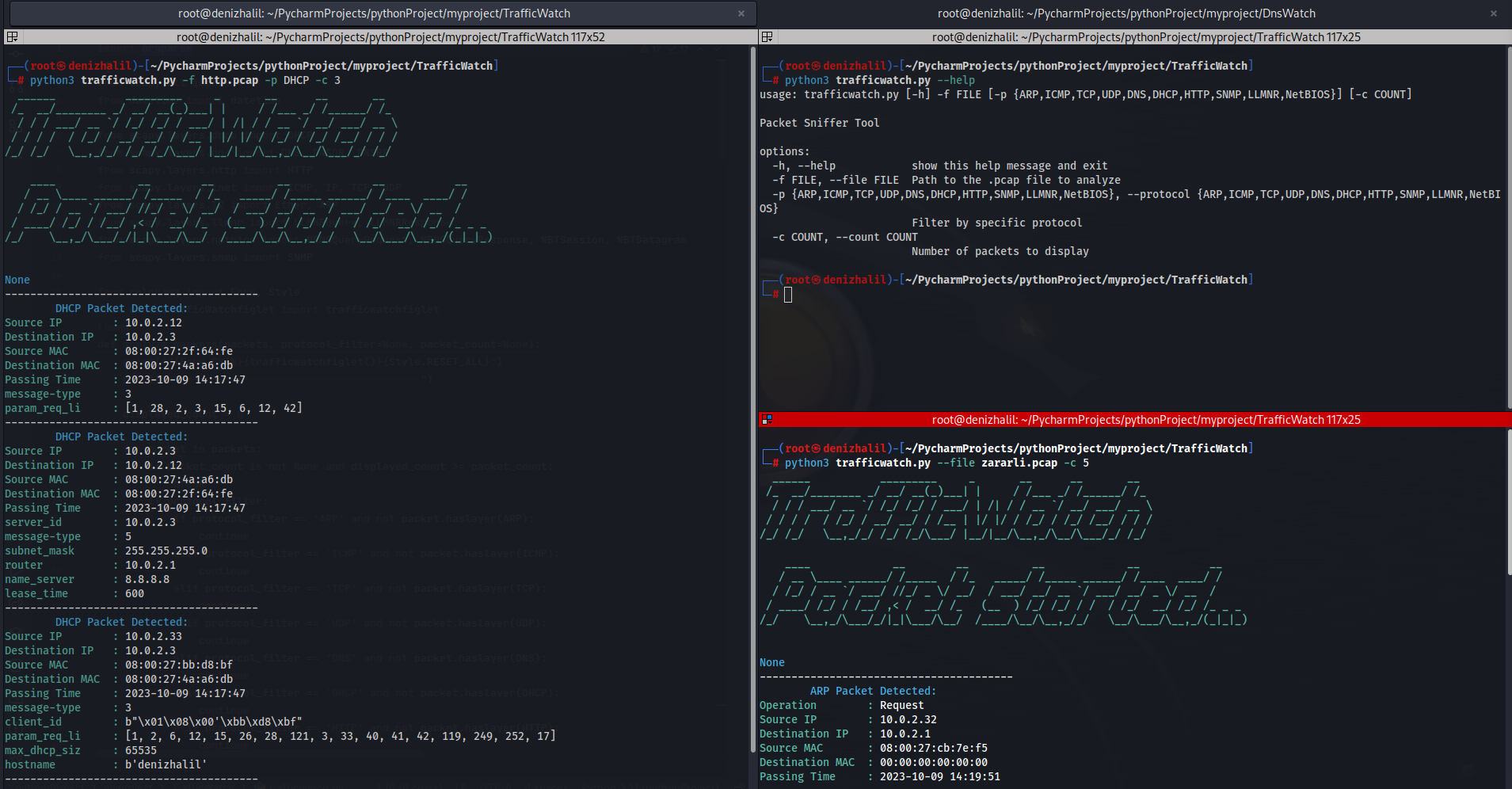
TrafficWatch, a packet sniffer tool, allows you to monitor and analyze network traffic from PCAP files or live network interfaces. It provides insights into various network protocols and can help with network troubleshooting, security analysis, and more.
Features
- Packet capture from PCAP files or live network interfaces.
- Protocol-specific packet analysis for ARP, ICMP, TCP, UDP, DNS, DHCP, HTTP, SNMP, LLMNR, and NetBIOS.
- Packet filtering based on protocol, source IP, destination IP, source port, destination port, and more.
- Summary statistics on captured packets.
- Interactive mode for in-depth packet inspection.
- Timestamps for each captured packet.
- User-friendly colored output for improved readability.
Requirements
- Python 3.x
- scapy
- argparse
- pyshark
- colorama
Installation
- Clone the repository:
git clone https://github.com/HalilDeniz/TrafficWatch.git- Navigate to the project directory:
cd TrafficWatch- Install the required dependencies:
pip install -r requirements.txtUsage
python3 trafficwatch.py --help
usage: trafficwatch.py [-h] -f FILE [-p {ARP,ICMP,TCP,UDP,DNS,DHCP,HTTP,SNMP,LLMNR,NetBIOS}] [-c COUNT]
Packet Sniffer Tool
options:
-h, --help show this help message and exit
-f FILE, --file FILE Path to the .pcap file to analyze
-p {ARP,ICMP,TCP,UDP,DNS,DHCP,HTTP,SNMP,LLMNR,NetBIOS}, --protocol {ARP,ICMP,TCP,UDP,DNS,DHCP,HTTP,SNMP,LLMNR,NetBIOS}
Filter by specific protocol
-c COUNT, --count COUNT
Number of packets to displayIf you only want to scan a single protocol
python trafficwatch.py -f path/to/your.pcap -p DHCPTo analyze packets from a PCAP file, use the following command:
python trafficwatch.py -f path/to/your.pcapTo specify a protocol filter (e.g., HTTP) and limit the number of displayed packets (e.g., 10), use:
python trafficwatch.py -f path/to/your.pcap -p HTTP -c 10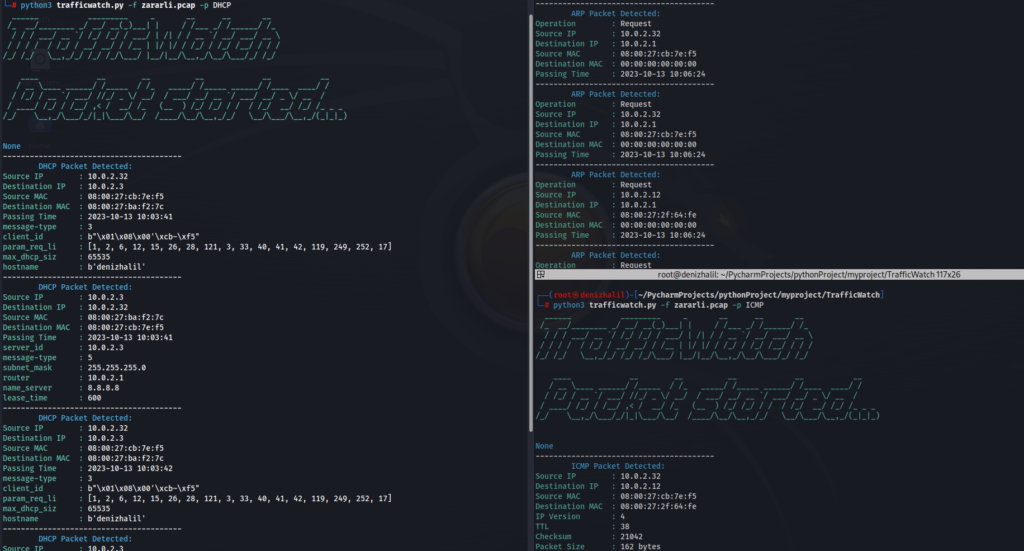
Options
-for--file: Path to the PCAP file for analysis.-por--protocol: Filter packets by protocol (ARP, ICMP, TCP, UDP, DNS, DHCP, HTTP, SNMP, LLMNR, NetBIOS).-cor--count: Limit the number of displayed packets.
Contributing
Contributions are welcome! If you want to contribute to TrafficWatch
Contact
If you have any questions, comments, or suggestions about TrafficWatch, please feel free to contact me:
- LinkedIn: Halil Ibrahim Deniz
- TryHackMe: Halilovic
- Instagram: deniz.halil333
- YouTube: Halil Deniz
- Email: halildeniz313@gmail.com
License
This project is licensed under the MIT License.