Introduction
DoSinator is an advanced, open-source tool written in Python, designed specifically for cybersecurity professionals and researchers to simulate Denial of Service (DoS) attacks. In today’s digital landscape, where cyber threats are becoming increasingly sophisticated, testing the resilience of networks, systems, and applications is critical. DoSinator provides a realistic environment for such testing, enabling users to assess the robustness of their infrastructure against various types of DoS attacks. The tool is particularly valuable for identifying vulnerabilities that could lead to service disruptions. By leveraging DoSinator, security teams can proactively pinpoint weaknesses in their systems and implement measures to strengthen their defenses. This proactive approach helps mitigate risks associated with downtime, data breaches, and reputational damage caused by successful DoS attacks.
Moreover, DoSinator’s open-source nature makes it accessible to a wide audience while encouraging collaboration and innovation. Users can contribute to its development, ensuring the tool evolves alongside emerging cyber threats. This combination of accessibility and adaptability positions DoSinator as an essential resource in the cybersecurity toolkit.
Learning Objectives
- Understand the purpose and functionality of DoSinator.
- Learn how to download and set up the tool.
- Explore its key features and practical usage examples.
- Develop skills in simulating various DoS attack scenarios.
What is the DoSinator Project?
The DoSinator project was created with the goal of empowering cybersecurity experts and researchers by providing a versatile platform for testing system vulnerabilities against a variety of DoS attack scenarios. Unlike traditional tools that may focus on specific attack types, DoSinator supports multiple attack modes, making it highly adaptable to different testing needs. The project is hosted on GitHub, where it is freely available for ethical use. This accessibility ensures that organizations of all sizes can benefit from its capabilities without incurring significant costs. Additionally, the collaborative nature of open-source projects allows users to suggest improvements or report issues, fostering a community-driven approach to cybersecurity innovation.
DoSinator’s design emphasizes ease of use while maintaining powerful functionality. Users can simulate real-world attack scenarios by customizing parameters such as packet size, attack rate, and duration. This level of control enables precise testing tailored to specific network configurations or potential threat models. Furthermore, the tool’s ability to simulate diverse attack types—ranging from SYN Floods to ARP Flooding—ensures comprehensive coverage during testing. By using DoSinator, organizations can gain valuable insights into their systems’ resilience and take informed steps to enhance their security posture.
How Does DoSinator Work?
DoSinator operates by generating high volumes of network traffic or requests directed at a target system with the intent of overwhelming its resources. The tool supports various attack modes that exploit different aspects of network protocols or application vulnerabilities. For example:
- SYN Flood Attacks: Exploit the TCP handshake process by sending numerous connection requests without completing them.
- UDP Flood Attacks: Overload the target with User Datagram Protocol (UDP) packets.
- ICMP Flood Attacks: Use Internet Control Message Protocol (ICMP) packets (e.g., ping requests) to saturate network bandwidth.
- Slowloris Attacks: Keep many connections open by sending partial HTTP requests.
- ARP Flooding: Disrupt local network communication by flooding ARP tables with spoofed entries.
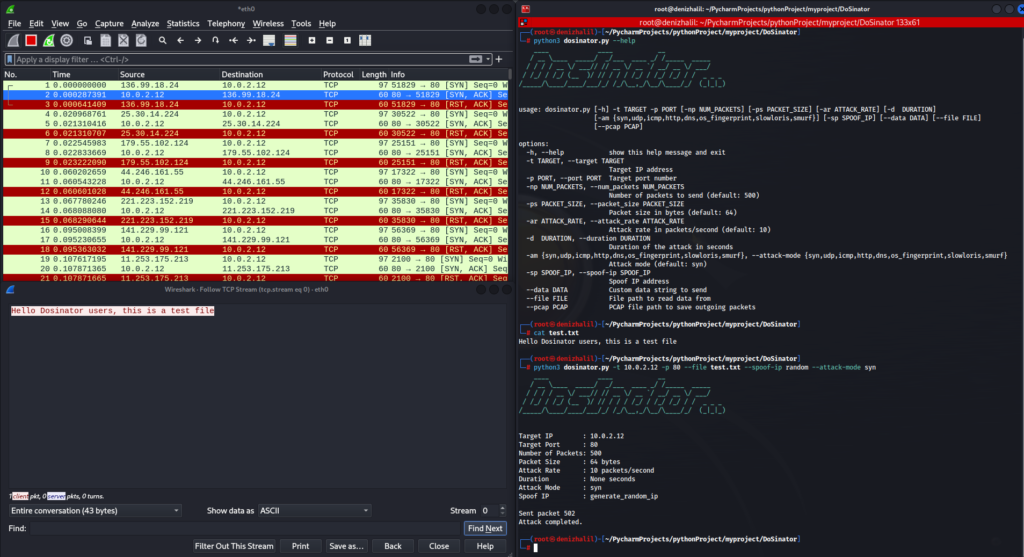
These options allow for fine-tuned simulations that mimic real-world attack conditions. Additionally, features like IP spoofing enable users to mask the source IP address during attacks, simulating scenarios where attackers attempt to remain anonymous. DoSinator also supports multithreaded packet sending, which ensures efficient use of system resources during high-intensity tests. Outgoing packets can be saved in PCAP format for further analysis using tools like Wireshark, providing detailed insights into attack behavior and system responses.
Key Features of DoSinator
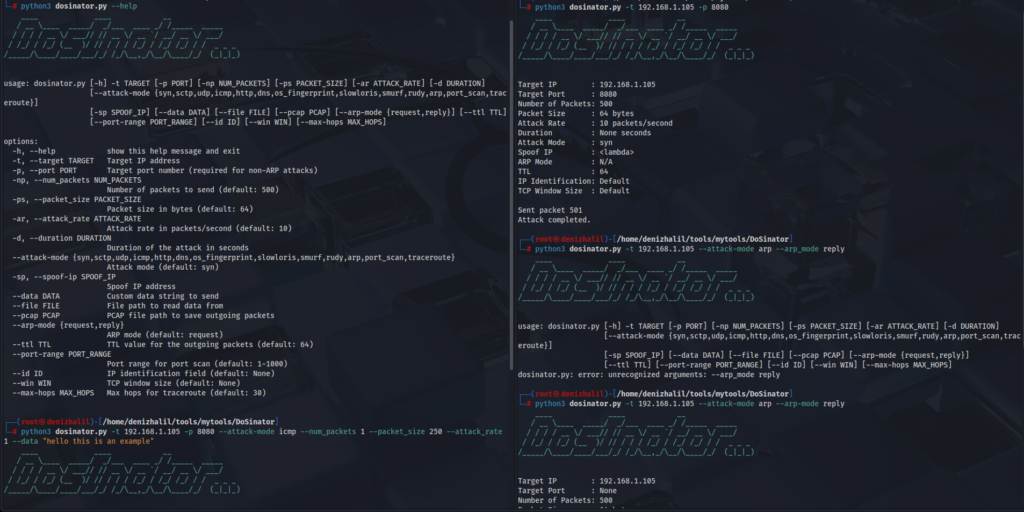
- Multiple Attack Modes: Includes SYN Flood, UDP Flood, ICMP Flood, OS Fingerprinting, Slowloris, Rudy, SCTP, Smurf, and ARP Flooding attacks. Each mode targets specific vulnerabilities in network protocols or application layers.
- Customizable Parameters: Adjust packet size, attack rate, and duration to tailor simulations according to specific needs.
- IP Spoofing: Mask the source IP address for anonymity during tests.
- Multithreaded Packet Sending: Utilize multiple threads for simultaneous packet transmission, maximizing efficiency.
- PCAP Output: Save outgoing packets in PCAP format for detailed post-test analysis.
- Data Injection: Load custom data from files into attack packets for specialized testing scenarios.
- ARP Flooding Support: Test local area networks by flooding ARP tables with spoofed entries.
These features make DoSinator a versatile tool capable of addressing a wide range of cybersecurity testing requirements. Whether assessing individual devices or entire networks, users can rely on its robust functionality to uncover potential vulnerabilities effectively.
Downloading DoSinator from GitHub
1. Clone the repository:
git clone https://github.com/HalilDeniz/DoSinator.git2. Navigate to the project directory:
cd DoSinator/3. Install dependencies:
pip install -r requirements.txtExample Usage of DoSinator
Here are several examples of how to use DoSinator to simulate various types of Denial of Service (DoS) attacks. Each example demonstrates different attack modes and configurations that can be tailored to specific testing scenarios.
- SYN Flood Attack
This attack targets the TCP handshake process by sending numerous connection requests without completing them, overwhelming the server.
python3 dosinator.py -t 192.168.1.1 -p 80 --attack-mode syn- UDP Flood Attack
This attack floods the target with UDP packets, consuming network bandwidth and server resources.
python3 dosinator.py -t 192.168.1.1 -p 53 --attack-mode udp- ICMP Flood Attack with IP Spoofing
This attack uses ICMP packets (e.g., ping requests) to flood the target while masking the source IP, making it harder to identify the attacker
python3 dosinator.py -t 192.168.1.1 --attack-mode icmp --spoof-ip random- HTTP Slowloris Attack
This attack keeps many connections open by sending partial HTTP requests, exhausting the target server’s resources.
python3 dosinator.py -t 192.168.1.2 -p 8080 --attack-mode slowloris --attack-rate 50 --duration 300- Smurf Attack
This attack exploits ICMP broadcast requests to flood a target with echo replies, consuming its network resources.
python3 dosinator.py -t 192.168.1.3 --attack-mode smurf --attack-rate 100 --duration 240- DNS Amplification Attack with Custom Data
This attack sends specially crafted DNS queries from a data file to amplify traffic directed at the target system
python3 dosinator.py -t 192.168.1.4 -p 53 --attack-mode dns --file dns_query.txt --attack-rate 300 --duration 150- ARP Request/Reply Flooding Attack
This attack floods the ARP table of a local network by sending a large number of ARP requests or reply to disrupt communication between devices
python3 dosinator.py -t 192.168.1.5 --attack-mode arp --arp-mode request/reply- Port Scanning Mode
Use DoSinator to scan for open ports on a target system and identify running services for further analysis or testing
python3 dosinator.py -t 192.168.1.7 --attack-mode port_scan --port-range 1-65535- Custom Packet Size and Rate SYN Flood
Simulate a SYN flood with specific packet sizes and rate configurations for more controlled testing
python3 dosinator.py -t 192.168.1.8 -p 443 --attack-mode syn --packet-size 128 --attack-rate 500- ICMP Ping Flood with High Volume
Overwhelm the target using a large number of ICMP echo request packets
python3 dosinator.py -t 192.168.1.9 --attack-mode icmp --num-packets 10000 --packet-size 56 --attack-rate 1000These examples demonstrate the flexibility and power of DoSinator in simulating diverse attack scenarios for testing purposes. Always ensure you have proper authorization before conducting any tests, as unauthorized use may lead to legal consequences or ethical violations.
Conclusion
DoSinator is a powerful and versatile tool attacks designed for testing the resilience of networks, systems, and applications against Denial of Service (DoS) attacks. Its wide range of attack simulations, including SYN Flood, UDP Flood, ICMP Flood, and Slowloris, makes it an essential resource for cybersecurity professionals. The tool’s customization options allow users to tailor attack parameters such as packet size, rate, and duration, enabling realistic testing scenarios that mimic potential real-world threats. Additionally, DoSinator’s ability to save outgoing packets in PCAP format for further analysis enhances its utility in understanding attack patterns and refining security measures. The open-source nature of the project fosters collaboration within the cybersecurity community, ensuring that the tool remains effective against evolving threats. However, it is crucial to use DoSinator ethically and with proper authorization to avoid legal repercussions. By conducting responsible testing, organizations can proactively strengthen their defenses and ensure their systems remain operational even under intense network stress. Ultimately, DoSinator serves as a valuable asset in the ongoing effort to enhance cybersecurity and protect against malicious attacks.
