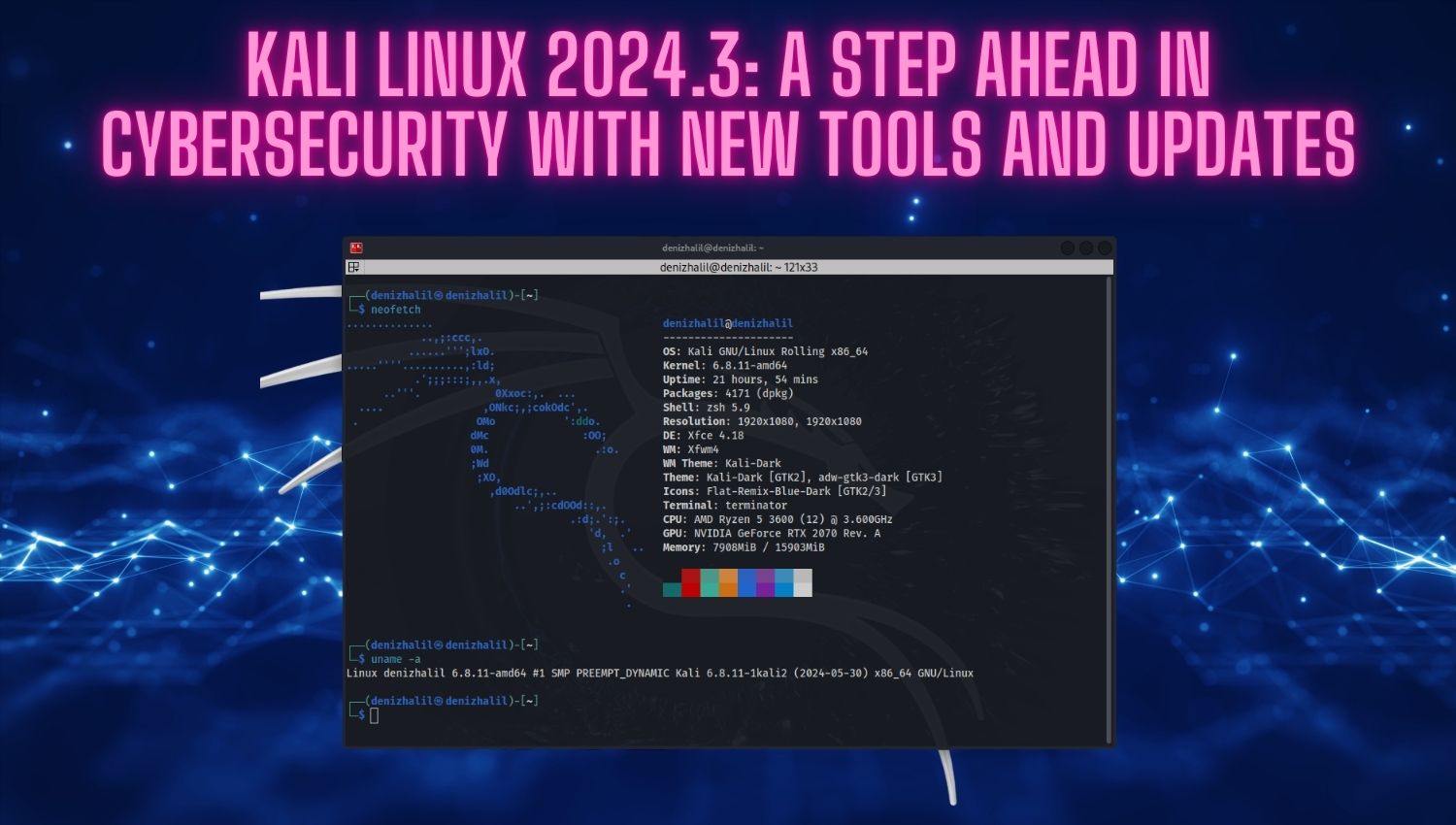
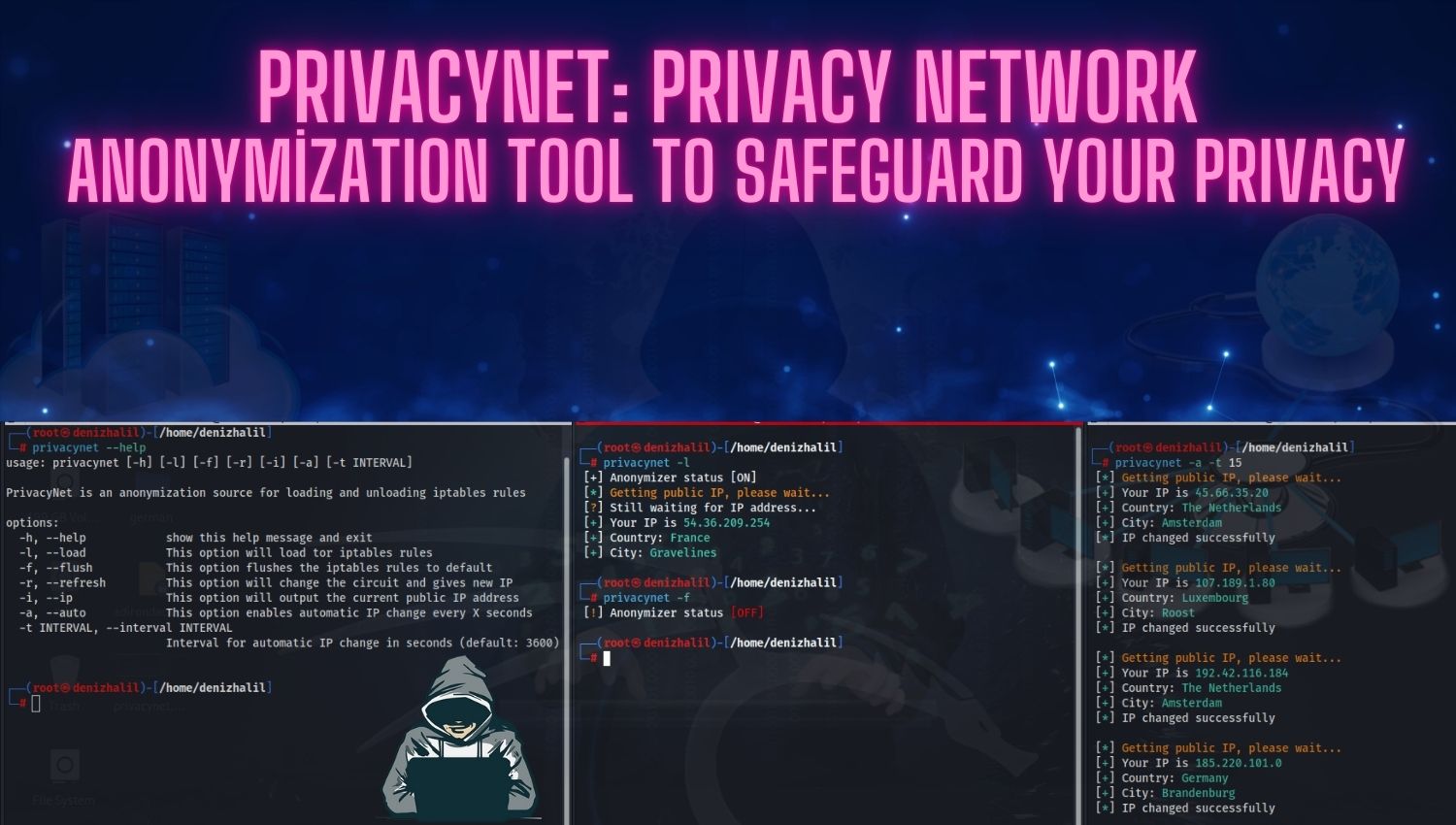
The Top Popular Hacker Operating Systems for Security
Introduction In the fast-paced world of cybersecurity, hackers continuously seek innovative tools and platforms to achieve their objectives. Hacker operating systems play a vital role in providing the necessary resources and capabilities for these individuals. In this article, we will explore the top eight popular hacker operating systems that have gained prominence due to their advanced features and robust