
Introduction
As the backbone of modern IT infrastructures, Linux is essential for network administrators, security professionals, and anyone involved in managing or securing systems. This powerful operating system is known for its stability, flexibility, and extensive security features, making it a top choice for running secure and scalable networks. “Mastering Linux Networking and Security: Essential and Advanced Techniques” is a comprehensive guide crafted to take you from foundational networking concepts to advanced security configurations in a structured and hands-on approach.
With this book, you’ll gain the knowledge and skills to configure, manage, and secure Linux-based networks, equipping you to handle both day-to-day tasks and advanced troubleshooting.
Read: Linux Network Basics: An Introduction to Network Management
Learning Objectives
By the end of “Mastering Linux Networking and Security,” you will:
- Understand fundamental networking concepts like IP addressing, subnetting, and network protocols.
- Configure and manage DNS, DHCP, and routing in Linux environments.
- Secure Linux servers using firewalls (iptables, ufw) and advanced network security tools.
- Set up secure communication channels via SSH, VPN, and SSL/TLS.
- Monitor network traffic to detect and respond to security incidents in real-time.
- Harden network services such as FTP/SFTP, VoIP, and wireless networks against attacks.
- Conduct security audits, penetration tests, and vulnerability assessments for robust security.
Why Master Linux Networking and Security?
In today’s digital landscape, Linux is not just an operating system; it is a foundation for cloud servers, enterprise networks, and cybersecurity defenses. Mastering Linux for networking and security enables you to manage complex systems, secure critical infrastructure, and ensure business continuity by protecting against cyber threats. This book combines theory with practical application, making it suitable for professionals looking to expand their skillset or students preparing to enter the IT industry.
What Will You Learn?
This book is organized into 30 chapters, each dedicated to a critical aspect of Linux networking and security. Topics include:
- Networking Fundamentals: Start with essential concepts like IP addressing, subnetting, and the OSI model, providing the foundation to understand data flow and communication in Linux networks.
- DNS and DHCP Configuration: Learn to set up and configure DNS and DHCP services, enabling you to handle IP address management, domain name resolutions, and network configuration efficiently.
- Routing and Network Bridges: Discover how to implement routing and network bridging to enable efficient data packet transfer within your network infrastructure, ensuring optimal communication paths.
- Firewall Configuration (iptables, ufw): Secure your network with iptables and ufw, two powerful Linux firewalls. Learn how to filter traffic, create rules, and block unauthorized access to protect your system.
- SSH and Remote Access Security: Set up SSH for secure remote access, and learn to configure public key authentication, port forwarding, and other security measures to prevent unauthorized access.
- VPN Setup for Secure Communication: Establish a VPN to create encrypted tunnels, protecting data as it travels across public networks. This chapter covers VPN setup, configuration, and management in Linux.
- SSL/TLS for Data Encryption: Learn to implement SSL/TLS protocols for encrypting data, ensuring secure communication between clients and servers, and protecting sensitive information from eavesdropping.
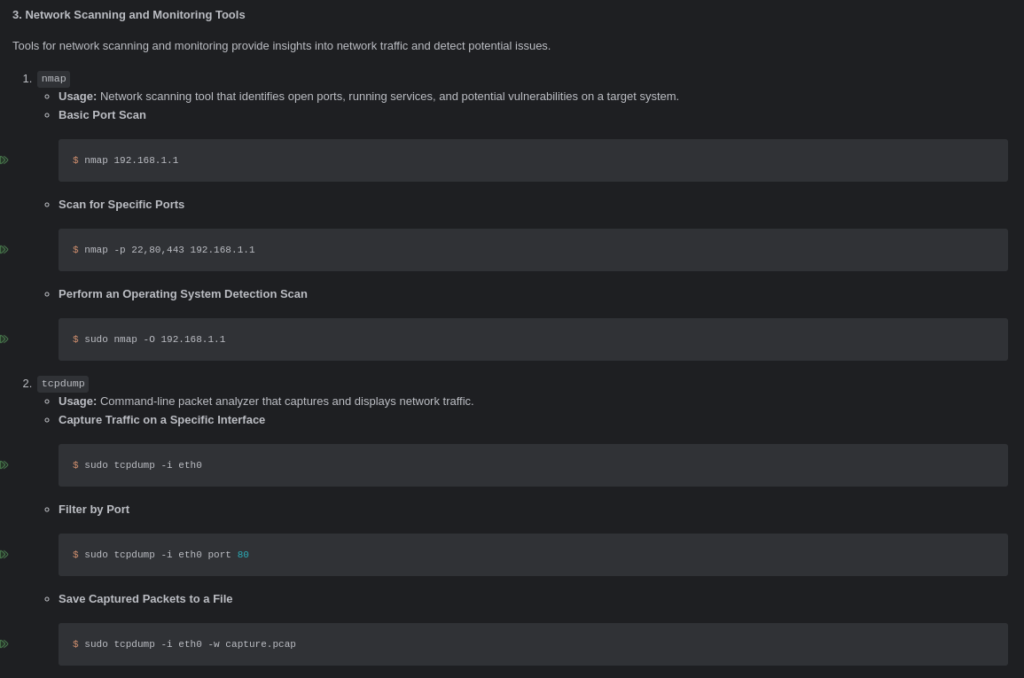
- Network Traffic Monitoring and Analysis: Use tools like Wireshark, tcpdump, and nmap to monitor network traffic, analyze packet flow, and identify anomalies. This section teaches you to detect potential intrusions and prevent attacks.
- Intrusion Detection and Prevention Systems (IDS/IPS): Implement IDS and IPS to detect and respond to unauthorized access and malicious activity on your network, enhancing your defense mechanisms.
- Security for Network Services (FTP/SFTP, VoIP, Wireless): Configure FTP/SFTP for secure file transfers, VoIP for voice communication, and wireless networks to minimize vulnerabilities and protect these essential services.
- Advanced Troubleshooting Techniques: Learn troubleshooting methods for network issues, including packet analysis, latency testing, and diagnostic tools, helping you quickly resolve connectivity issues.
- Conducting Security Audits and Vulnerability Assessments: Perform security audits to assess vulnerabilities, harden Linux systems, and prepare against potential threats. This section covers audit tools, methodology, and best practices.
- Linux Firewall Advanced Configurations: Dive deeper into firewall configurations to manage complex scenarios, including NAT, port forwarding, and custom filtering rules for unique security needs.
- Real-World Case Studies and Projects: Apply your skills in real-world scenarios through projects that demonstrate common security issues and how to tackle them using Linux tools. This hands-on approach reinforces the concepts covered throughout the book.
Who Is This Book For?
This book is designed to serve a diverse range of professionals and learners, each with unique needs and goals within the field of Linux networking and security. Whether you’re managing a corporate network, securing a personal server, or building your foundation in cybersecurity, this comprehensive guide has something valuable to offer. Here’s a closer look at who will benefit most:
- Network Administrators: In today’s digital landscape, network administrators need more than just basic knowledge of Linux. This book provides them with in-depth insights into managing, configuring, and securing Linux-based networks, equipping them with essential skills in setting up robust firewalls, monitoring network traffic, configuring VPNs, and troubleshooting network issues. By mastering these tools and techniques, network administrators can significantly enhance their ability to prevent and mitigate network breaches, ensuring reliable and secure connectivity across their organization.
- Cybersecurity Professionals: For those working on the front lines of security, this book is an essential toolkit. It offers cybersecurity experts the advanced methods and tools they need to detect and respond to potential threats. From learning about Intrusion Detection and Prevention Systems (IDS/IPS) to configuring secure remote access and performing regular security audits, this guide dives into advanced security strategies specifically tailored for Linux environments. Professionals will also find practical insights into the latest security tools like Wireshark, tcpdump, and iptables, empowering them to harden network defenses against modern attacks.
- IT Students and Enthusiasts: Those starting their journey in IT or cybersecurity will find this book invaluable as it builds a solid foundation in Linux networking and security. The book breaks down complex concepts into understandable segments, ensuring that students can follow along and apply what they learn. From understanding the basics of IP addressing and the OSI model to learning more advanced skills like network traffic analysis and VPN setup, this guide provides the practical knowledge and hands-on experience needed to advance in the IT field. It’s perfect for students in formal education programs, self-learners, and hobbyists looking to deepen their skills and improve their career prospects.
- System Administrators: For system administrators tasked with managing and securing Linux servers, this book is a comprehensive manual that addresses the security needs of today’s enterprise environments. The chapters on firewall configuration, secure communication (SSH, VPN), and network monitoring are designed to help administrators maintain optimal server performance while ensuring system integrity. With clear explanations on security best practices and practical advice for hardening Linux servers, system administrators will gain the expertise to effectively protect critical infrastructure, detect suspicious activity, and manage secure data transfer across networks.
Whether you are aiming to secure an entire organizational network or simply enhance your understanding of Linux for personal use, “Mastering Linux Networking and Security: Essential and Advanced Techniques” provides the practical tools, methodologies, and insights necessary to excel in the fast-evolving field of network security.
Why You Should Read This Book
Mastering Linux Networking and Security offers more than just a guide to configuring Linux servers; it delves into the core principles that underlie secure network infrastructures. In an era where data breaches and cyber threats are on the rise, understanding how to protect and optimize Linux-based systems is invaluable. This book goes beyond introductory material, focusing on advanced configurations, security protocols, and hands-on solutions that empower professionals to create resilient networks.
With its blend of theory, practical skills, and advanced techniques, this book provides a complete roadmap for anyone looking to advance in network security. Each chapter is crafted to build your expertise step-by-step, using clear explanations, visual aids, and examples to demonstrate how real-world networks operate and how they can be protected effectively. Through detailed case studies, you’ll gain insights into the challenges faced in real environments, allowing you to see how security principles are applied to solve complex problems. The inclusion of projects also ensures that you gain practical experience, reinforcing your understanding and giving you the confidence to tackle real-world scenarios on your own.
Get Your Copy Today
Don’t miss the opportunity to elevate your Linux networking and security skills with “Mastering Linux Networking and Security: Essential and Advanced Techniques.” Whether you’re aiming to secure your own networks or seeking a solid foundation for career advancement, this book provides the expertise you need to succeed. Support my work and gain access to this essential resource by visiting BuyMeACoffee.
