Introduction
In the digital era, the rapid expansion of technology has brought new opportunities but also increased the complexity of cyber threats. With the proliferation of internet-connected devices and the rise of cloud computing, organizations are more vulnerable than ever to cyberattacks. Traditional security mechanisms, such as firewalls, antivirus programs, and signature-based detection methods, are becoming inadequate against sophisticated attacks that evolve rapidly. As cybercriminals adopt advanced techniques and exploit vulnerabilities, the need for adaptive, intelligent, and scalable solutions has grown exponentially.
Machine learning in cybersecurity has emerged as a key player in the fight against these evolving threats. By harnessing the power of machine learning (ML), systems can learn from vast amounts of data and identify patterns that human analysts or traditional tools might miss. This capability allows for proactive threat detection and response, significantly enhancing an organization’s security posture. In this article, we will explore how machine learning, specifically through artificial neural networks (ANNs), can be effectively applied to cybersecurity. We will also walk through the creation of a simple neural network using Python to demonstrate its classification capabilities, which are crucial for threat detection and prevention systems.
Learning Objectives
By the end of this article, readers will be able to:
- Understand the basics of machine learning and artificial neural networks.
- Recognize the role of ML in cybersecurity for detecting and preventing cyber threats.
- Implement a simple perceptron-based classification model using Python.
- Apply machine learning concepts to basic cybersecurity applications.
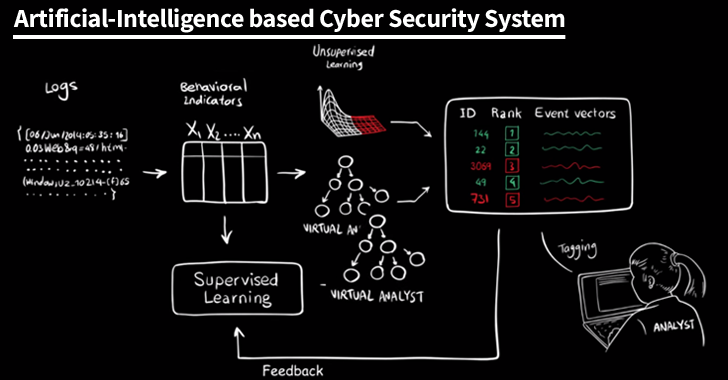
Machine Learning’s Role in Cybersecurity
Machine learning has become a transformative force in the realm of cybersecurity, particularly through the use of artificial neural networks (ANNs). These networks excel at identifying complex patterns in data, making them invaluable for various applications such as anomaly detection in network traffic and fraud detection. As cyber threats continue to evolve, the adaptability and efficiency of machine learning techniques are crucial for effective defense mechanisms.
- Malware Detection: One of the most prominent applications of machine learning in cybersecurity is malware detection. Traditional antivirus solutions often rely on signature-based detection methods, which can struggle to identify new or modified malware variants. In contrast, machine learning algorithms can analyze vast datasets of malware signatures and behavioral patterns to detect new, unseen threats. By employing techniques such as supervised learning, these models can be trained on labeled datasets containing both benign and malicious samples. This allows them to classify incoming files and flag potential malware more accurately and swiftly than traditional methods, significantly enhancing an organization’s ability to defend against malware attacks.
- Network Traffic Analysis: Machine learning also plays a vital role in network traffic analysis. With the increasing complexity of network environments, identifying unusual patterns that may indicate cyber attacks—such as Distributed Denial of Service (DDoS) attacks—has become more challenging. Machine learning models can process large volumes of network traffic data in real-time, learning the normal behavior of systems and users. When deviations from this norm are detected, the system can flag these anomalies for further investigation. This proactive approach not only helps in early detection but also reduces response times, allowing security teams to mitigate potential threats before they escalate into significant incidents.
- Anomaly Detection: Anomaly detection is another critical application of machine learning in cybersecurity. By training models on historical data, machine learning algorithms can learn what constitutes normal behavior within a system or network. This capability enables them to identify deviations that could signify potential security breaches or insider threats. For instance, if a user suddenly accesses sensitive files they typically do not interact with, or if there is an unusual spike in outbound traffic, the system can alert security personnel to investigate further. This method enhances situational awareness and allows organizations to respond quickly to potential threats.
- Phishing Prevention: Phishing attacks remain one of the most prevalent forms of cyber threats today. Machine learning can significantly enhance phishing prevention efforts by analyzing email headers, body content, and other characteristics to identify potentially harmful messages. By training models on datasets containing both phishing and legitimate emails, these systems can learn to differentiate between harmless communications and those designed to deceive users into providing sensitive information. Additionally, machine learning algorithms can be employed to evaluate URLs embedded within emails, flagging those that exhibit suspicious behavior or are known to be associated with phishing attempts.
- Automated Threat Response: Finally, machine learning facilitates automated threat response, which is essential for organizations aiming to maintain robust cybersecurity defenses amidst a growing number of threats. By integrating machine learning into security operations centers (SOCs), organizations can automate routine tasks such as log analysis and threat intelligence triaging. This automation not only improves efficiency but also allows human analysts to focus on more complex tasks that require critical thinking and expertise. By leveraging machine learning for real-time threat detection and response, organizations can enhance their overall security posture and reduce the risk of data breaches.
Project Objective
In this section, we will outline the primary objective of our project. This project aims to provide an opportunity to understand and implement data classification methods using machine learning, particularly through the use of artificial neural networks (ANNs). We will create a simple perceptron model using the Iris dataset, which will help us grasp the fundamental principles of machine learning and classification problems. Additionally, this project will illustrate how these methods can be adapted for applications in cybersecurity. By the end of the project, readers are expected to have a foundational understanding of machine learning and ANNs, as well as insights into how they can be applied within the realm of cybersecurity.
Mastering Advanced Python from Scratch to Advanced
Unlock the full potential of Python with this comprehensive guide, spanning 227 pages and 50 chapters. From advanced techniques like metaprogramming.
-5% 25 on buymeacoffeeLet’s Start Coding: A Perceptron Model on the Iris Dataset
Although this example uses the Iris dataset, the core principles can be adapted to cybersecurity applications. We’ll implement a basic perceptron—a type of artificial neural network—to solve a classification problem. Here’s how you can do it step-by-step using Python and the Scikit-learn library.
1. Loading Necessary Libraries:
from sklearn.datasets import load_iris
from sklearn.model_selection import train_test_split
from sklearn.linear_model import Perceptron
from sklearn.metrics import accuracy_scoreWe begin by importing the necessary libraries: load_iris to load the dataset, train_test_split to split the data into training and test sets, Perceptron to create the neural network model, and accuracy_score to evaluate our model’s performance.
2. Loading and Preparing the Dataset:
# Load the Iris dataset
iris = load_iris()
X, y = iris.data, iris.target
# Split the dataset into training and test sets
X_train, X_test, y_train, y_test = train_test_split(X, y, test_size=0.3, random_state=42)Here, we load the Iris dataset, assign the features to X, and the labels (flower species) to y. The data is split into 70% training and 30% test sets to allow model evaluation.
3. Creating and Training the Model:
# Create the Perceptron model
clf = Perceptron(tol=1e-3, random_state=0)
# Train the model with training data
clf.fit(X_train, y_train)Next, we instantiate a Perceptron model and train it using badthe fit method with the training data. The tol parameter controls the stopping criteria, and random_state ensures consistent results.
Mastering Python for Ethical Hacking: A Comprehensive Guide to Building 50 Hacking Tools
Let’s embark on this journey together, where you will learn to use Python not just as a programming language, but as a powerful weapon in the fight against cyber threats
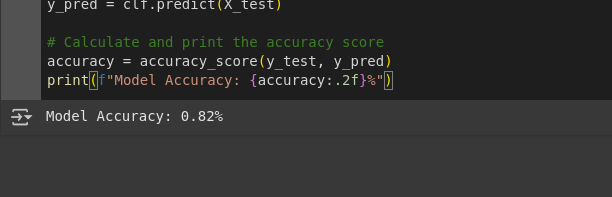
-45% $25 on buymeacoffee4. Testing the Model and Evaluating Accuracy:
# Make predictions on the test data
y_pred = clf.predict(X_test)
# Calculate and print the accuracy score
accuracy = accuracy_score(y_test, y_pred)
print(f"Model Accuracy: {accuracy:.2f}%")Finally, we test the model on the test data using the predict method and calculate the accuracy using accuracy_score. This gives a quick snapshot of the model’s performance.
Conclusion
Machine learning, particularly artificial neural networks, has immense potential in enhancing cybersecurity systems. The example provided in this article, which uses a simple classification model, demonstrates the foundational principles of machine learning and its application in classification problems. However, more complex and tailored models can address specific cybersecurity threats, such as detecting malware, phishing attempts, and abnormal network behaviors. These advanced models can be trained on vast datasets to identify sophisticated patterns that may elude traditional security tools. The ongoing development of machine learning techniques will continue to revolutionize how we approach cybersecurity, making it an indispensable tool in defending against evolving cyber threats. As technology advances and cyberattacks become more sophisticated, the adaptability and scalability of machine learning algorithms will play a crucial role in maintaining robust cybersecurity defenses. By integrating machine learning into security operations centers (SOCs), organizations can automate routine tasks, enhance threat detection capabilities, and improve response times, ultimately strengthening their overall security posture.
In conclusion, the future of cybersecurity is deeply intertwined with the advancements in machine learning and artificial neural networks. By leveraging these technologies, organizations can build proactive defense mechanisms that are capable of adapting to new threats as they emerge, ensuring a safer digital environment for all users.