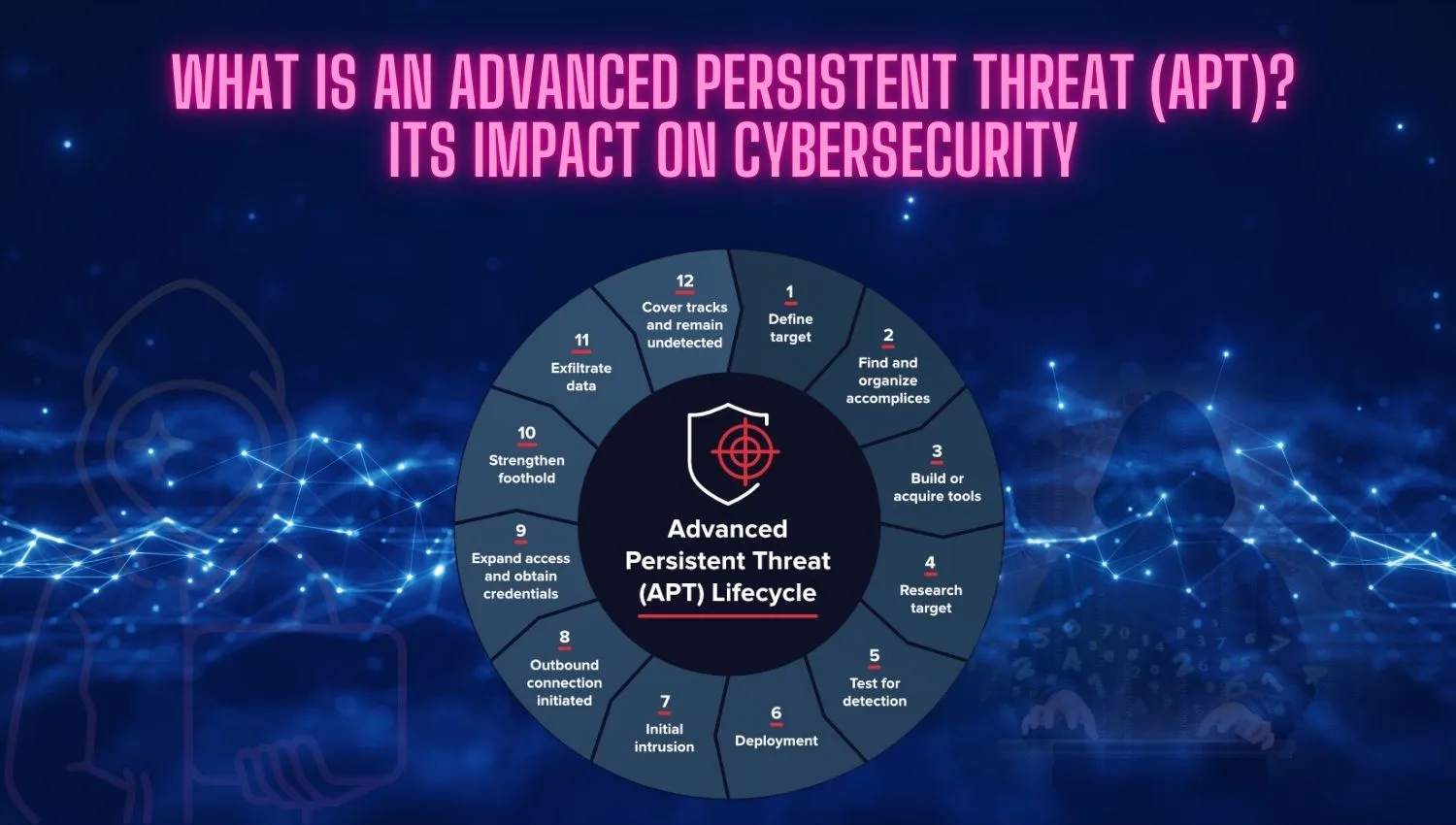
Beginner-Level Cybersecurity Certifications: Step in Your Career
Introduction: Cybersecurity has rapidly become a growing and evolving field, driven by increasing threats in the digital world. For those looking to pursue a career in this domain, beginner-level certifications serve as a critical step in acquiring fundamental knowledge and skills. These certifications are recognized by employers and provide individuals with the expertise needed to establish confidence in their