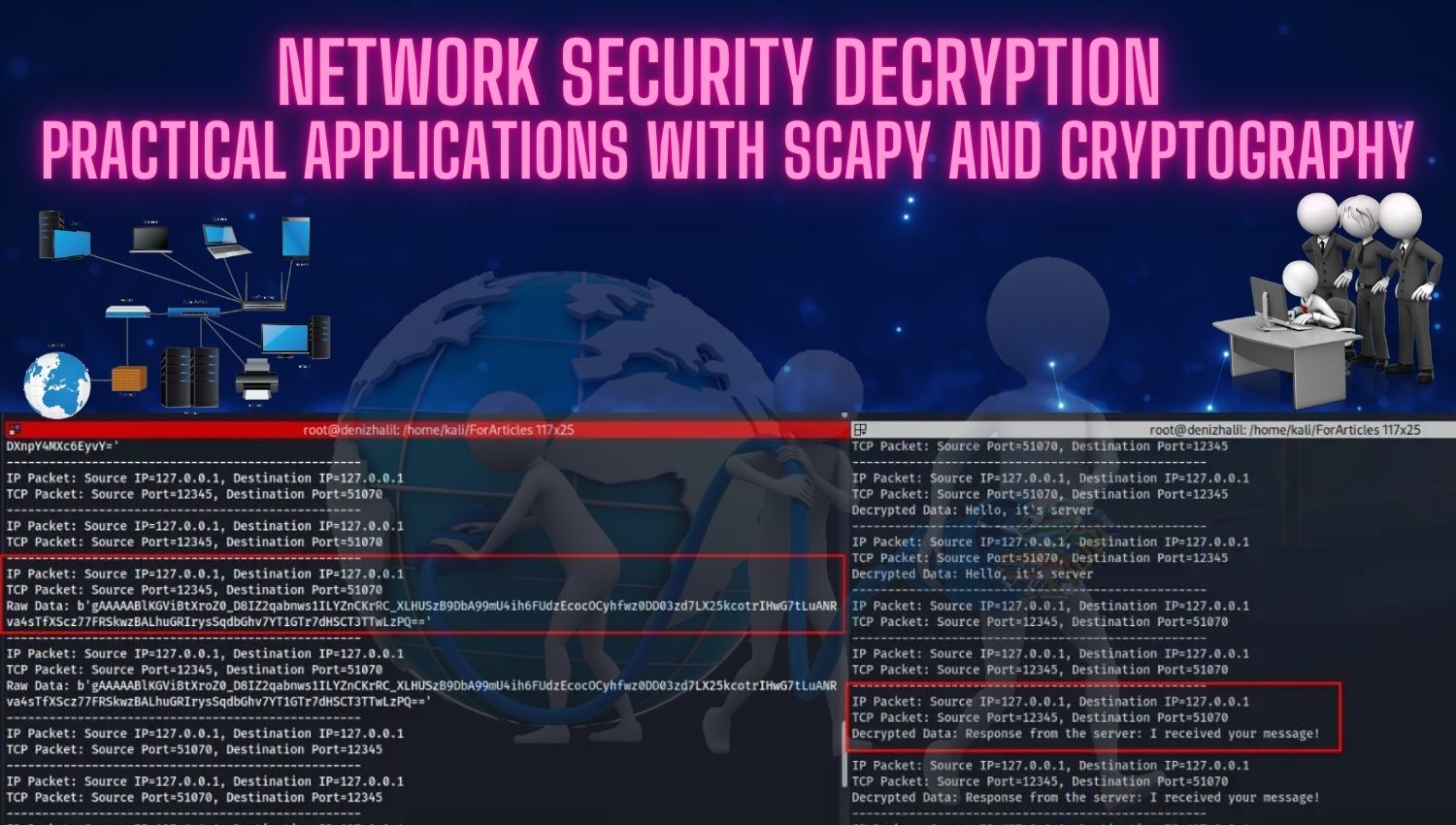
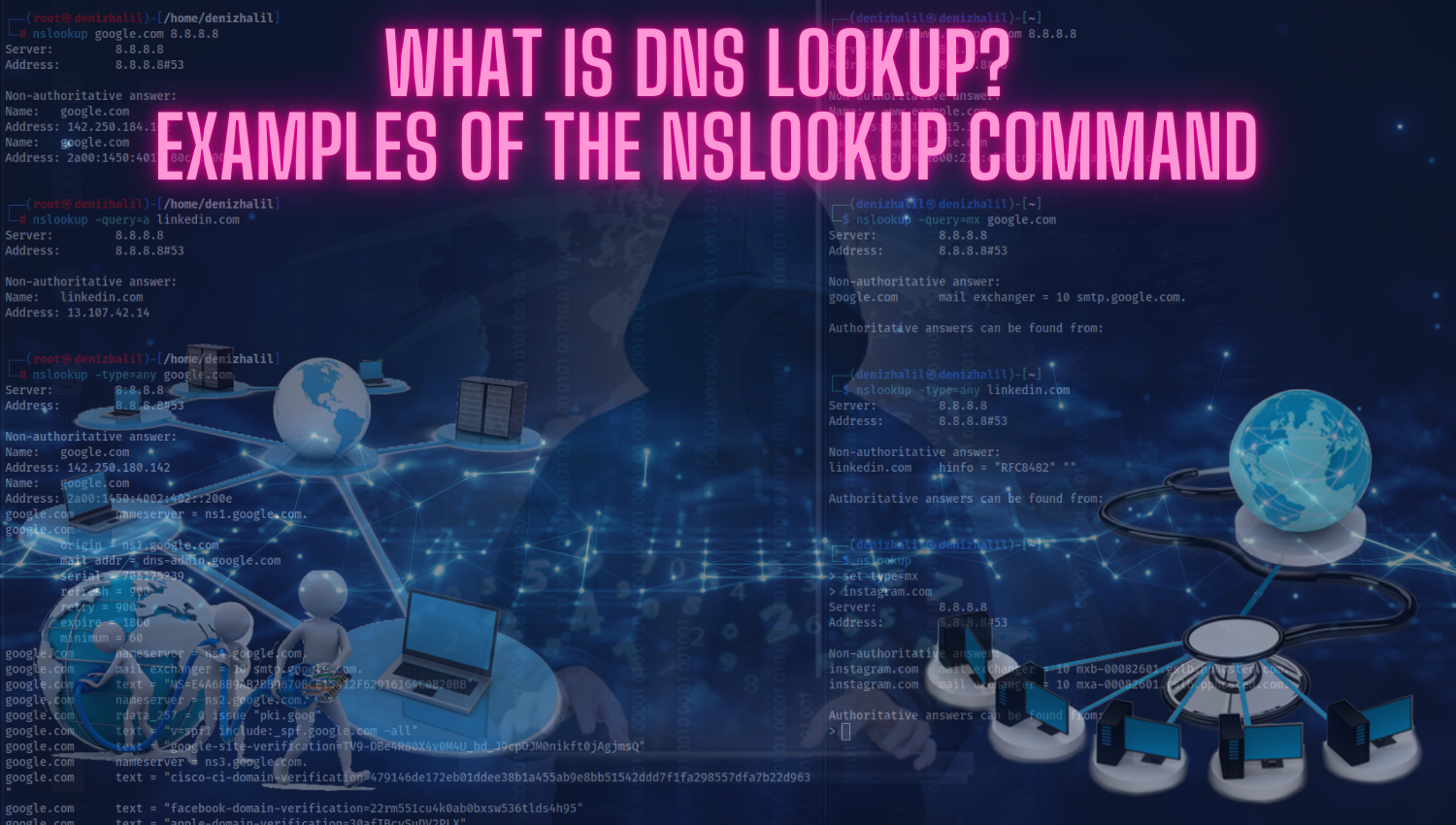
What is Spear Phishing and How Can We Protect Ourselves?
Introduction: In the realm of cybersecurity, terms like phishing and spear phishing frequently arise. Phishing is a type of cyberattack that generally targets internet users to steal their personal information. However, spear phishing is a more specialized and targeted form of attack. In this article, we will explore what spear phishing is, how it works, and how we can protect ourselves from such