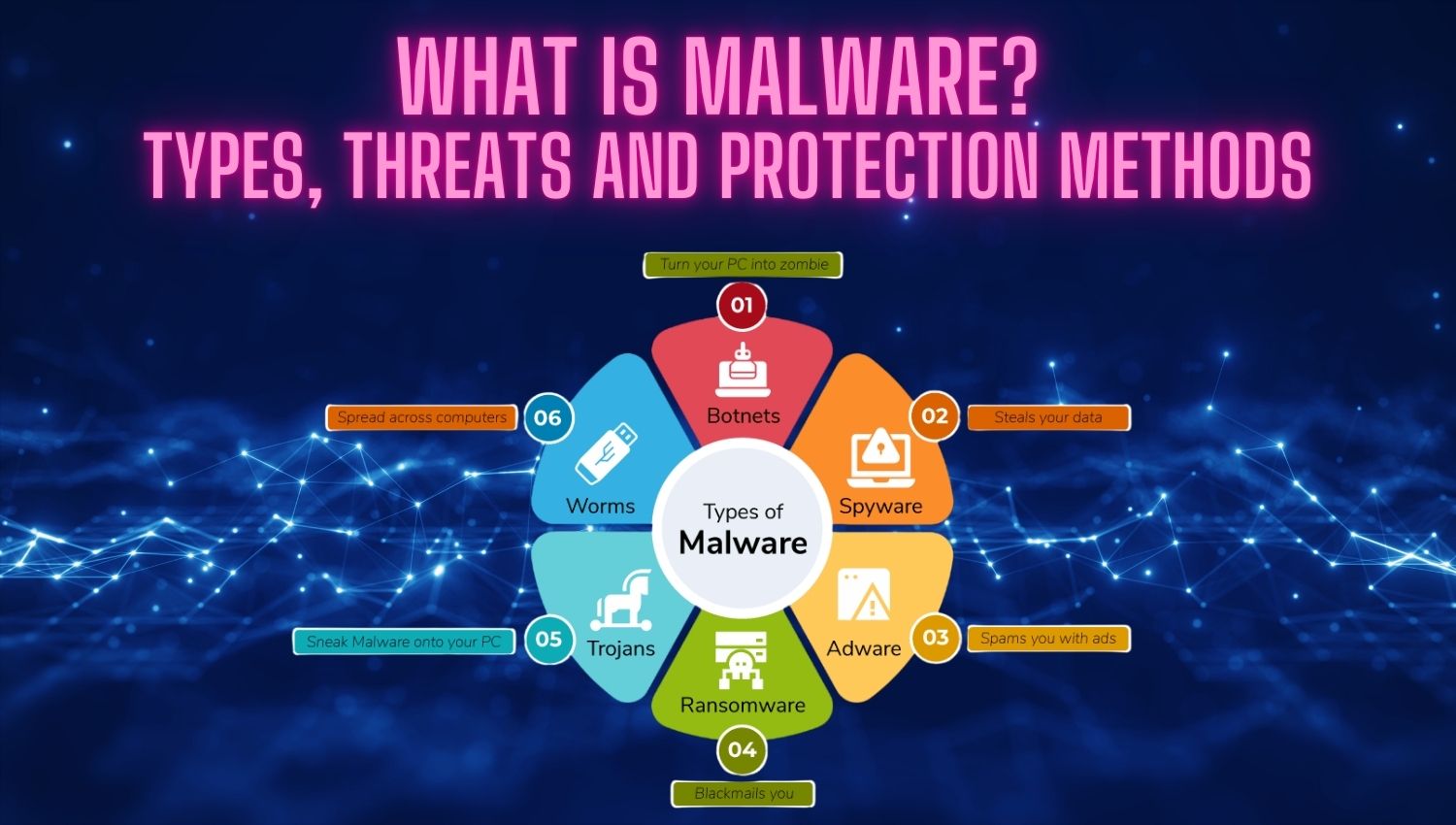
What is Cyber Threat Intelligence: A Comprehensive Guide
Introduction In today’s digital landscape, cyber threats are evolving more rapidly than ever, presenting serious challenges for organizations and individuals alike. As technology advances and our reliance on digital systems grows, attackers are constantly developing new and more sophisticated methods to breach defenses, steal information, and disrupt operations. Traditional security tools and reactive approaches are no longer sufficient to keep pace with