What is SNMP Security and Exploitation: A Comprehensive Guide
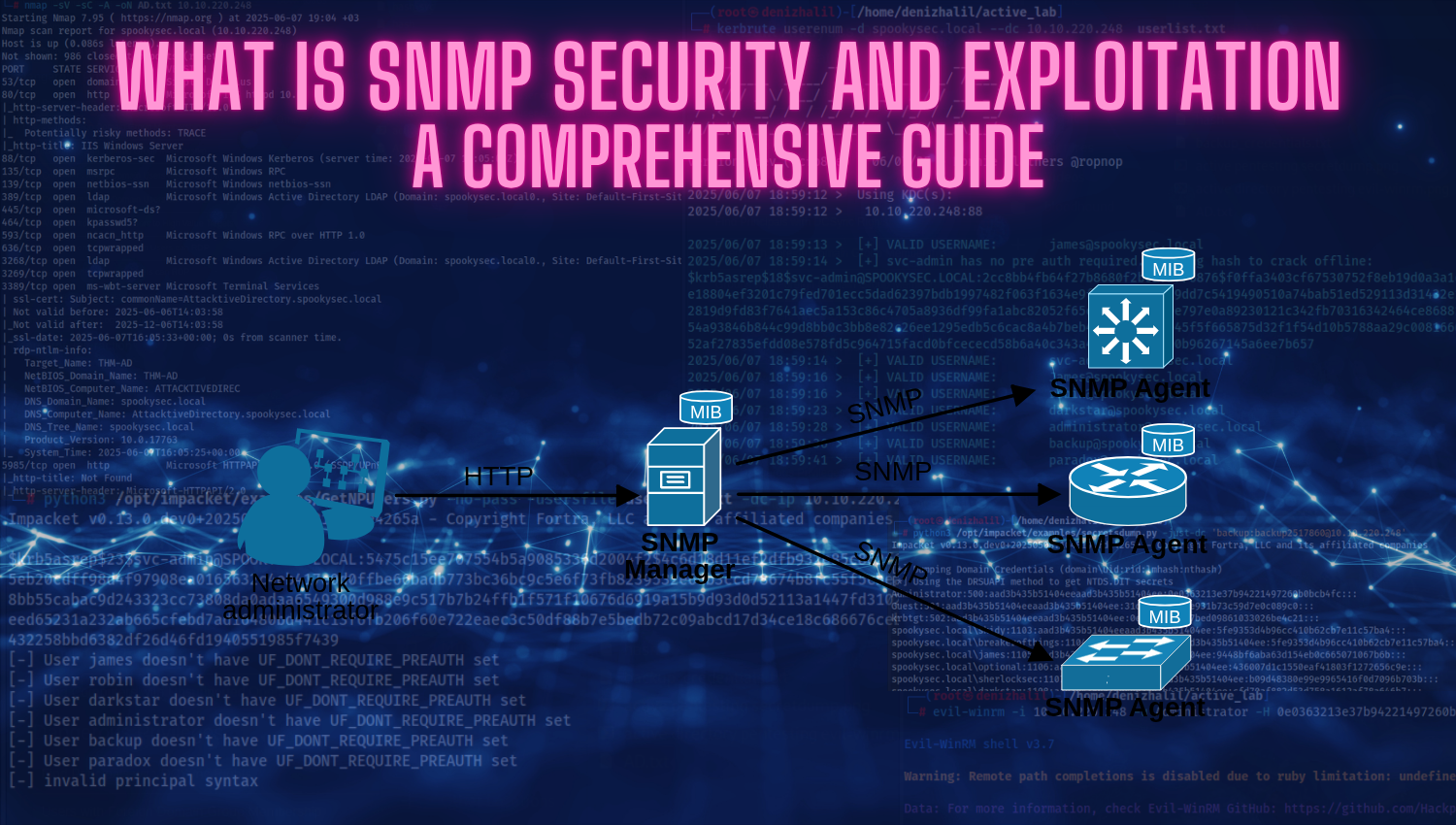
Introduction Simple Network Management Protocol (SNMP) has stood as the cornerstone of network device management since its introduction in the late 1980s, empowering administrators to monitor and control devices ranging from switches and routers to firewalls, servers, and the expanding realm of IoT infrastructure. SNMP’s efficiency, universal support, and lightweight design helped it become a global standard—enabling centralized visibility into network health and