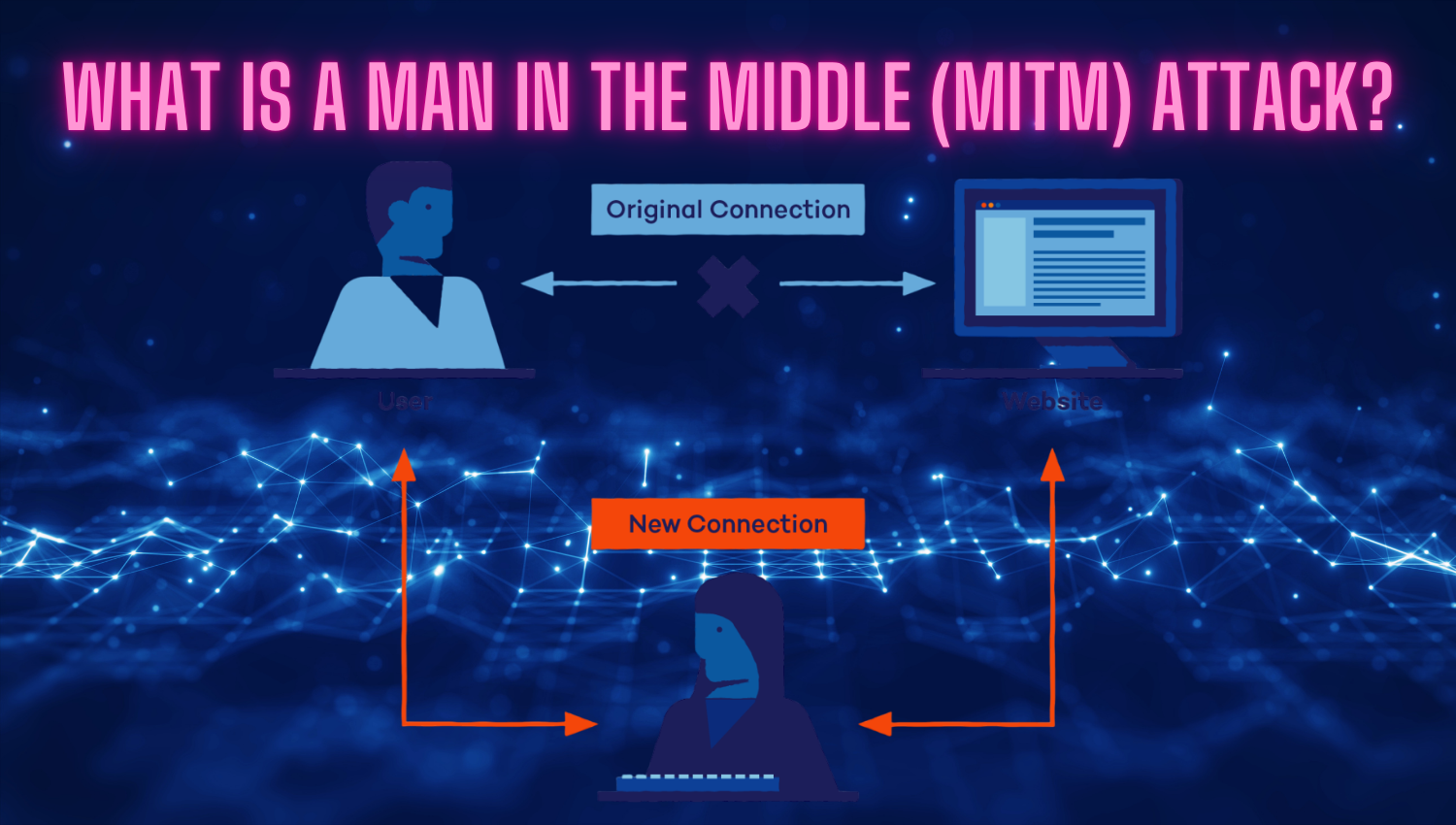
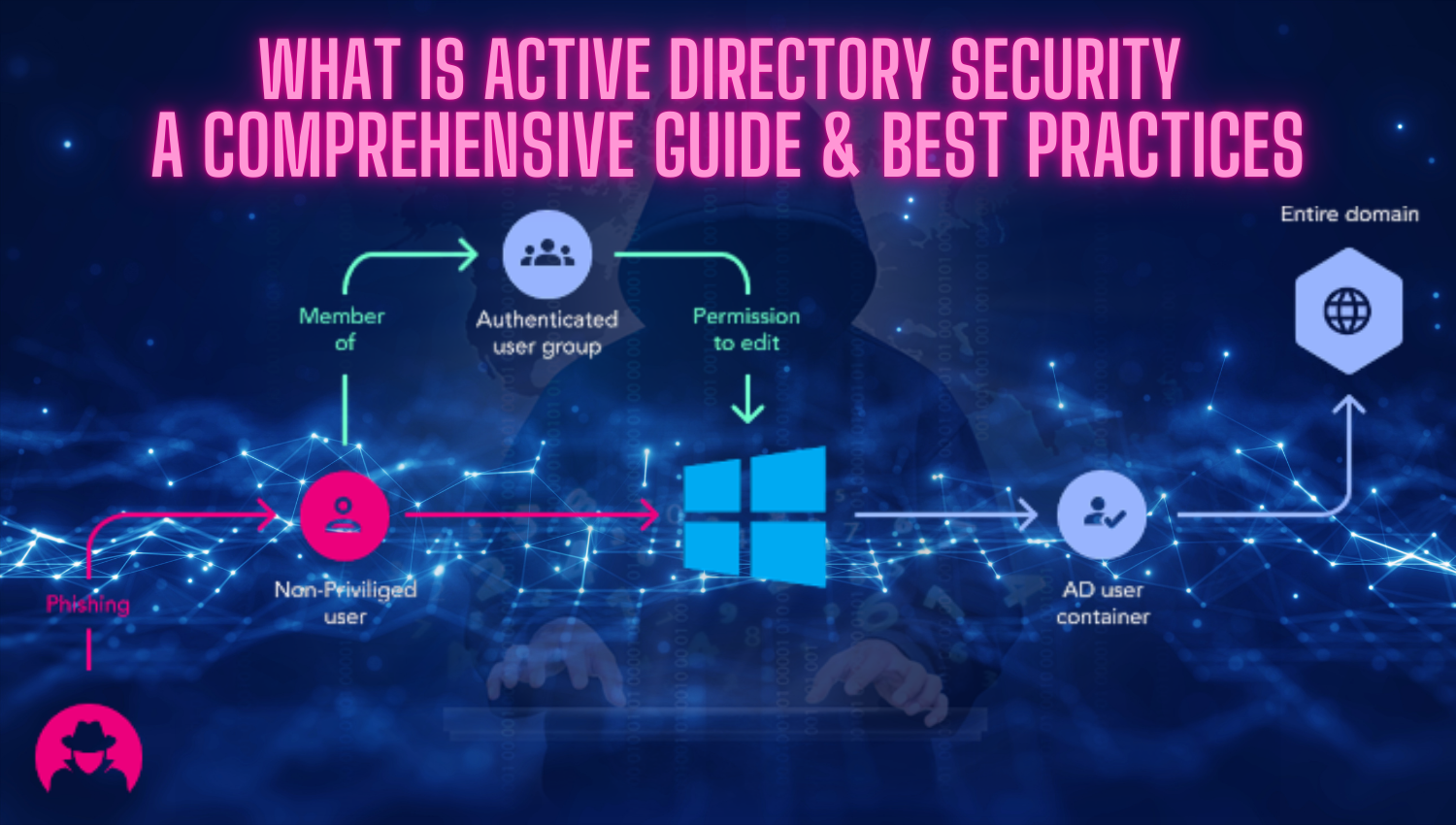
Cybersecurity Interview Questions and Answer Tips
Introduction Cybersecurity stands out as one of the world’s fastest-growing and most crucial career fields in today’s technology-driven environment. With the rapid integration of digital systems across every industry, the need for skilled security professionals has grown beyond specialist IT departments to become a foundational element in business strategies and national infrastructures. According to the World Economic Forum’s