Introduction
In today’s rapidly evolving cybersecurity landscape, ransomware attacks have become a significant threat. RansomwareSim is a tool designed to simulate how ransomware works, offering a safe environment for educational and training purposes. This simulation allows individuals to understand the mechanisms of ransomware and better prepare against such attacks. This article introduces the RansomwareSim project, explains its key features, and walks you through the steps to download and use it. The RansomwareSim ransomware simulator is essential for understanding these threats safely.
Learning Objectives
By the end of this article, you will learn:
- The purpose and structure of the RansomwareSim project.
- How ransomware encrypts files and communicates with a command-and-control server.
- Key features of the RansomwareSim tool.
- How to set up and run the simulator in a controlled environment.
What is the RansomwareSim Project?
RansomwareSim is a simulated ransomware application built to demonstrate the behavior of ransomware in a secure and controlled environment. It encrypts specified files within a target directory and simulates communication with a command-and-control (C2) server. It is a valuable tool for cybersecurity training, helping users understand how real ransomware operates without the risk of causing actual harm. However, it is important to emphasize that this tool should only be used in authorized environments for learning purposes, Creating Ransomware with Python | Part 1. The RansomwareSim ransomware simulator ensures a safe learning experience.
How Does RansomwareSim Work?
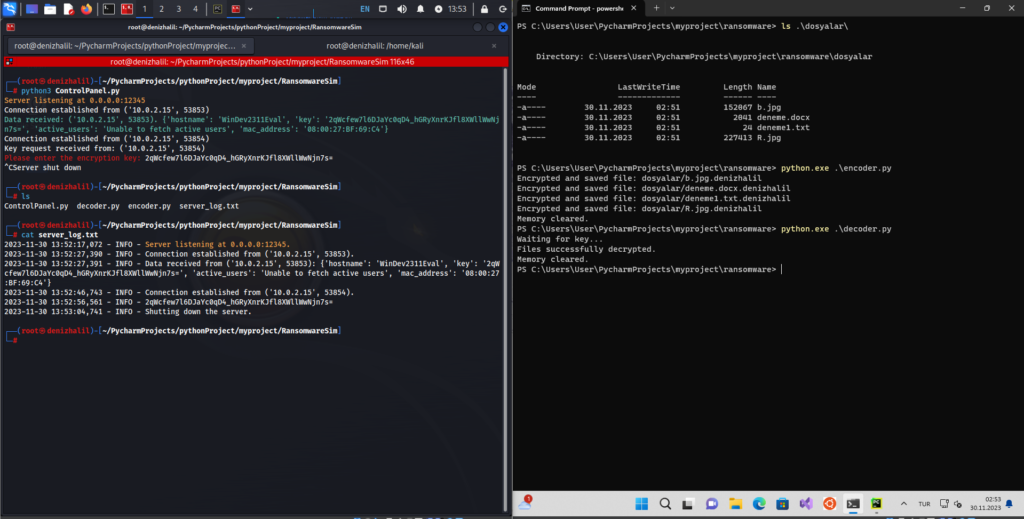
The RansomwareSim tool works by encrypting files in a designated directory and creating a ransom note to simulate an actual ransomware attack. Here’s how it functions:
- File Encryption: RansomwareSim scans the specified directory for certain file types and encrypts them using secure cryptographic methods.
- Desktop Wallpaper Change: On Windows systems, the tool changes the desktop wallpaper to imitate how ransomware typically displays ransom notes.
- Simulated Ransom Note: It creates a README file on the desktop with a ransom note, instructing the user on how to decrypt the files.
- Communication with a C2 Server: RansomwareSim connects to a simulated C2 server, sending system data and receiving a decryption key.
- Decryption Process: Once the correct decryption key is provided through the server, RansomwareSim decrypts the files.
This process provides a complete simulation of how real ransomware behaves, giving users valuable insight into the ransomware life cycle. Using the RansomwareSim ransomware simulator, you can safely observe these mechanisms.
Key Features of RansomwareSim
RansomwareSim includes the following features:
- File Encryption: Encrypts specified file types in a target directory.
- Simulated Ransom Note: Creates a README file with instructions.
- C2 Communication: Simulates communication with a server to retrieve a decryption key.
- Decryption Mechanism: Files can be decrypted after the correct key is received.
- Wallpaper Modification (Windows): Changes the wallpaper to display the ransom note. These features make the RansomwareSim ransomware simulator invaluable.
These features make RansomwareSim an ideal tool for demonstrating ransomware attacks in a non-malicious, controlled environment.
Downloading RansomwareSim from GitHub
You can download RansomwareSim from GitHub and run it on your machine. Below are the steps to get started:
- Step 1: Clone the Repository Start by cloning the RansomwareSim repository from GitHub:
git clone https://github.com/HalilDeniz/RansomwareSim.git- Step 2: Navigate to the Project Directory Once cloned, navigate to the project folder:
$ cd RansomwareSim/- Step 3: Install Dependencies RansomwareSim requires specific Python libraries. Install the necessary dependencies using the following command:
pip install -r requirements.txt- Step 4: Run the Control Server The control server simulates the command-and-control functionality. Open
controlpanel.pyand run the script to start the server. - Step 5: Start the Ransomware Simulator Navigate to the directory containing
encoder.py, modify the main function to specify your target directory, and run the script to start the ransomware simulation. - Step 6: Decrypting Files After the files are encrypted, you can use
decoder.pyto input the decryption key and restore the files. The entire process can be safely tested with the RansomwareSim ransomware simulator.
Conclusion
RansomwareSim offers a powerful tool for understanding the mechanisms behind ransomware attacks in a safe, controlled environment. By simulating ransomware behavior, users can gain practical experience with how ransomware operates and better prepare for defending against these types of attacks. Always ensure ethical and legal use of this tool and never deploy it on unauthorized systems. The RansomwareSim ransomware simulator community on Discord can provide additional support and insights.
