Introduction
The Domain Name System (DNS) is an essential component of internet infrastructure, translating human-readable domain names into IP addresses. Understanding how DNS works and being able to enumerate DNS records can provide crucial information for both system administrators and ethical hackers. In this article, we will develop a simple DNS enumeration tool in Python that queries different DNS record types (such as A, MX, and TXT) for a domain name provided by the user. The tool will be implemented within a class structure, take advantage of the argparse library for command-line input, and use colorama to make the output visually informative.
Learning Objectives
After reading this article, you will learn:
- The basic principles of DNS and why it is important
- How to perform DNS queries using Python
- How to capture user input with Python’s
argparse - How to add color to terminal output using
colorama - How to structure a Python application using classes
Purpose of This Project
The purpose of this project is to build a practical DNS enumeration tool that can be used to gather valuable information about a domain by querying its DNS records. This tool will not only help users understand the DNS records available for a given domain, but it will also demonstrate how Python can be used to build flexible and dynamic command-line tools using powerful libraries such as argparse, dnspython, and colorama. By the end of this project, you’ll have a better grasp of DNS record types and how to implement a class-based solution in Python.
Mastering Python for Ethical Hacking: A Comprehensive Guide to Building 50 Hacking Tools
Let’s embark on this journey together, where you will learn to use Python not just as a programming language, but as a powerful weapon in the fight against cyber threats
-5% $25 on buymeacoffeeLet’s Start Coding
Now, let’s break down the tool step by step to understand how each part works.
Setting Up the Environment:
Before starting, you need to install the required libraries using the following commands in your terminal:
pip install dnspython colorama- dnspython: A powerful DNS toolkit for querying DNS records.
- colorama: Used for adding color to the terminal output for better readability.
1. Importing the Libraries
import argparse
import dns.resolver
from colorama import Fore, Style, init- argparse: This module helps us capture command-line arguments. In our case, we will use it to take the domain name input from the user.
- dns.resolver: Part of the dnspython library, it is used to query DNS records.
- colorama: Provides colored output to the terminal to differentiate between errors, warnings, and normal output.
2. Defining the DNSEnumerator Class And Initializing
# Initialize colorama
init(autoreset=True)
class DNSEnumerator:
def __init__(self, domain):
self.domain = domain- class DNSEnumerator: This defines a class called
DNSEnumerator. Classes help organize the code better and allow for easier extension in the future. - init method: This is the constructor of the class, which initializes the
domainvariable. The domain is passed when an instance of the class is created. - init(autoreset=True): Initializes colorama and sets it to automatically reset colors after each line. This means you don’t have to manually reset colors after using them, ensuring the text after colored output isn’t affected.
3. Enumerating DNS Records
def enumerate_records(self):
try:
print(Fore.CYAN + f"[*] Enumerating DNS records for: {self.domain}\n")
self.query_dns_record('A')
self.query_dns_record('AAAA')
self.query_dns_record('MX')
self.query_dns_record('NS')
self.query_dns_record('TXT')
self.query_dns_record('CNAME')
except Exception as e:
print(Fore.RED + f"[-] Error during DNS enumeration: {e}")- enumerate_records method: This method performs the DNS queries for different record types.
- Fore.CYAN: We use colorama’s
Fore.CYANto color the output in cyan when starting the enumeration. - query_dns_record: The tool checks for various DNS record types such as ‘A’, ‘AAAA’, ‘MX’, ‘NS’, ‘TXT’, and ‘CNAME’. Each type represents different information about the domain (e.g., A records map domain names to IPv4 addresses).
- try-except block: We use a try-except block to catch any exceptions that may occur during the DNS query process. If an error happens, it is printed in red with
Fore.RED.
5. Querying Specific DNS Records
def query_dns_record(self, record_type):
try:
print(Fore.YELLOW + f"\n[+] Querying {record_type} records:")
answers = dns.resolver.resolve(self.domain, record_type)
for answer in answers:
print(Fore.GREEN + f"{record_type} record: {answer}")
except dns.resolver.NoAnswer:
print(Fore.RED + f"[-] No {record_type} records found.")
except dns.resolver.NXDOMAIN:
print(Fore.RED + f"[-] Domain {self.domain} does not exist.")
except dns.resolver.Timeout:
print(Fore.RED + f"[-] Query timed out.")- query_dns_record method: This method takes a
record_typeas input (e.g., A, MX, TXT) and queries the DNS records for the provided domain. The results are printed in green withFore.GREEN. - Fore.YELLOW: The query process for each record type is printed in yellow to indicate that the query is ongoing.
- NoAnswer: If no DNS records are found for the given record type, the output is printed in red.
- NXDOMAIN: If the domain name doesn’t exist, an error is printed in red.
- Timeout: If the query takes too long, a timeout message is printed.
6. Main Function And Creating an Instance of DNSEnumerator
def main():
parser = argparse.ArgumentParser(description="DNS Enumeration Tool")
parser.add_argument("domain", help="Domain name to enumerate")
args = parser.parse_args()
enumerator = DNSEnumerator(args.domain)
enumerator.enumerate_records()- argparse setup: Here we use
argparse.ArgumentParserto define the command-line interface. Thedomainargument is required and will be provided by the user when running the script. - enumerator = DNSEnumerator(args.domain): This line creates an instance of the
DNSEnumeratorclass with the domain name provided by the user as a command-line argument. - enumerate_records(): This method is called to start the DNS enumeration for the given domain.
Mastering Scapy: A Comprehensive Guide to Network Analysis
Mastering Network Analysis with Scapy” is not just about learning a tool; it’s about unlocking a deeper understanding of the digital world that surrounds us
-5% $20 on buymeacoffee7. Running the Script
if __name__ == "__main__":
main()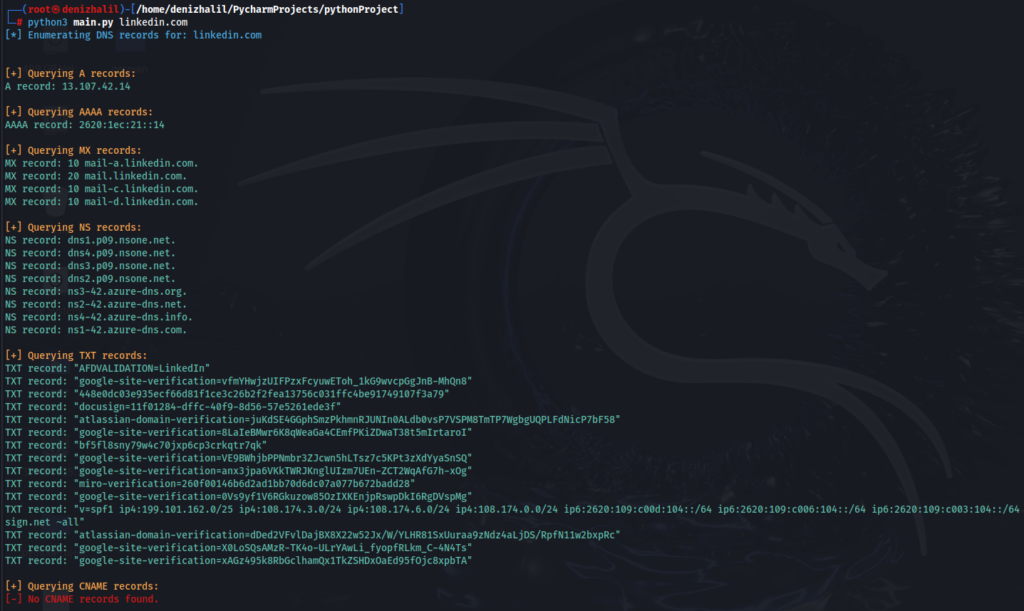
Conclusion
By completing this project, we have successfully created a DNS enumeration tool that can query multiple DNS records for a given domain name. Using argparse, we made the tool flexible by allowing users to provide domain names via the command line. Additionally, colorama enabled us to format the terminal output in a more readable and visually appealing way. This project not only strengthens your understanding of DNS but also improves your ability to build Python tools with dynamic user input and colorful terminal output.




This tool is a fantastic resource for quickly and easily querying DNS records, and the guide is well-structured. Anyone with basic DNS knowledge can follow and understand this code.
I only want to query a specific type of DNS record. How can I modify the code?
You can add an option in argparse to let users specify which record type to query:
This lets the user select the record type they’re interested in.
thank you so much and Is it possible to query multiple domains simultaneously?
Yes, you can capture a list of domains in argparse using the nargs option, and then loop through each domain.
This way, the user can enter multiple domains, and the tool will query each one in sequence.
What if I encounter a network error during DNS queries?
The try-except blocks in the code capture network or timeout errors, displaying error messages so that you can quickly identify any issues during execution.
Adding colors to the output using colorama makes errors and information much clearer. This is a really eye-catching feature!