Introduction
In today’s digital landscape, where cyber threats are becoming increasingly sophisticated and prevalent, maintaining robust network security is more important than ever. Organizations face constant challenges in protecting their sensitive data from malicious actors who exploit vulnerabilities in network infrastructures. The Network Compromise Assessment Tool is specifically designed to address these challenges by analyzing pcap files to detect potential suspicious network traffic. By focusing on identifying abnormal activities and searching for suspicious keywords, this tool serves as a vital asset for cybersecurity professionals engaged in network penetration testing and overall computer security.
Learning Objectives
By engaging with this document, you will:
- Understand the core functionalities and objectives of the NetworkAssessment project.
- Learn how to effectively utilize the tool for assessing network vulnerabilities.
- Familiarize yourself with the key features that enhance its capability in detecting network threats.
- Gain insights into proper installation and usage of the tool.
What is the NetworkAssessment Project?
The NetworkAssessment project is a powerful utility aimed at enhancing network security by providing a thorough analysis of captured network packets. It assists security analysts, network administrators, and IT professionals in identifying vulnerabilities, detecting potential compromises, and ensuring the integrity of their networks. By focusing on abnormal patterns in network traffic, the tool empowers users to take proactive measures against cyber threats.
The project is particularly valuable for organizations that need to conduct regular assessments of their network environments. With the rise of remote work and cloud computing, understanding network behavior has become critical. NetworkAssessment provides insights that can help organizations maintain compliance with industry regulations and best practices.
How Does NetworkAssessment Work?
NetworkAssessment functions by examining pcap files, which contain packet data from network traffic. The tool employs a variety of detection algorithms to identify suspicious activities, including:
- DNS Tunneling: Attackers often use DNS tunneling to exfiltrate data or establish covert communication channels. The tool detects such anomalies by analyzing DNS queries and responses, alerting users to potential data exfiltration attempts.
- SSH Tunneling: SSH sessions can be misused to bypass network restrictions or obscure malicious activities. NetworkAssessment identifies these sessions by monitoring SSH traffic patterns and flagging any unusual behavior.
- TCP Session Hijacking: Unauthorized takeover of TCP sessions can lead to significant security breaches. The tool monitors for signs of session hijacking attempts by analyzing TCP packets for anomalies that indicate unauthorized access or control.
Through these mechanisms, the tool provides a detailed overview of network activity and highlights areas that may require further investigation. This proactive approach allows organizations to respond swiftly to potential threats before they escalate into serious incidents.
Key Features of NetworkAssessment
The NetworkAssessment tool boasts several key features that enhance its effectiveness in detecting and analyzing network threats:
- DNS Tunneling Detection: Identifies covert communication channels over DNS, providing alerts for potential data exfiltration attempts that could compromise sensitive information.
- SSH Tunneling Detection: Spots signs of SSH sessions that may be used to cloak malicious activities or bypass network controls, ensuring that all communication is legitimate and authorized.
- TCP Session Hijacking Identification: Monitors for suspicious TCP sessions that might indicate unauthorized access or control, allowing administrators to take immediate action against potential intrusions.
- Various Attack Signatures: Recognizes indicators of common attacks such as SYN flood, UDP flood, Slowloris, and SMB attacks. This feature helps security teams understand the threat landscape and prepare appropriate defenses.
- Suspicious Keyword Search: Actively scans network traffic for user-defined keywords that could indicate malicious intent or sensitive data leakage. This capability is particularly useful for organizations handling confidential information.
- Protocol-Specific Scanning: Users can specify which protocols to monitor (e.g., TCP, UDP), allowing for focused and efficient analysis tailored to specific needs. This flexibility enables users to concentrate on areas most relevant to their security posture.
- Output Logging: Provides an option to save detailed analysis results to a file for further investigation or record-keeping. This feature enhances accountability and traceability in security assessments.
- IPv6 Fragmentation Attack Detection: Detects potential attempts to exploit fragmentation mechanisms in IPv6 networks, ensuring comprehensive coverage in modern environments where IPv6 adoption is increasing.
- User-Friendly Display: The tool features color-coded outputs and progress indicators that enhance readability and user experience. This design consideration makes it accessible even for those new to packet analysis.
Downloading NetworkAssessment from GitHub
To get started with NetworkAssessment, you can easily download it from GitHub. Follow these steps:
1. Clone the repository using the following command:
git clone https://github.com/HalilDeniz/NetworkAssessment.git2. Navigate into the project directory:
cd NetworkAssessment/3. Install the required dependencies using pip:
pip install -r requirements.txtThis straightforward installation process ensures that you have everything you need to begin analyzing your network traffic effectively.
Example Usage of NetworkAssessment
Once installed, you can run the tool using the following command structure:
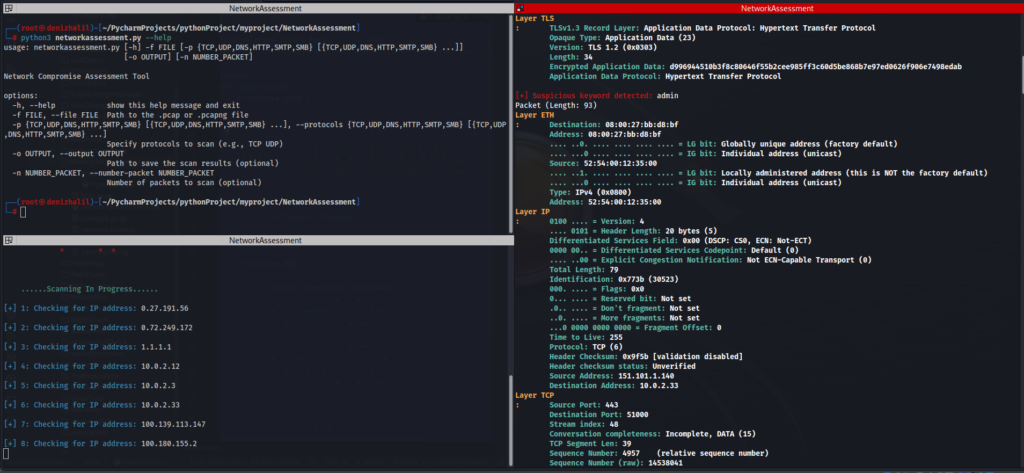
└─$ python3 networkassessment.py --help
usage: networkassessment.py [-h] -f FILE
[-p {TCP,UDP,DNS,HTTP,SMTP,SMB} [{TCP,UDP,DNS,HTTP,SMTP,SMB} ...]]
[-o OUTPUT] [-n NUMBER_PACKET]
Network Compromise Assessment Tool
options:
-h, --help show this help message and exit
-f FILE, --file FILE Path to the .pcap or .pcapng file
-p {TCP,UDP,DNS,HTTP,SMTP,SMB} [{TCP,UDP,DNS,HTTP,SMTP,SMB} ...], --protocols {TCP,UDP,DNS,HTTP,SMTP,SMB} [{TCP,UDP,DNS,HTTP,SMTP,SMB} ...]
Specify protocols to scan (e.g., TCP UDP)
-o OUTPUT, --output OUTPUT
Path to save the scan results (optional)
-n NUMBER_PACKET, --number-packet NUMBER_PACKET
Number of packets to scan (optional)Parameters Explained:
-for--file: This parameter specifies the path to the.pcapor.pcapngfile you wish to analyze (mandatory). This file contains the captured network traffic data that will be scrutinized by the tool.-por--protocols: Here you can specify which protocols you want to scan (optional). You can mention multiple protocols from options like “TCP”, “UDP”, “DNS”, “HTTP”, “SMTP”, “SMB”. This allows for targeted analysis based on your specific concerns.-oor--output: This optional parameter allows you to define a path where the scan results will be saved. Having a record of your findings can be invaluable for future reference.-nor--number-packet: Use this parameter to specify how many packets you want to scan from the provided file (optional). If not specified, all packets will be analyzed. This flexibility allows users to focus their analysis on specific segments of traffic if desired.
For example, if you want to analyze the first 1000 packets from a file named sample.pcap, focusing on TCP and UDP protocols while saving results to output.txt, you would use:
python3 networkassessment.py -f sample.pcap -p TCP UDP -n 1000 -o output.txtThis command will trigger an analysis that focuses on just those protocols within a specified packet limit, making it efficient for users with large datasets.
About the Original Author
NetworkAssessment is a fork of an earlier project called Network_Assessment, originally created by Alperen Uğurlu. This updated version builds upon his foundational work while incorporating community contributions that enhance its detection capabilities. A heartfelt thanks goes out to Alperen Uğurlu for his inspiration and groundwork; without his efforts, this improved version would not have been possible. For more information about the original tool and its development history, visit the Network_Assessment repository.
Conclusion
The Network Compromise Assessment Tool stands as an essential resource for enhancing network security through effective analysis of network traffic. By leveraging its capabilities—ranging from detecting tunneling techniques to identifying session hijacking—cybersecurity professionals can better identify vulnerabilities and respond proactively to potential threats within their networks. As cyber threats continue to evolve rapidly, tools like NetworkAssessment play a crucial role in safeguarding our digital environments against malicious activities.
Investing time in understanding and implementing this tool can significantly bolster your organization’s defenses against cyber threats. Embrace this powerful resource today and fortify your defenses against an ever-changing threat landscape! Whether you’re a seasoned cybersecurity expert or just starting your journey into network security analysis, NetworkAssessment provides the tools necessary for effective monitoring and response strategies in today’s complex networking environments.
