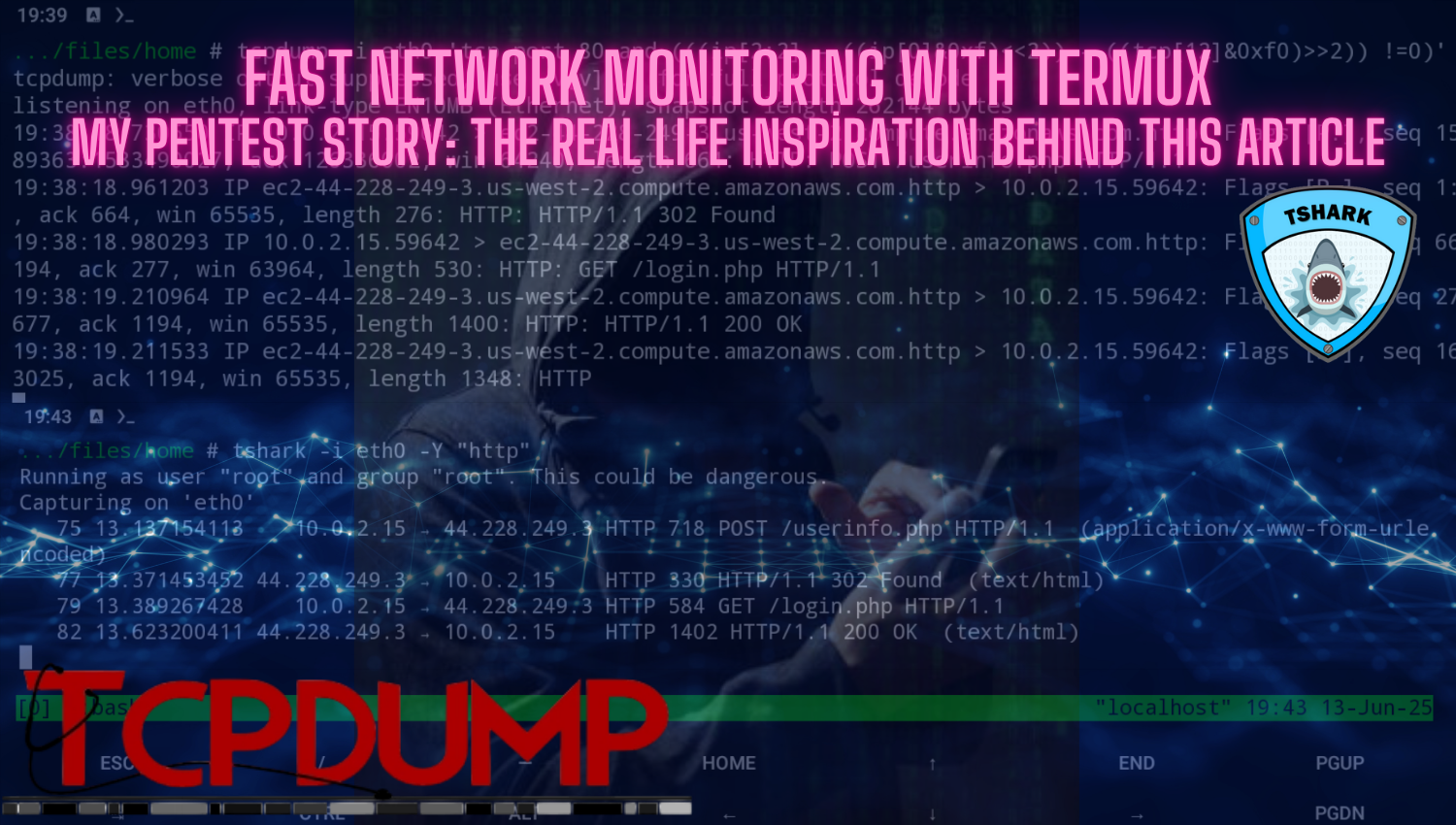
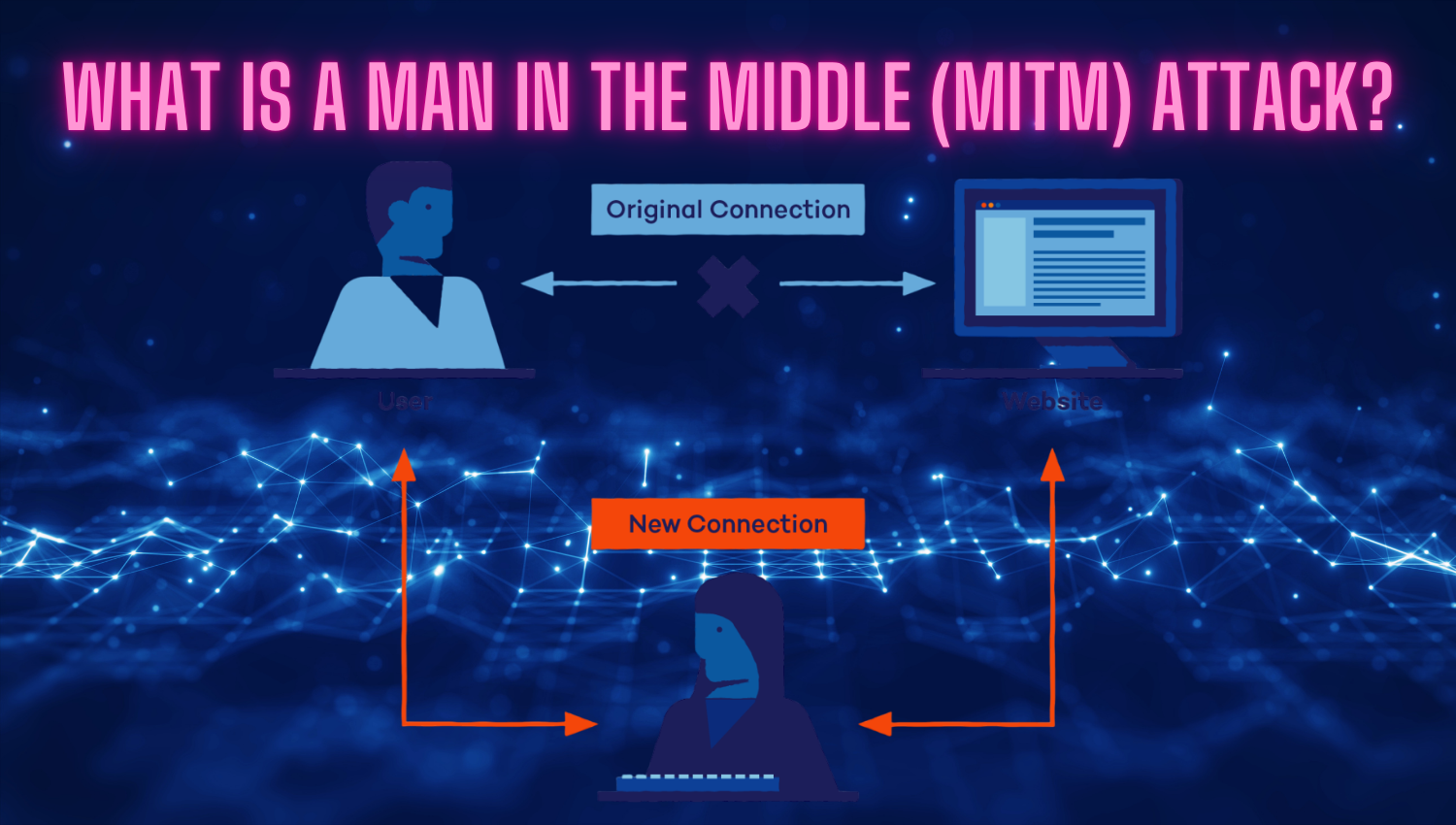
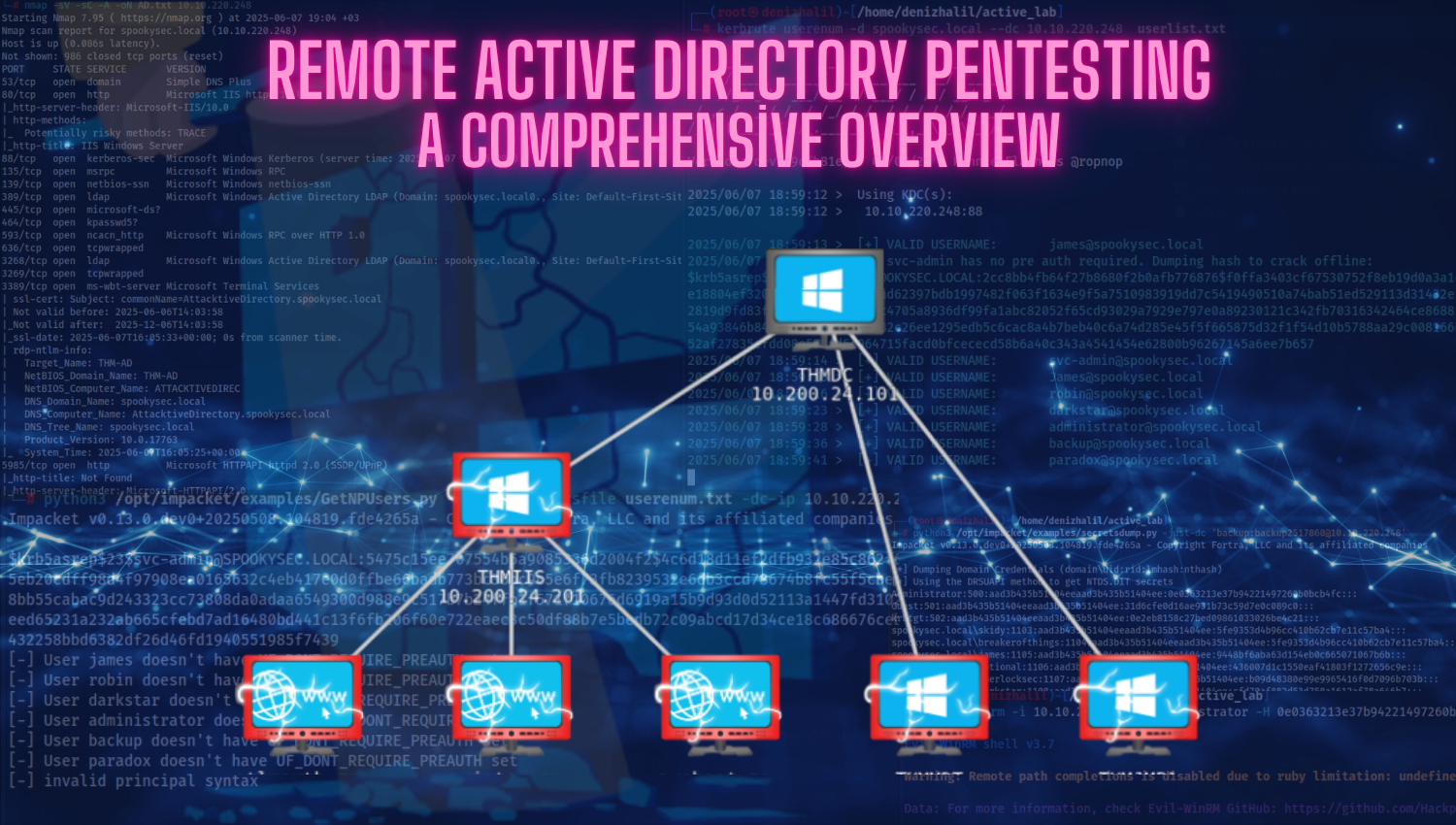
Linux Privilege Escalation Cheat Sheet: Techniques and Prevention
Introduction Linux privilege escalation is a critical security concern that involves exploiting vulnerabilities to gain unauthorized access to system resources. This technique is commonly used by attackers to elevate their privileges from a limited user account to the root user, allowing them full control over the system. The root user has unrestricted access, enabling them to modify system configurations, install