Introduction
Network monitoring is an essential practice in modern IT and cybersecurity, allowing organizations to maintain the health, performance, and security of their networks. As networks become increasingly complex, the need for effective monitoring tools has grown significantly. This guide will explore how to create a network monitoring tool using C++, focusing on capturing and analyzing UDP packets. By understanding how to monitor network traffic, professionals can detect anomalies, troubleshoot issues, and enhance overall network security.
Learning Objectives
By the end of this guide, readers will be able to:
- Understand the fundamentals of network monitoring and packet analysis.
- Utilize raw sockets in learn C++ style guide to capture UDP packets.
- Parse UDP headers to extract essential information such as source and destination IP addresses.
- Implement a command-line application for real-time network monitoring.
Network Monitoring with C++
C++ Network monitoring involves continuously observing network traffic to ensure smooth operation and security. It enables administrators to track key metrics such as bandwidth usage, packet loss, and latency. Effective monitoring is crucial for troubleshooting connectivity issues and responding swiftly to potential threats. In this project, we will focus on capturing UDP packets specifically. The User Datagram Protocol (UDP) operates at Layer 4 of the OSI model and is widely used for applications that require fast transmission without the overhead of establishing a connection.
C++ network programming is an excellent choice for developing network monitoring tools due to its performance and low-level access to system resources. By using raw sockets, we can capture all packets passing through a specified interface, regardless of their protocol type.
Project Purpose
The purpose of this project is to create a basic network monitoring tool that listens for incoming UDP packets on a specified network interface. The tool will parse UDP headers to retrieve source and destination IP addresses. This foundational knowledge serves as a stepping stone for further exploration into more sophisticated network analysis techniques.
Let’s Start Writing Our Code
Below is a complete implementation of a simple UDP network monitoring tool in C++ (dev cpp). This code captures packets using raw sockets and displays relevant information such as source and destination IP addresses. We will break down the code into manageable sections for better understanding.
Header Files and Buffer Definition:
#include <iostream>
#include <cstring>
#include <sys/socket.h>
#include <netinet/in.h>
#include <arpa/inet.h>
#include <unistd.h>
#define BUF_SIZE 2048#include <iostream>: Includes the standard input-output stream library for console output.#include <cstring>: Provides functions for handling C-style strings and memory.#include <sys/socket.h>: Contains definitions for socket programming.#include <netinet/in.h>: Defines structures for internet domain addresses.#include <arpa/inet.h>: Provides functions for converting IP addresses.#include <unistd.h>: Includes POSIX operating system API, particularly for closing sockets.#define BUF_SIZE 2048: Defines a constant buffer size of 2048 bytes for receiving packets.
IP Header Structure
// IP header structure
struct ip_header {
unsigned char ihl:4, version:4;
unsigned char tos;
unsigned short tot_len;
unsigned short id;
unsigned short frag_off;
unsigned char ttl;
unsigned char protocol;
unsigned short check; // checksum
struct in_addr ip_src, ip_dst; // source and destination IP addresses
};- This structure defines the fields of an IP header. Each field is represented with appropriate data types:
ihl: Internet Header Length (4 bits).version: IP version (4 bits).tos: Type of Service.tot_len: Total length of the packet.id: Identification field.frag_off: Fragment offset.ttl: Time to Live.protocol: Protocol used (e.g., TCP, UDP).check: Checksum for error-checking.ip_srcandip_dst: Source and destination IP addresses.
UDP Header Structure
// UDP header structure
struct udp_header {
unsigned short source_port;
unsigned short dest_port;
unsigned int seq_num;
unsigned int ack_num;
unsigned char data_offset:4, reserved:4;
unsigned char flags;
unsigned short window_size;
unsigned short checksum;
unsigned short urgent_pointer;
};- Similar to the IP header, this structure defines the fields of a TCP header:
source_portanddest_port: Port numbers for the source and destination.seq_numandack_num: Sequence and acknowledgment numbers for TCP communication.data_offset,reserved, andflags: Control information for TCP segments.window_size,checksum, andurgent_pointer: Flow control and error-checking fields.
Packet Processing Function
void process_packet(const char* buffer, ssize_t size) {
// Parse the IP header
struct ip_header* ip = (struct ip_header*)buffer;
// Parse the UDP header
struct udp_header * tcp = (struct tcp_header*)(buffer + sizeof(struct ip_header));
// Print IP information
std::cout << "Source IP: " << inet_ntoa(ip->ip_src)
<< " | Destination IP: " << inet_ntoa(ip->ip_dst)
<< " | Protocol: " << (int)ip->protocol
<< " | Packet Size: " << size << std::endl;
// Print TCP information
std::cout << "Source Port: " << ntohs(tcp->source_port)
<< " | Destination Port: " << ntohs(tcp->dest_port)
<< " | Sequence Number: " << ntohl(tcp->seq_num)
<< " | Acknowledgment Number: " << ntohl(tcp->ack_num)
<< " | Flags: " << (int)tcp->flags << std::endl;
}- The function
process_packettakes a buffer containing packet data and its size as parameters. - It parses the IP header from the beginning of the buffer and then parses the TCP header immediately following it.
- The function prints out:
- Source and destination IP addresses using
inet_ntoa. - Protocol number from the IP header.
- Packet size received.
- Source and destination IP addresses using
- For the TCP header, it prints:
- Source and destination ports using
ntohsto convert from network byte order to host byte order. - Sequence and acknowledgment numbers using
ntohl. - Flags set in the TCP header.
- Source and destination ports using
Main Function
int main() {
int sockfd;
char buffer[BUF_SIZE];
// Create socket
if ((sockfd = socket(AF_INET, SOCK_RAW, IPPROTO_TCP)) < 0) {
std::cerr << "Failed to create TCP socket!" << std::endl;
return 1;
}
std::cout << "TCP listener started." << std::endl;
while (true) {
// Receive message
ssize_t n = recv(sockfd, buffer, BUF_SIZE, 0);
if (n < 0) {
std::cerr << "Error receiving packet!" << std::endl;
continue;
}
process_packet(buffer, n);
}
close(sockfd);
return 0;
}- The main function initializes a raw socket using the Internet protocol family (
AF_INET) and specifies that it will capture TCP packets (SOCK_RAWwith protocol set toIPPROTO_TCP). - If socket creation fails, an error message is printed, and the program exits.
- The program enters an infinite loop where it waits to receive packets. It uses the
recvfunction to read data into the buffer. If an error occurs during reception, it prints an error message but continues listening for packets. - Upon successfully receiving a packet, it calls the
process_packetfunction to parse and display information about that packet. - Finally, when exiting (not shown here), it closes the socket to free resources.
This breakdown provides a comprehensive understanding of how each part of the code contributes to creating a basic UDP network monitoring tool in C++. By capturing raw packets and parsing their headers, you can gain insights into network traffic in real-time.
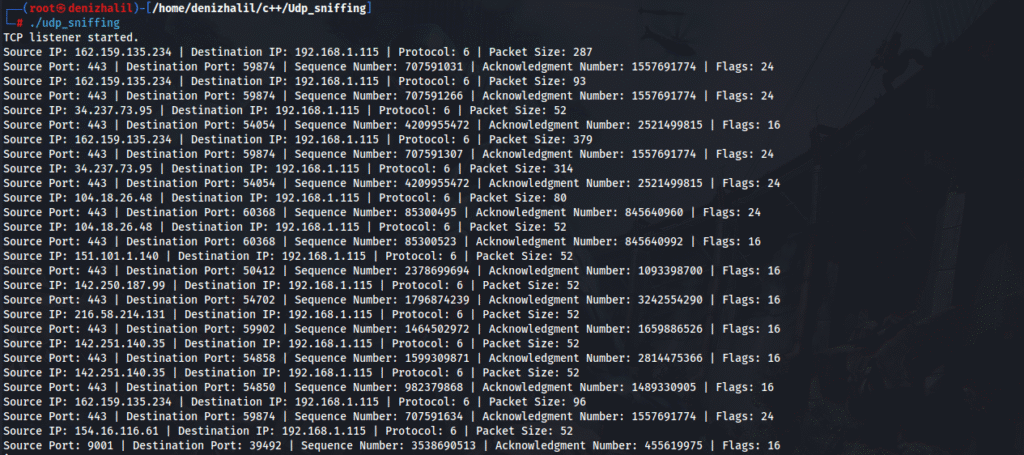
Conclusion
This guide has provided an overview of how to implement a basic UDP network monitoring tool using C++. By capturing and analyzing UDP packets in real-time, you can gain valuable insights into your network’s performance and security. Understanding these concepts is essential for anyone interested in enhancing their skills in network security or performance monitoring. With this foundation in place, readers can further explore advanced topics such as filtering specific traffic types based on protocols or ports or even building more sophisticated network monitoring tools that provide deeper insights into network behavior.

